Severity
High
Analysis Summary
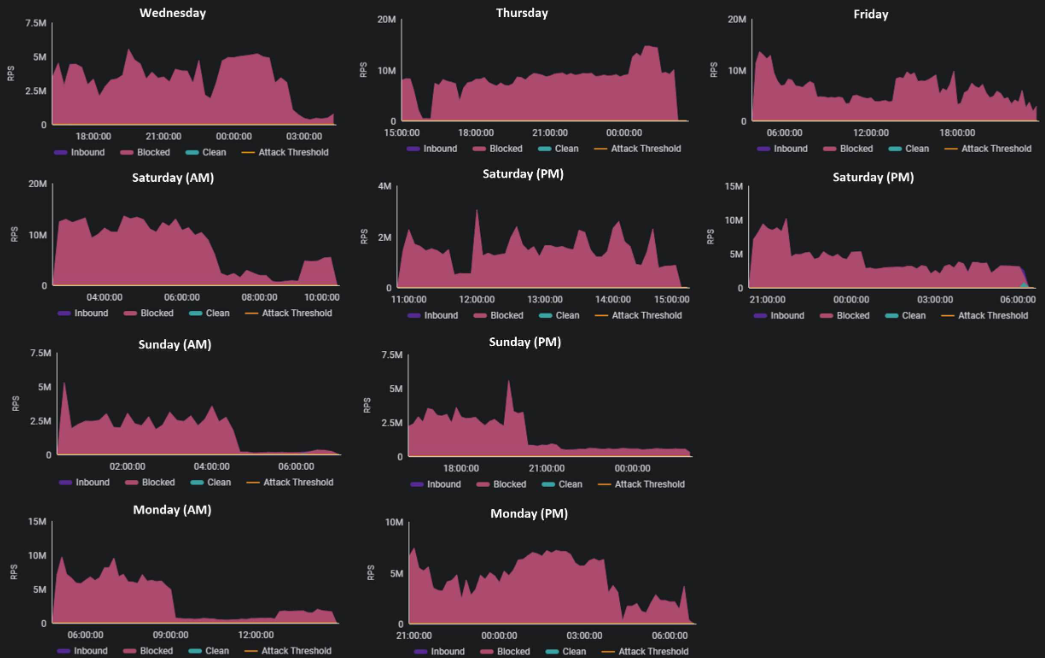
A record-breaking web DDoS attack campaign targeting a financial institution in the Middle East lasted six days, peaking at 14.7 million requests per second (RPS) and averaging 4.5 million RPS.
This extensive assault consisted of ten attack waves over 100 hours, significantly disrupting services with a low legitimate-to-malicious request ratio of 0.12%. A cybersecurity company's Web DDoS Protection Services successfully mitigated the attack, blocking over 1.25 trillion malicious requests while preserving 1.5 billion legitimate ones preventing any major service outages despite multiple attempts by the attackers.
The attack was attributed to SN_BLACKMETA, a hacktivist group possibly linked to Sudan and operating out of Russia. This group has a history of targeting high-profile infrastructure and financial systems in various countries including Israel, Canada, Saudi Arabia, France, and the UAE. SN_BLACKMETA announced the campaign on its Telegram channel before the attack highlighting its intention and following through with the execution.
SN_BLACKMETA's activities reflect a methodical approach to cyber warfare leveraging sophisticated attack methods and maintaining a high public profile through frequent updates and validations of their actions on social media. Their operations suggest a potential collaboration with other hacktivist groups like Killnet and the use of services such as InfraShutdown, a premium DDoS-for-hire service promoted by Anonymous Sudan. This service is known for its powerful and disruptive capabilities, posing a significant threat to global infrastructures.
The researchers emphasize the importance of robust DDoS mitigation strategies to withstand such intense and prolonged attacks. Essential measures include high-fidelity intelligence on threat actors behavioral-based detection to distinguish legitimate from malicious traffic, real-time signature creation to defend against unknown threats, and a comprehensive emergency response plan. Hybrid DDoS protection combining on-premise and cloud solutions is also crucial to address high-volume attacks and prevent network saturation.
Organizations are urged to bolster their defenses against sophisticated DDoS attacks by regularly inspecting and patching their networks. Implementing advanced cybersecurity measures and maintaining preparedness against emerging threats like SN_BLACKMETA are critical to safeguarding critical infrastructure and ensuring operational resilience.
Impact
- Operational Disruption
- Denial of Service
Remediation
- Regularly update firmware on all network devices, especially those identified as vulnerable.
- Implement strict access controls to limit the exposure of network device interfaces on the internet.
- Use advanced DDoS mitigation services and solutions that can handle high packet and bit rate attacks.
- Conduct frequent security audits and vulnerability assessments on network infrastructure.
- Employ network segmentation to isolate critical infrastructure and reduce the attack surface.
- Increase monitoring and detection capabilities to quickly identify and respond to unusual traffic patterns.
- Collaborate with device manufacturers to address and patch security vulnerabilities promptly.
- Educate and inform users and administrators about the importance of timely updates and secure configurations.
- Implement robust firewall and intrusion prevention systems to filter malicious traffic.
- Develop and maintain an incident response plan to handle DDoS attacks effectively and minimize downtime.

