Severity
High
Analysis Summary
On April 26, 2025, a newly-emerged ransomware gang "Everest" has recently added the banking sector i.e. Jordan Kuwait Bank, to the victim list on its data leak website.

Jordan Kuwait Bank, established in 1976, has grown into a key institution within Jordan's banking sector. It operates 62 branches across Jordan and one in Cyprus. Since its founding, the bank’s paid-up capital has expanded from JD 5 million to JD 100 million (around USD 141 million by 2008). Its core philosophy focuses on attracting investment into Jordan, particularly from Kuwait and other Arab nations.
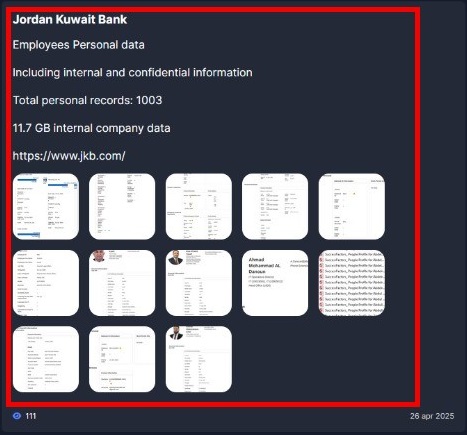
At an official website for Everest, the group has claimed to alleged access of 11.7GB of database by performing the ransomware attack. The database includes:
- Employees Personal Data
- Internal and Confidential Information
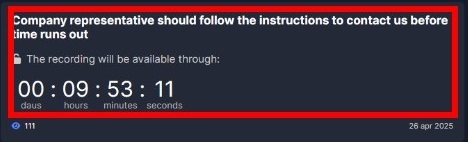
Moreover, the ransomware group has announced to publicly post the all information and confidential data after the 9 hours of time ultimatum given to company representatives.
To combat these threats, organizations need to implement comprehensive protection strategies beyond merely patching vulnerabilities. Effective defenses include rigorous network segmentation, strong access controls, regular vulnerability audits, and security hardening practices like disabling unnecessary services and employing encryption. Robust incident response plans and comprehensive backup strategies are crucial.
Impact
- Exposure of Sensitive Data
- Reputational Damage
Remediation
- Implement robust multi-layered security measures to detect and respond to ransomware activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known ransomware and indicators of compromise associated with ransomware groups.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

