Severity
High
Analysis Summary
A recent joint advisory from cybersecurity agencies across several countries has highlighted the activities of APT40, a China-linked cyber espionage group also known by various aliases including Bronze Mohawk and Gingham Typhoon.
The advisory underscores APT40's capability to swiftly exploit newly disclosed vulnerabilities in widely-used software like Log4j and Atlassian Confluence and its adeptness at transforming proofs-of-concept (PoCs) into operational exploits within a short timeframe. This agility allows APT40 to conduct targeted reconnaissance and exploitation operations across diverse sectors and geographical regions leveraging its association with China's Ministry of State Security (MSS).
APT40 has been active since at least 2011, primarily targeting organizations in the Asia-Pacific region but also extending its reach globally including Australia, the United States, and other countries represented by the advisory's agencies. Notably, its tactics involve deploying web shells for persistence, utilizing Australian websites for command-and-control purposes, and exploiting vulnerabilities in end-of-life or unpatched devices like SOHO routers. This operational approach aligns with broader trends observed in Chinese cyber espionage, emphasizing stealth through network edge device weaponization and living-off-the-land (LotL) tactics.
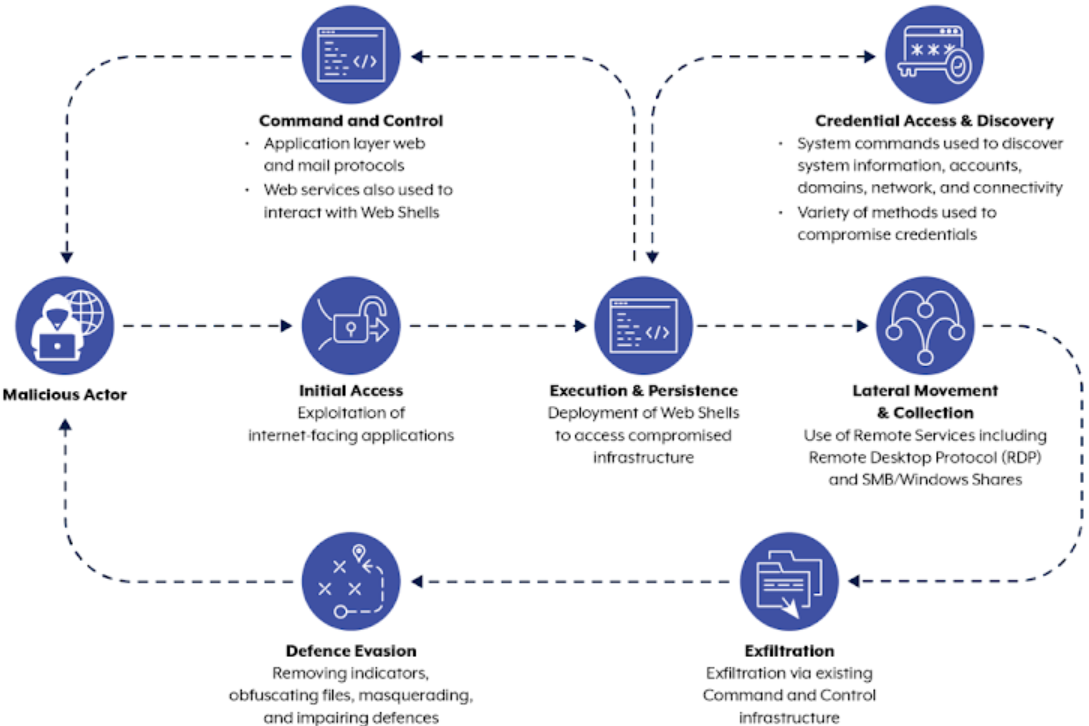
Recent campaigns attributed to APT40 include leveraging vulnerabilities such as CVE-2023-38831 in WinRAR for phishing campaigns targeting specific entities like Papua New Guinea, showcasing the group's adaptability and persistence in pursuing strategic objectives. Beyond initial exploitation, APT40 engages in comprehensive attack chains involving reconnaissance, privilege escalation, and lateral movement facilitated by techniques like remote desktop protocol (RDP) exploitation to exfiltrate valuable information.
Organizations are advised to implement robust cybersecurity measures to mitigate the risks posed by APT40 and similar threats. These include maintaining comprehensive logging mechanisms, enforcing multi-factor authentication (MFA) establishing rigorous patch management systems, replacing outdated equipment, and segmenting networks to restrict access to sensitive data. Such proactive measures are essential in countering the evolving tactics of state-sponsored threat actors like APT40 ensuring resilience against sophisticated cyber attacks aimed at intellectual property theft and compromise of critical infrastructure.
Impact
- Cyber Espionage
- Unauthorized Access
- Sensitive Data Theft
Indicators of Compromise
MD5
- 26a5a7e71a601be991073c78d513dee3
- 64454645a9a21510226ab29e01e76d39
- 5bf7560d0a638e34035f85cd3788e258
- e02be0dc614523ddd7a28c9e9d500cff
SHA-256
- 44369783a819a38909e89449495fb98c3f9ba07dd0d2fa55a24a560a89f21a86
- 97daa26c59e0e151f66872147ccd30dd1815bc6e63ec40c288130c6e8a6ea992
- b271e74ed44c3c405da858f29b6dfd4a99658dcac7bc83938079ad0dbbdf1b66
- 7c7acd87b47d405da4d6efa2c43599148e12c094970ba198905f0a165d79a78f
SHA-1
- 4d89f323a89acefc43c312cd0d198066db7ddf34
- 783d8b32d5a99bfe1367f0709562e36a6b4a042f
- 3d90768c117873cfb31102abec7b4e0834cd778e
- a900b33ba9700cf0aece6c2811202253767aa6e2
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Regularly update and patch software and systems to mitigate vulnerabilities.
- Conduct regular security audits and penetration testing to identify and address weaknesses.
- Review and reset user account passwords, especially those with elevated privileges, to prevent unauthorized access. Disable or remove any compromised accounts.
- Ensure secure storage of backups and sensitive information with access restricted to authorized personnel only.
- Implement strict access controls and the principle of least privilege (PoLP) to restrict user and system access rights. This reduces the attack surface.
- Continuously monitor command-and-control (C2) traffic patterns and communications to identify anomalies and block malicious C2 activity.
- Train employees and staff on cybersecurity best practices and how to recognize phishing attempts and social engineering tactics.
- Develop a robust incident response plan that outlines steps to take in the event of a breach. This should include procedures for containment, investigation, and notification of affected parties.

