Severity
High
Analysis Summary
The maritime and military-industrial sectors are two important areas of Pakistan's economy that the APT group DONOT has targeted. The DONOT threat group has successfully infiltrated sensitive infrastructure using sophisticated malware and focused social engineering techniques.
The APT group DONOT, also called APT-C-35, has been active since 2016 and is mostly known for its persistent cyber espionage efforts, according to the researchers. This threat group has historically targeted diplomatic missions, governmental organizations, and military installations, with a focus on South Asian nations. Its operations are distinguished by a high level of stealth, infiltrating target networks with the use of advanced malware and specially designed tools.
Using phishing emails and malicious attachments as initial infection vectors, the DONOT APT has previously targeted companies by taking advantage of flaws in military and government networks. But this time, they are concentrating on Pakistan's vital manufacturing sectors, which underpin the nation's defense and maritime industries. Due to the delicate nature of these industries, the attack has significant ramifications for national security and economic stability.
The new cyberattack focuses on a campaign that targets the factories that provide Pakistan's marine and defense industries with equipment. This focused strategy implies that the DONOT group is more concerned with collecting particular industrial and military intelligence than they are with obtaining broad access to networks. A malicious LNK file that was included in a spam email masquerading as a genuine Rich Text Format (RTF) document served as the campaign's first infection vector. The purpose of this LNK file was to trick the victim into opening it by making it look as though it contained encrypted data. When the file was clicked, it sent off a series of PowerShell commands that downloaded more malware, including a DLL file that served as a "stager" for subsequent attacks.
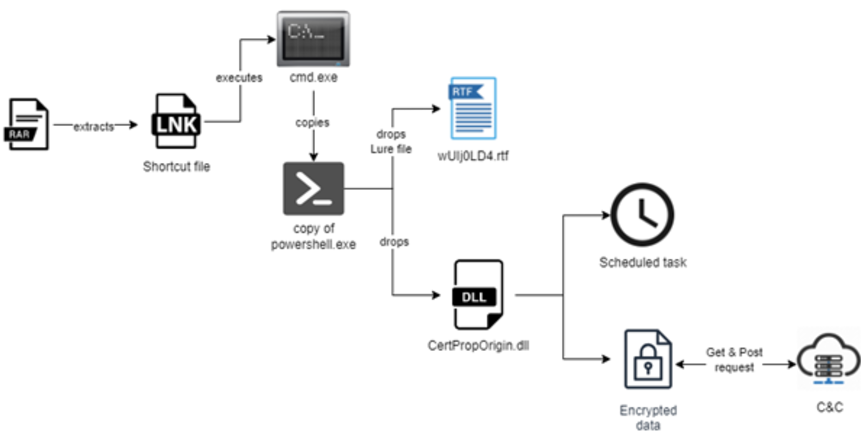
When the malicious LNK file was executed, it triggered a sequence of operations that downloaded and decrypted further payloads using PowerShell scripts. Following their deployment onto the compromised system, these payloads created a footing that enabled the malware to continue operating on the compromised system. The malware set up a task to run the payload every five minutes to keep access to the network. The highly sophisticated malware used in this attack by the DONOT uses a variety of encryption techniques to evade detection by conventional security measures. The group presented a brand-new way to communicate with command-and-control (C2) servers. The malware obfuscates its communications using Base64 encoding and AES encryption, making it more challenging for security software to detect malicious activities.
After establishing its presence, the malware sent a unique device ID to the principal C2 server via a POST request to authenticate the compromised system. The malware would download further payloads, set up the machine for persistence, and prepare for more attack phases if the C2 server responded positively. DONOT used random domain generation for backup C2 servers in addition to encrypting communications between the target computer and the C2 server. This tactic guarantees that the infection can continue to function through alternative, dynamically formed domains even if the principal server is knocked down.
A PowerShell script concealed within the LNK file is executed to start the malicious process. This script uses a straightforward XOR method to decrypt the DLL payload and the lure RTF file. After that, the files are extracted to the temporary location of the victim. To further attract the user, the malware reads the bait document after extracting it and removes the PowerShell script. Karachi Shipyard & Engineering Works (KS&EW), a well-known defense contractor in Pakistan, was connected to the luring document itself. This implies that the attacker's main goal was to use targets unique to the military industry to infiltrate it.
Following execution, the DLL starts a procedure that retrieves important configuration information from an embedded JSON file, such as server addresses, encryption keys, and other task parameters. The malware then securely communicates with the C2 server using this information to ask for more instructions on how to carry out the cyberattack. Additionally, the stager malware looks for a scheduled activity called "Schedule." The malware generates this task if it doesn't exist, making sure the malicious DLL runs every five minutes to keep the compromised machine persistent. This method is a component of a larger plan to make sure the infection stays hidden for as long as feasible.
The use of random domain generation is one of this attack's most noteworthy features. By creating backup domains for its C2 servers, the DONOT group has taken additional security measures to evade detection. Words from a hardcoded array of values are concatenated to generate these domains, and then a random top-level domain (TLD) is chosen. Even if some of the names are blacklisted, cybersecurity professionals will find it more difficult to shut down the C2 infrastructure due to this dynamic domain development process.
The DONOT group used a more advanced method of payload delivery in this campaign. This time, the decryption key was integrated into the malware itself, making it more difficult for analysts to find than in earlier campaigns where it was hardcoded into the configuration file. A more sophisticated method of cyber espionage is demonstrated by the malware's capacity to download, decrypt, and run additional payloads. The malware generates a scheduled task to run the final payload—which might include anything from data exfiltration tools to more malicious code that can harm the infiltrated systems over time—after the payload has been successfully decoded.
The DONOT APT group's most recent cyberattack represents a dramatic increase in its strategy, employing cutting-edge techniques like PowerShell exploitation, dynamic domain creation, and improved encryption to avoid detection. The fact that this attack targeted Pakistan's defense and sensitive maritime industries shows how dangerous these increasingly advanced organizations are becoming. Organizations must bolster cybersecurity defenses against this by implementing strong endpoint detection, carrying out frequent audits, and educating staff members to spot phishing attacks. To protect against future cyberattacks, proactive threat hunting and a well-defined incident response plan are crucial. To reduce the risks posed by sophisticated persistent threats like DONOT, vigilance and readiness are still essential.
Impact
- Cyber Espionage
- Sensitive Data Theft
- Unauthorized Access
- Command Execution
- Security Bypas
Indicators of Compromise
Domain Name
- internalfileserver.online
MD5
- c5f3fdf966f6c78d788d13a39c0cd2b1
- 812d1eae15d3852b7ad90c1ad443cf53
SHA-256
- cffe7eb01000de809b79a711702eaf3773f2e6167ce440f33f30bcd6fabcace3
- a7893c54edaecaa0e56010576a8249ad9149456f5d379868a0ecaa4c5c33fa70
SHA1
- a7cde1cfcb37ee45f4b64e0c7a1000d3b7973450
- 7ff4ba03fe7a402800938253c0eafc9ec0165cd3
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Deploy advanced endpoint security solutions that can detect and prevent the activities associated with the DONOT APT group.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Raising awareness among users about the risks associated with downloading apps from unknown or untrusted sources is crucial. Users should be educated about the importance of verifying app permissions and conducting background research on developers before installing apps.
- Implement reputable mobile security solutions on devices that can help detect and block malicious apps. Mobile antivirus and anti-malware software can provide an additional layer of protection against potential threats.
- Maintain regular and secure backups of critical data, ensuring that data can be restored in case of a cyberattack.
- Employ network monitoring and intrusion detection systems to detect and respond to suspicious activities in real time.
- Enforce the principle of least privilege, granting users only the minimum access required to perform their tasks.

