Severity
High
Analysis Summary
A threat actor known as BlackTech (aka Earth Hundun) has been targeting the government, research, and technology industries in the Asia-Pacific area as part of a recent wave of cyberattacks. These incursions open the door to the release of an upgraded modular backdoor known as Waterbear and its improved replacement known as Deuterbear.
The cybersecurity experts said, “Among the group’s arsenal of weapons, the Waterbear backdoor is one of the most complex, with a wide array of anti-debug, anti-sandbox, and general antivirus-hindering techniques.”
Waterbear is renowned for its intricacy since it employs numerous evasion techniques to reduce the likelihood of being discovered and examined. BlackTech started utilizing the most recent iteration of Waterbear, often referred to as Deuterbear, in 2022. This version differs from the original Waterbear in several ways, including anti-memory scanning and decryption procedures. Under the alias Earth Hundun, the cybersecurity company is keeping tabs on the threat actor, who has been active since at least 2007. Other names for it include Palmerworm, HUAPI, Manga Taurus, Circuit Panda, Red Djinn, and Temp.Overboard.
Cybersecurity and intelligence agencies from the United States and Japan identified the adversary as Chinese in a joint advisory released in September of last year. The advisory detailed China's capacity to alter router firmware and take advantage of domain-trust relationships in routers to shift focus from overseas subsidiaries to their corporate headquarters located in both nations.
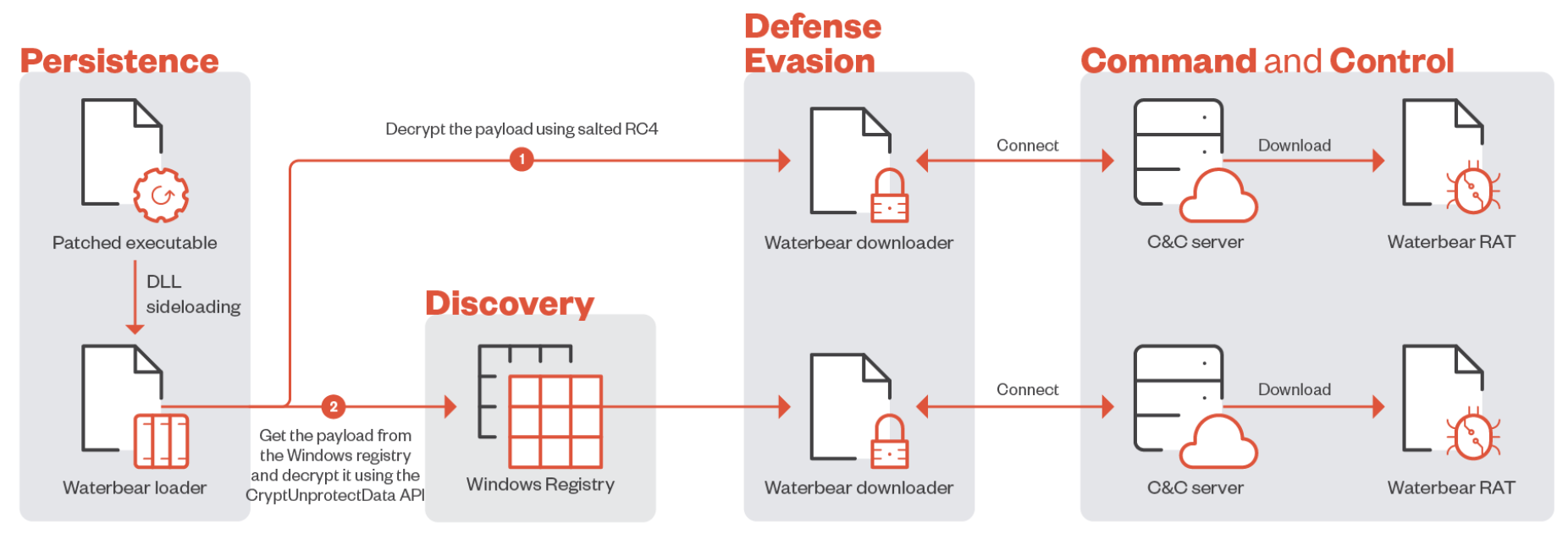
BlackTech actors hide their activities by using dual-use tools, specialized malware, and living-off-the-land strategies like turning off router recording. The cyber attackers frequently alter the firmware to conceal their activity across the edge devices after obtaining administrator access to network edge devices and establishing an early foothold into a target network. This helps them stay persistent in the network. Waterbear, also known as DBGPRINT, is an essential weapon in its extensive toolbox. It has been in use since 2009 and has received regular updates with better defense evasion characteristics.
A downloader is used to obtain the core remote access trojan via a command-and-control (C2) server. The loader is then used to launch the trojan, which is then run through a well-known method known as DLL side-loading. With the capability of almost 50 commands, the most recent version of the implant can carry out a multitude of tasks, including initiating and ending processes, managing files, capturing screenshots, altering the Windows Registry, and window management.
Deuterbear has also been distributed by a similar infection vector since 2022; its downloader employs a variety of obfuscation techniques to thwart anti-analysis and employs HTTPS for C2 connections. BlackTech has been steadily improving the Waterbear backdoor and all of its branches and variations since 2009. In addition to implementing several modifications in malware execution, like changing the function decryption, scanning for debuggers or sandboxes, and changing traffic protocols, the Deuterbear downloader uses HTTPS encryption to secure network traffic.
Impact
- Unauthorized Access
- Sensitive Data Theft
- Cyber Espionage
Indicators of Compromise
MD5
- fd5e3b9bf8dd997f1978c3fba49acc78
SHA-256
- d6ac4f364b25365eb4a5636beffc836243743ecf7ef4ec391252119aed924cab
SHA1
- 08ca912f6829dced15c08430352c0b082557af99
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Be vigilant when downloading software and double-check the URL to see if it is legitimate.
- Never download software from untrusted sources.
- Download apps only from official app stores like Google Play Store or Apple App Store. Avoid downloading apps from third-party websites or unofficial sources.
- Review the permissions requested by apps before installing them. Be cautious of apps that request unnecessary permissions or access to sensitive data.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.
- Keep your operating system and apps up-to-date with the latest security patches and updates
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Be cautious of unsolicited messages, emails, or links, especially from unknown or suspicious sources. Avoid clicking on suspicious links or downloading attachments from untrusted sources.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Regularly backup your data to a secure location, such as a cloud storage service or external hard drive.
- Develop and regularly update an incident response plan that outlines the steps to take in case of a security breach. Test the plan through simulations to ensure its effectiveness.

