Severity
High
Analysis Summary
'Glutton' is a new PHP backdoor that the Chinese threat group APT41 is utilizing to attack both Chinese and American corporations, as well as other cybercriminals. The new PHP malware was found in late April 2024 by researchers but there is proof that it was deployed in December 2023 together with other files.
Although Glutton is a sophisticated backdoor, researchers note that it has significant flaws in encryption and stealth, which may suggest that it is still in the early stages of development. APT41, another name for Winnti, is a well-known Chinese state-sponsored threat actor that specializes in financial crime and cyber espionage. Since coming to prominence in 2012, the group has attacked government and political organizations, as well as companies in the gambling, pharmaceutical, and telecommunications sectors.
Glutton is a modular backdoor based on ELF that gives APT41 freedom and stealth by enabling them to activate particular components for customized attacks. 'task_loader,' which establishes the environment; 'init_task,' which installs the backdoor; 'client_loader,' which adds obfuscation; and 'client_task,' which runs the PHP backdoor and interacts with the command-and-control (C2) server, are its essential components.
Because of their high degree of modularity, these payloads can be used alone or in a series of steps using task_loader to create an all-encompassing attack architecture. To achieve a covert footprint, all code execution takes place inside PHP or PHP-FPM (FastCGI) processes, guaranteeing that no file payloads are left behind.
Phishing as a 'php-fpm' process, the backdoor injects malicious code ('l0ader_shell') into PHP files on ThinkPHP, Yii, Laravel, and Dedecms frameworks, enabling fileless execution through dynamic in-memory execution. '/etc/init.d/network' is one of the system files that Glutton alters to create persistence across reboots. It can also alter Baota panel files to keep control and steal setups and credentials. The malware can steal data and system information from the filesystem in addition to Baota.
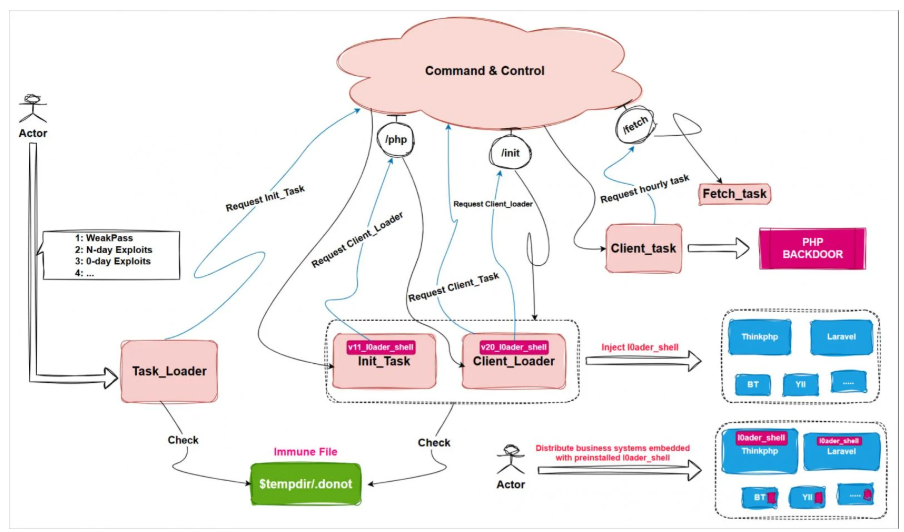
22 commands that are received from the C2 server are supported by Glutton. According to the researchers, APT41 has used Glutton on targets in China and the USA, with a primary focus on online app developers, social security organizations, and IT services. Code injection is used against well-known PHP web development frameworks, such as ThinkPHP, Yii, Laravel, and Dedecms, which are frequently used in business-critical applications. Because it is frequently used to handle sensitive data, including MySQL databases, the Baota web panel, a well-known server management tool in China, is also targeted.
By incorporating Glutton into software packages offered for sale on cybercrime forums such as Timibbs, the threat actors are also actively employing it to search for other hackers. These trojanized software programs pose as click-farming platforms, phony cryptocurrency exchanges, and gambling and gaming systems. Glutton uses the 'HackBrowserData' tool to retrieve private data from online browsers, including credit card numbers, passwords, cookies, download histories, and browsing histories, after the hackers' computers have been compromised.
Researchers speculate that the deployment of HackBrowserData was a "black eats black" tactic. HackBrowserData is used by Glutton's operators to steal sensitive, valuable data from cybercriminals when they try to locally debug or alter backdoored corporate systems. By using the attackers' actions against them, this starts a cyclical attack chain. Concerning this APT41 campaign, which has been going on for more than a year, researchers presented signs of compromise. The original access vector is still unclear, though.
Impact
- Cyber Espionage
- Financial Loss
- Unauthorized Access
- Code Execution
- Sensitive Data Theft
Indicators of Compromise
Domain Name
- cc.thinkphp1.com
IP
- 156.251.163.120
- 172.247.127.210
MD5
- 8fe73efbf5fd0207f9f4357adf081e35
- f8ca32cb0336aaa1b30b8637acd8328d
- ac290ca4b5d9bab434594b08e0883fc5
SHA-256
- d0cbd60ec32ca016ec1cf402da977dbbcc3f7387bdb580055ad04f66c8f3989e
- 60c71dc626fbf248b85f9cacbd3768fa6e163017621bac31acc49ca1dd2cd436
- 777c1fda4008f122ff3aef9e80b5b5720c9f2dbc3d7e708277e2ccad1afd8cc5
SHA1
- dd242818a0a08fac23ec820a4338fbdba6b5964e
- 9891394ce33dd7ab4bd6b776e814110e573c11b1
- 64f11153d9a845db0a2c713900562c6f0cd74971
URL
- http://v6.thinkphp1.com/php?
- http://v20.thinkphp1.com/v20/init?
- http://v20.thinkphp1.com/v20/fetch?
- http://v6.thinkphp1.com/bt
- http://v20.thinkphp1.com/bt
- http://v6.thinkphp1.com/msg
- http://v20.thinkphp1.com/msg
- http://v6.thinkphp1.com/save
- http://v20.thinkphp1.com/save
- http://v6.thinkphp1.com/client/bt
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Regularly change passwords for all accounts and use strong, unique passwords for sensitive accounts.
- Carefully check the URLs before entering credentials or downloading software.
- Implement multi-factor authentication (MFA) on all accounts to add an extra layer of security to login processes.
- Consider the use of phishing-resistant authenticators to further enhance security. These types of authenticators are designed to resist phishing attempts and provide additional protection against social engineering attacks.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations need to stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.
- Never trust or open links and attachments received from unknown sources/senders.

