Severity
High
Analysis Summary
As part of a campaign driven by financial gain, North Korean threat actors have been seen stealing money using a Linux version of a well-known malware family named FASTCash.
According to the researchers, to enable the unlawful withdrawal of cash from ATMs, the malware is deployed on payment switches within infected networks that process card transactions. The U.S. government initially revealed in October 2018 that North Korean-affiliated cybercriminals were using FASTCash as part of an ATM cashout scam that was targeting banks in Africa and Asia since at least late 2016.
FASTCash schemes aim to enable fraudulent transactions by remotely breaching payment switch application servers located within banks. In one 2017 instance, cash could be simultaneously withdrawn from ATMs spread over more than 30 countries thanks to the actions of HIDDEN COBRA threat actors. Another instance in 2018 had HIDDEN COBRA actors who made it possible to withdraw cash from ATMs in 23 different countries at the same time.
Previous FASTCash artifacts have included IBM AIX and Microsoft Windows computers (one detected as recently as last month), but the most recent research indicates that the samples intended to compromise Linux systems were initially uploaded to the VirusTotal platform in mid-June 2023.
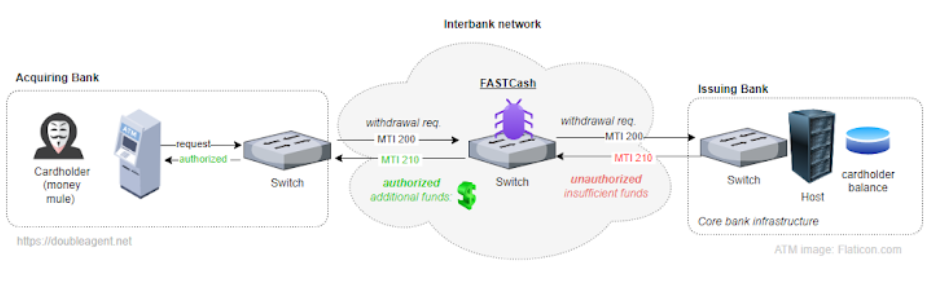
The malware is compiled for Ubuntu Linux 20.04 and appears as a shared object called "libMyFc.so". It is intended to start unapproved fund withdrawals by intercepting and altering ISO 8583 transaction communications, which are used to process debit and credit cards. It involves specifically faking refused (magnetic swipe) transaction signals that indicate there are not enough funds for a predetermined set of cardholder account numbers and allowing them to take out an arbitrary amount of Turkish Lira.
Per fraudulent transaction, the amount of money taken out ranges from 12,000 to 30,000 Lira ($350 to $875), which is similar to the Windows FASTCash artifact "switch.dll" that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) previously described in September 2020. The identification of the Linux variation highlights even more how important it is to have sufficient detection capabilities, which are frequently deficient in Linux server setups.
Impact
- Financial Loss
- Unauthorized Acces
Indicators of Compromise
MD5
- d1bb81f507a697548e1acbce814904de
- a97920557623296123d961f72e164513
- ac057094659b056c68360eb6665e4ace
- 7bae539b25bed652540a4792d32c7909
- fce3eda41abb6ab5b043164e44e95302
- 4ce9d999e0656fafab9d53e4a6b306a3
- 14d72896e174c0601d5d9ee4a5976ea5
- 518acee0cc61041709e9ebb38169bea0
- 03e6496b8a0187d0265b64612ec85291
- c4141ee8e9594511f528862519480d36
- 46b318bbb72ee68c9d9183d78e79fb5a
- d790997dd950bb39229dc5bd3c2047ff
SHA-256
- f34b532117b3431387f11e3d92dc9ff417ec5dcee38a0175d39e323e5fdb1d2c
- 7f3d046b2c5d8c008164408a24cac7e820467ff0dd9764e1d6ac4e70623a1071
- afff4d4deb46a01716a4a3eb7f80da58e027075178b9aa438e12ea24eedea4b0
- f43d4e7e2ab1054d46e2a93ce37d03aff3a85e0dff2dd7677f4f7fb9abe1abc8
- 5232d942da0a86ff4a7ff29a9affbb5bd531a5393aa5b81b61fe3044c72c1c00
- 2611f784e3e7f4cf16240a112c74b5bcd1a04067eff722390f5560ae95d86361
- c3904f5e36d7f45d99276c53fed5e4dde849981c2619eaa4dbbac66a38181cbe
- 609a5b9c98ec40f93567fbc298d4c3b2f9114808dfbe42eb4939f0c5d1d63d44
- 078f284536420db1022475dc650327a6fd46ec0ac068fe07f2e2f925a924db49
- 129b8825eaf61dcc2321aad7b84632233fa4bbc7e24bdf123b507157353930f0
- 10ac312c8dd02e417dd24d53c99525c29d74dcbc84730351ad7a4e0a4b1a0eba
- 3a5ba44f140821849de2d82d5a137c3bb5a736130dddb86b296d94e6b421594c
SHA-1
- 9f487df6c84dd794bafa3fa4173888e07af3fb60
- cdeefb46b4d8a58af99a429c8d6b5db575533cc5
- 206f602a3d571b4706a62a1b316ebd5b78d1706b
- 301bafbbf49f8b5ad56c11cbd1d548fde9027445
- 3ce053389d2bd4f8e04f4bbbbed224d8a544b245
- 83415069e4b62f0795144911f31f55ead3af670a
- 8e95a90f7dcc5f27006e64864b37abcc29562b67
- bccf365476b9037ca851625934b7c7363c6979f6
- 43c7b96e6c047015f66f2e3e591b94428eaf361a
- 2b22d9c673d031dfd07986906184e1d31908cea1
- 5375ad3746ce42a6f262f55c4f1f0d273fb69c54
- 7e6407c28c55475aa81853fac984267058627877
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure that all operating systems, software, and applications are regularly updated with the latest security patches.
- Conduct regular security awareness training for users to recognize and avoid phishing emails.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Implement network segmentation to limit lateral movement within the network.
- Implement continuous monitoring of network traffic and endpoint activities to detect any unusual or suspicious behavior.
- Develop and regularly test an incident response plan to ensure a swift and effective response in case of a security incident.
- Implement SIEM solutions to centralize log collection and analysis. This can help in identifying patterns of suspicious behavior and provide timely alerts for potential security incidents.
- Regularly back up critical data and ensure that the backup copies are stored securely.

