Severity
High
Analysis Summary
Crazy Evil, a Russian-speaking cybercrime gang, has been linked to a series of social media scams targeting cryptocurrency users, primarily through the distribution of malware like StealC, Atomic macOS Stealer (AMOS), and Angel Drainer.
According to the Researcher, Operating since at least 2021, Crazy Evil specializes in identity fraud, cryptocurrency theft, and information-stealing malware. The group uses social engineering tactics and a network of traffic to redirect legitimate internet traffic to malicious phishing pages, compromising both Windows and macOS users. These attacks often focus on decentralized finance (DeFi) systems and are estimated to have generated over $5 million in illicit revenue, affecting tens of thousands of devices globally.
The gang operates through a sophisticated traffer model, employing six sub-teams—AVLAND, TYPED, DELAND, ZOOMLAND, DEFI, and KEVLAND—each associated with specific scams. These scams often promote fake platforms such as Voxium, TyperDex, DeMeet, and Selenium Finance, among others, under the guise of legitimate services. The malware used, primarily AMOS, is distributed via these fraudulent websites, and the group has been particularly active in exploiting the cryptocurrency space with highly-targeted spear-phishing campaigns. Crazy Evil's operations are further coordinated via Telegram channels, where affiliates are instructed on how to execute these attacks and share updates on their activities.
Crazy Evil's traffers use a "lead generation" approach to generate high-quality, undetected traffic, ensuring their malicious pages are not flagged by security vendors. The group’s success has also contributed to its growth, with over 4,800 subscribers on Telegram, where they provide tools, guides, and affiliate opportunities to other cybercriminals. The group’s modular structure, with distinct sub-teams dedicated to specific scams, has allowed it to scale operations effectively while maintaining operational secrecy. This approach has allowed them to maintain a sustained presence in the cryptocurrency ecosystem, further exacerbating the risks to digital asset holders.
In addition to its focus on cryptocurrency theft, Crazy Evil is part of a larger trend of cybercrime groups using traffic distribution systems (TDS) like TAG-124. This system, which overlaps with various ransomware groups, uses compromised WordPress sites to redirect users to fake landing pages that deliver malware. These sites, often running outdated plugins, make detection more difficult. The TDS is used to distribute not only malware like StealC and AMOS but also other malicious payloads like Lumma Stealer and Cobalt Strike Beacon. This interconnectedness between cybercrime groups highlights the broader threat landscape and the need for heightened security across platforms.
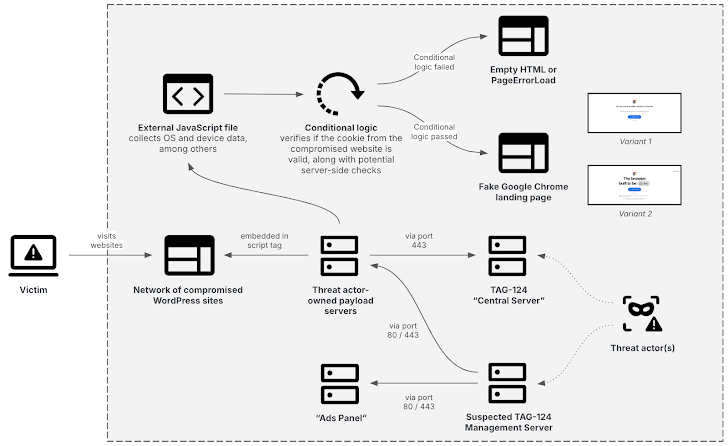
Recent developments show that the methods employed by Crazy Evil are being emulated by other threat actors, further increasing the risk to users in sectors like cryptocurrency, gaming, and software. As these cybercriminal entities refine their tactics and exploit popular platforms like GitHub for malware distribution, security teams must remain vigilant. The use of advanced techniques like fake Google Chrome update pages, malicious GitHub releases, and MaaS models is making it easier for these attackers to execute large-scale, low-cost campaigns. Consequently, ongoing vigilance and improved detection methods are essential in preventing the further erosion of trust and security in these sectors.
Impact
- Cryptocurrency Theft
- Information Theft
- Financial Loss
Indicators of Compromise
Domain Name
tokenframegovernance.com
voxiumcalls.com
voxium.eu
rocketgalaxy.io
gatherum.cc
IP
178.22.31.97
141.98.9.20
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Deploy and regularly update endpoint detection and response (EDR) solutions.
- Enable application whitelisting to prevent unauthorized software execution.
- Monitor for unauthorized access and unusual login attempts
- Track Crazy Evil’s tactics, techniques, and procedures (TTPs) through threat intelligence feeds.
- Block known malicious domains and IP addresses associated with Crazy Evil’s infrastructure.
- Set up alerts for indicators of compromise (IOCs) related to AMOS, StealC, and Angel Drainer.
- Use web filtering solutions to block access to phishing sites and malicious domains.
- Implement strict browser security settings and warn users against fake update prompts.
- Regularly audit and secure WordPress and other CMS platforms to prevent exploitation.
- Have an incident response plan in place to quickly contain and mitigate infections.
- Isolate compromised devices and perform forensic analysis to identify the attack vector.
- Regularly back up critical data and ensure backups are stored securely offline.

