Severity
High
Analysis Summary
Threat actors behind the Chameleon Android banking malware, which targets Canadian users by posing as Customer Relationship Management (CRM) software, have been using a new tactic that cybersecurity researchers have uncovered.
The researchers said, “Chameleon was seen masquerading as a CRM app, targeting a Canadian restaurant chain operating internationally.”
Targeting consumers in Canada and Europe, the campaign was first seen in July 2024 and suggested that the company was expanding its victimology reach beyond Australia, Italy, Poland, and the United Kingdom. The use of CRM-related themes by the malicious dropper programs that carry the malware suggests that business-to-consumer (B2C) workers and customers in the hospitality industry are the intended targets.
Additionally, the dropper artifacts are made to get beyond Google's Restricted Settings, which were implemented in Android 13 and later. This is done to stop side-loaded programs from demanding risky rights, such as accessibility services, a tactic that was previously used by SecuriDroper and Brokewell. After installation, the program presents a phony login page for a CRM tool before pretending to be an error message and asking the victims to reinstall it—but in actuality, it launches the Chameleon payload.
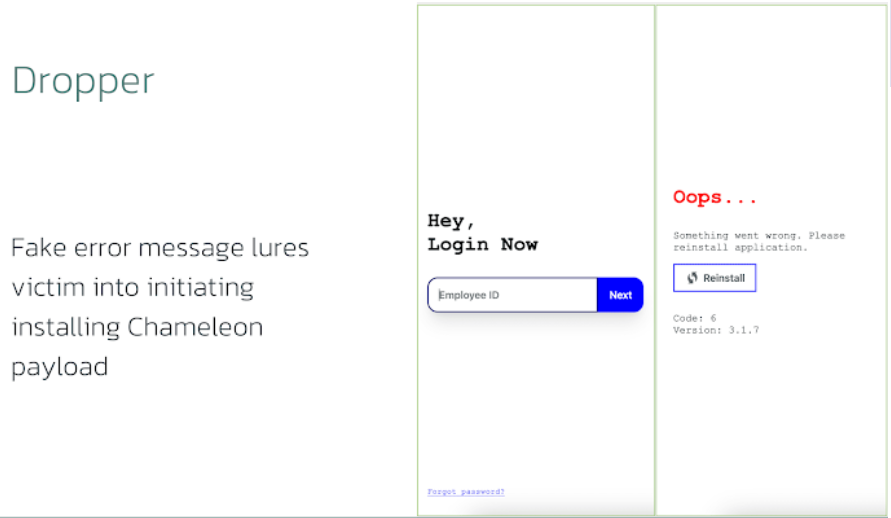
After completing the login process, the fake CRM website is loaded once more with a fresh error message reading "Your account is not activated yet. Contact the HR department". With the ability to do on-device fraud (ODF) and transfer user funds fraudulently, Chameleon can also gather credentials, contact lists, SMS messages, and geolocation data by using overlays and a broad range of permissions. Chameleon gains access to business banking accounts and poses a serious risk to the company if the attackers are successful in infecting a device that has access to corporate banking. This latest campaign's choice of masquerade is probably because of the greater chance of such access for employees whose duties involve CRM.
This development occurred weeks after researchers revealed the details of a banking malware campaign in Latin America carried out by the CyberCartel gang to steal financial information and credentials, as well as to distribute a trojan called Caiman through rogue Google Chrome extensions. Installing a rogue browser plugin and using the Man-in-the-Browser approach is the ultimate goal of these nefarious acts. This makes it possible for the attackers to obtain private banking information illegally in addition to other pertinent information like on-demand screenshots and information about compromised machines. The threat actors share setups and updates over a Telegram channel.
Impact
- Credential Theft
- Sensitive Data Theft
- Financial Loss
- Unauthorized Access
Remediation
- Ensure that all operating systems, software, and applications are regularly updated with the latest security patches.
- Conduct regular security awareness training for users to recognize and avoid phishing emails.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using multi-layered protection is necessary to secure vulnerable assets.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Implement network segmentation to limit lateral movement within the network.
- Implement continuous monitoring of network traffic and endpoint activities to detect any unusual or suspicious behavior.
- Develop and regularly test an incident response plan to ensure a swift and effective response in case of a security incident.
- Implement SIEM solutions to centralize log collection and analysis. This can help in identifying patterns of suspicious behavior and provide timely alerts for potential security incidents.
- Regularly back up critical data and ensure that the backup copies are stored securely.

