Severity
High
Analysis Summary
Arid Viper threat actor has been linked to a mobile espionage campaign that uses trojanized Android apps to distribute the spyware strain AridSpy. The infection is pushed via specific websites that mimic several messaging apps, a job opportunity app, and an app for the Palestinian Civil Registry.
The researchers said, “Often these are existing applications that had been trojanized by the addition of AridSpy's malicious code.”
Since 2022, there have reportedly been up to five campaigns involved in the activity; researchers have documented previous iterations of AridSpy. Of the five campaigns, three are still running. Since its debut in 2017, APT-C-23, Desert Falcon, Grey Karkadann, Mantis, and Two-tailed Scorpion have a lengthy history of employing mobile malware. In the past, Arid Viper has targeted journalists, dissidents, and military personnel in the Middle East. The group is still doing well in the mobile malware
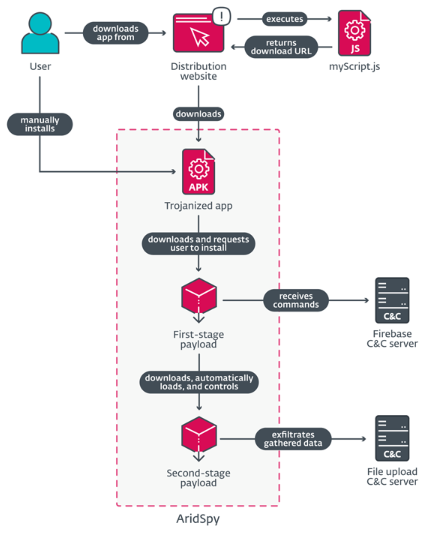
According to the analysis, the most recent version of AridSpy has been modified into a multi-stage trojan that allows the original, trojanized program to download more payloads from a command-and-control (C2) server. Through phony websites that serve as distribution hubs for the booby-trapped apps, the attack chains mostly target users in Egypt and Palestine.
A number of the functionally functioning but false apps, like LapizaChat, NortirChat, and ReblyChat—all based on real programs like StealthChat, Session, and Voxer Walkie Talkie Messenger—state that they are secure chat services. Another app claims to be from the Palestinian Civil Registry.
Additionally, it has been discovered that the Palestinian Civil Registry's website, which was registered on May 30, 2023, is promoted through a 179-follower Facebook page. The app that is being distributed through the website is based on the same-named program that can be downloaded from the Google Play Store. Although it is not a trojanized version of the Google Play app, the malicious program retrieves data from that app's real server. This indicates that Arid Viper developed its client layer to interface with the official server, drawing inspiration from that app's capabilities.
According to researchers, AridSpy was being distributed using a website that was registered in August 2023, pretending to be a job-searching app. The app's remarkable feature is that it isn't based on any real apps. When the malicious software is loaded, it first looks for security software on the device using a hard-coded list. If any are not present, it then downloads a first-stage payload. A Google Play Services update is what the payload pretends to be.
The trojanized app does not need to be installed on the same device for this payload to function. This implies that AridSpy won't be impacted in any way if the victim removes the original trojanized program, such as LapizaChat. The primary objective of the first stage is to download the malicious component that resides in the next stage component and uses a Firebase domain for C2 operations.
In addition to supporting a large number of commands to collect data from the devices, the malware can exfiltrate or deactivate itself while using a mobile data plan. Data exfiltration can be started with a command or by waiting for a predefined event to occur. AridSpy will capture a picture with the front camera and send it to the exfiltration C&C server if the victim locks or unlocks the phone. Pictures are only taken when the battery level is above 15% and it has been more than 40 minutes since the last picture was taken.
Impact
- Sensitive Data Theft
- Command Execution
- Cyber Espionage
- Data Exfiltration
Indicators of Compromise
Domain Name
- gameservicesplay.com
- palcivilreg.com
- analyticsandroid.com
- almoshell.website
MD5
- 3d070d0fed8bd8bde8bd09d907df66dc
- 2f5d39c31808ecf71b333818887d2f17
- 0980b29b5f52a36339ded0d62ec1af79
- 7269751abac507dd0305b89047e6851a
- 2224da16069d80b643dc2a25da9edc35
- 1ed7907aa77b9d36e707a6c662b911d8
- 24ac2a350a3c6aeb2e75413eb7c57ef1
- 103e22b050bdac39a80aac2c2831902d
SHA-256
- 0cb41557841ff6f314c398250a165706e0b18f93674a7c12f4489018a1661673
- f4ddfd426440829bcbbbe789cb0c18fa3a23798eb5643f1c88b7986390b3d648
- cace16a3ef7594ac9881a5a3baa3426b30a4d8c5f0f5caf378946f6ca72a4868
- d6140ef329f2a8f141a05055b1d583a40dc9f5b26b00c63c72c7ebd82fa3c7ec
- ddb91e692d0276684ac1a8af5f9ce5215fe53175c5918ce76906d45cfc2c7a03
- 6290d860b12c4981180f1acba8277dcd6ff7c50b811c267b80044f32126f8055
- 19df327e7c0ffe8bd883f044c3906424cefe893d50a0d5386e8445668d2dd1e4
- a4e74f74e675a08fdf8e0b55d5da59af8f1c67a2820c97ba6c6790b29589663d
SHA1
- 797073511a15eb85c1e9d8584b26baa3a0b14c9e
- a934fb482f61d85dda5e52a7015f1699bf55b5a9
- f49b00896c99ea030dcca0808b87e414bbde1549
- 568e62abc0948691d67236d9290d68de34bd6c75
- db6b6326b772257fddcb4be7cf1a0cc0322387d8
- 2158d88bce6368fac3fcb7f3a508fe6b96b0cf8a
- b806b89b8c44f46748888c1f8c3f05df2387df19
- 8ff57dc85a7732e4a9d144f20b68e5bc9e581300
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Only download apps from official app stores (Google Play Store and Apple App Store) and avoid third-party app sources.
- Review the permissions an app requests during installation. If an app asks for excessive permissions that are unrelated to its functionality, consider it a red flag.
- Never trust or open links and attachments received from unknown sources/senders.
- Encourage individuals to report any suspicious activities, emails, or messages to relevant authorities, organizations, or cybersecurity experts.
- Verify the authenticity of websites, social media profiles, and apps before providing personal information or engaging with them.
- Implement strong, multi-factor authentication (MFA) for email accounts, social media profiles, and other sensitive online services.
- Keep all software and operating systems up to date with the latest security patches to minimize vulnerabilities.
- Employ robust network security measures, including firewalls and intrusion detection systems, to detect and block malicious network traffic.
- Develop and maintain an incident response plan that outlines steps to take in case of a security breach. Ensure that individuals and organizations know how to respond effectively.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Refrain from downloading apps from unofficial sources or third-party app stores. These sources are less regulated and more prone to hosting malicious apps.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using a multi-layered protection is necessary to secure vulnerable assets.

