Severity
High
Analysis Summary
Palo Alto Networks has alerted users about active exploitation of CVE-2024-3393, a denial-of-service (DoS) vulnerability in its PAN-OS software. This vulnerability enables unauthenticated attackers to send specially crafted, malicious packets through the firewall’s data plane, causing the device to reboot. Repeated exploitation forces the device into maintenance mode, requiring manual intervention to restore operations. The issue affects devices with 'DNS Security' logging enabled, and attacks leveraging this flaw have resulted in customer outages as the firewalls attempt to block malicious DNS packets.
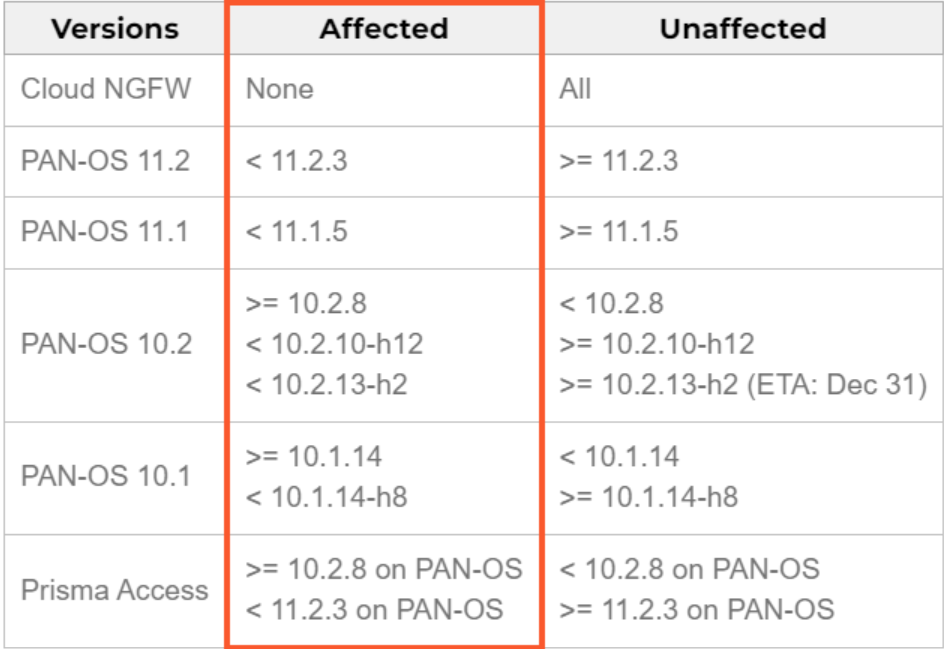
The vulnerability impacts specific versions of PAN-OS but has been resolved in PAN-OS versions 10.1.14-h8, 10.2.10-h12, 11.1.5, 11.2.3, and later. However, PAN-OS 11.0, which is also affected by CVE-2024-3393, will not receive a patch as it reached its end-of-life on November 17. Users of this version are urged to upgrade to a supported version to mitigate the risk. Palo Alto Networks confirmed the flaw is actively being exploited, underlining the importance of implementing these updates promptly.
For those unable to update immediately, the company has shared workarounds to mitigate risks. Unmanaged NGFWs, Panorama-managed NGFWs, or Prisma Access systems managed by Panorama users can navigate to Objects → Security Profiles → Anti-spyware → DNS Policies → DNS Security for each Anti-spyware profile. Here, they can change the log severity to "none" for all configured DNS Security categories, commit the changes, and revert the settings after applying fixes.
For NGFWs managed through Strata Cloud Manager (SCM), DNS Security logging can be disabled on individual NGFWs using the same steps or across all devices by filing a support case. Prisma Access users can also open a support case to disable DNS Security logging across all tenants or expedite tenant upgrades if necessary. These mitigation steps serve as temporary measures, but applying the permanent fixes in supported PAN-OS versions remains the most effective solution to safeguard against this vulnerability. Customers are strongly encouraged to act promptly to secure their devices and prevent disruptions.
Impact
- Denial of Service
Indicators of Compromise
CVE
- CVE-2024-3393
Affected Vendors
Affected Products
- Palo Alto PAN-OS 10.1.14-h8
- Palo Alto PAN-OS 10.2.10-h12
- Palo Alto PAN-OS 11.1.5
- Palo Alto PAN-OS 11.2.3
- Palo Alto PAN-OS 11.0
Remediation
- Refer to Palo Alto Networks Security Advisory for patch, upgrade, or suggested workaround information.
- Organizations must test their assets for the vulnerability mentioned above and apply the available security patch or mitigation steps as soon as possible.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations must stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.

