Severity
High
Analysis Summary
Cl0p, an infamous ransomware group active since early 2019, has cemented its reputation as one of the most formidable cyber threats worldwide. With over 1,025 confirmed victims and an estimated $500 million in ransom profits, the Russian-linked operation has consistently targeted global corporate networks while deliberately avoiding CIS countries. The group derives its name from the “.cl0p” file extension used after encryption, which fittingly translates to “bedbugs” in Russian symbolizing its relentless persistence and adaptability in breaching secure systems.
The group’s latest campaign demonstrates a highly advanced exploitation of a zero-day vulnerability (CVE-2025-61882) in Oracle E-Business Suite (EBS), an enterprise-grade ERP solution used for order management, logistics, and procurement. First observed in June 2025, this flaw has recently seen a sharp rise in exploitation, enabling Cl0p to infiltrate networks rapidly and conduct large-scale data exfiltration. Analysts from highlighted the campaign as a major technical advancement, uncovering an elaborate exploitation infrastructure that indicates increasing sophistication in Cl0p’s attack methodology.
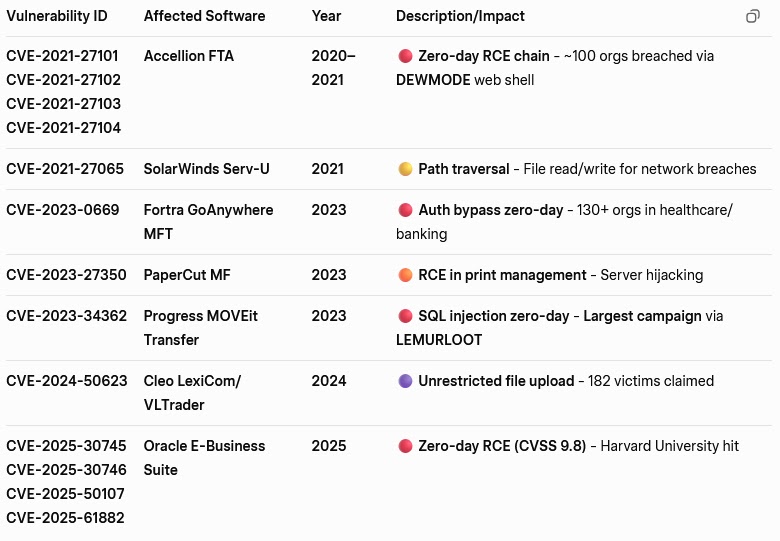
Upon deeper analysis of Oracle’s initial indicators of compromise, researchers traced two outbound IPs directly linked to active attacks. Further fingerprint correlation via Shodan and FOFA scans revealed 96 IP addresses sharing identical SSL certificate characteristics, illustrating Cl0p’s extensive and well-coordinated infrastructure. The data exposed a pattern of geographic distribution, although backend infrastructure remains largely dependent on Russian-based providers. This tactic highlights the group’s deliberate attempt to mask origins through global IP diversification while maintaining centralized control.
One of the most revealing discoveries is Cl0p’s infrastructure reuse strategy, showcasing continuity and efficiency between campaigns. Analysts found that 41 subnet IPs from the Oracle EBS exploitation were previously used in the 2023 MOVEit Transfer attacks (CVE-2023-34362), confirming the group’s preference for maintaining long-term hosting relationships and rotating infrastructure rather than rebuilding from scratch. Approximately 77.8% of subnets exhibited repeated use across multiple campaigns, with Alviva Holdings Limited identified as a key hosting provider for 15 of the active IPs. This persistent infrastructure reuse, combined with zero-day exploitation and geographic obfuscation, underscores why Cl0p continues to operate as one of the most resilient and technically adept ransomware syndicates in today’s threat landscape.
Impact
- File Encryption
- Gain Access
Indicators of Compromise
CVE
CVE-2023-34362
CVE-2025-61882
IP
- 15.235.83.73
- 82.117.252.142
- 79.141.160.78
- 79.60.150.121
- 45.182.189.109
- 5.188.87.38
- 92.118.36.249
- 185.104.194.134
- 45.227.252.199
- 45.182.189.107
- 91.199.163.59
- 45.227.255.28
Remediation
- Apply Oracle EBS patches and official vendor fixes for CVE-2025-61882 immediately (or apply vendor hardening workarounds if patching is delayed).
- Isolate any systems showing indicators of compromise (IoCs) take affected EBS servers offline from the network for forensic triage.
- Block the two known outbound IPs and any additional IPs found in your IOC list at perimeter firewalls and proxy gateways.
- Disable or restrict remote management interfaces and admin accounts for EBS until systems are validated.
- Implement strict egress filtering allow only required outbound connections from application servers; block suspicious destinations and non-standard ports.
- Use network segmentation: place ERP/EBS systems in a hardened VLAN with limited access from user/workstation networks.
- Enforce least privilege on hosting accounts and service accounts used by EBS (remove unnecessary privileges and local admin rights).
- Add SSL certificate fingerprint monitoring and alerting to detect reused certificates across your external infrastructure.

