Severity
High
Analysis Summary
SHROUDED#SLEEP is a sophisticated cyber-espionage campaign attributed to APT37, a North Korean state-sponsored threat actor also known by aliases such as InkySquid and Reaper. This group, active since at least 2012 is believed to be part of North Korea's Ministry of State Security (MSS).
The campaign targeting Cambodia and likely other Southeast Asian nations employs a previously unknown backdoor and remote access trojan (RAT) called VeilShell. APT37 is known for its versatility in cyber-operations including developing custom malware and leveraging tools like RokRAT for intelligence gathering.
According to the report, this attack begins with the delivery of a ZIP archive containing a Windows shortcut (LNK) file which likely arrives via spear-phishing emails. Once launched the LNK file triggers PowerShell code execution to deploy next-stage components such as a decoy lure document a configuration file, and a malicious DLL. These files are quietly dropped into the Windows startup folder enabling persistence. A unique method used in this campaign is AppDomainManager injection allowing the attackers to stealthily load the malicious DLL and later retrieve the VeilShell backdoor from a remote server.
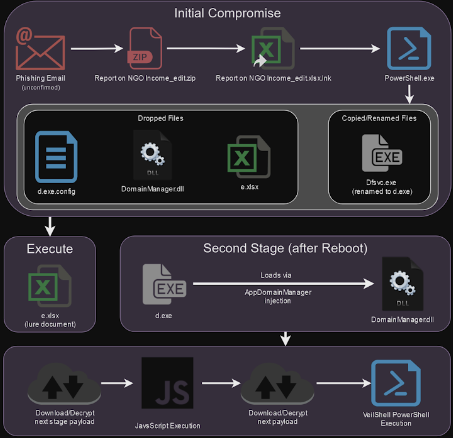
VeilShell is a PowerShell-based malware that provides attackers with extensive control over compromised systems. Its capabilities include file exfiltration, system task manipulation, downloading and uploading files, and ZIP archive extraction. The malware is designed to remain undetected utilizing long sleep times between actions and delaying execution until after the system reboots. This level of stealth allows the attackers to maintain persistent access and avoid detection by traditional security measures.
The SHROUDED#SLEEP campaign highlights a patient and methodical approach by APT37, emphasizing long-term control over compromised systems. The use of AppDomainManager injection and PowerShell-based RATs reflects the evolving techniques in cyber-espionage operations. Securonix's report also draws parallels with other North Korean groups like Lazarus and Kimsuky, noting that state-aligned attackers are increasingly using advanced malware techniques to achieve their espionage and financial objectives across different regions, including Southeast Asia and the U.S.
Impact
- Cyber Espionage
- Data Exfiltration
- Unauthorized Access
- Information Theft
Indicators of Compromise
IP
- 172.93.181.249
MD5
- bbccf12b0be14d50f955813302029b2d
- 6a0aa1baee0f621768130d8be822d6f0
- 63dc2ab3fb59a1e5caf485b60ed1f9cc
- 23d55b0f6a502c7ed3a70d41272b0732
- ff83093c7cc91e59d0fa741c10ea6d5e
SHA-256
- beaf36022ce0bd16caaee0ebfa2823de4c46e32d7f35e793af4e1538e705379f
- 913830666dd46e96e5ecbecc71e686e3c78d257ec7f5a0d0a451663251715800
- 9d0807210b0615870545a18ab8eae8cecf324e89ab8d3b39a461d45cab9ef957
- cfbd704cab3a8edd64f8bf89da7e352adf92bd187b3a7e4d0634a2dc764262b5
- 106c513f44d10e6540e61ab98891aee7ce1a9861f401eee2389894d5a9ca96ef
SHA-1
- 0feb9d41f11876ba6e641bee47ef3221e8cea919
- 7cb2c5009dc85fa80697ba4678a8545431ba82ad
- 7d45d1f8b6f2b919b526eb9f085f2c7dc189f81e
- 36a2c2cd63e3ca23a7934cfb3e7a957f2b5363f8
- 21cc11f788952ee9a99431843bf8d56e246d6944
Remediation
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Ensure that general security policies are employed including implementing strong passwords, correct configurations, and proper administration security policies.
- Limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.

