Severity
High
Analysis Summary
Cybersecurity researchers uncovered a malicious Android app on the Google Play Store which stole around $70,000 in cryptocurrency over five months by masquerading as the legitimate WalletConnect protocol.
According to the report, This app disguised under various names like "Mestox Calculator" and "WalletConnect - DeFi & NFTs," tricked users with fake reviews and consistent branding achieving over 10,000 downloads. The app specifically targeted mobile device users marking the first time a cryptocurrency drainer has focused solely on this group. Over 150 users fell victim to the scam though not all who downloaded the app were affected.
The malicious app associated with a developer named UNS LIS was popular in countries such as Nigeria, Portugal, and Ukraine. It redirected users to a bogus website based on their IP address and User-Agent, mimicking a legitimate service like Web3Inbox to trick them. If the victim’s criteria didn’t match the attacker's target the app would reroute them to legitimate sites to avoid detection allowing it to bypass Google's app review process. The app also prevented analysis by implementing techniques that obscure its true behaviour.
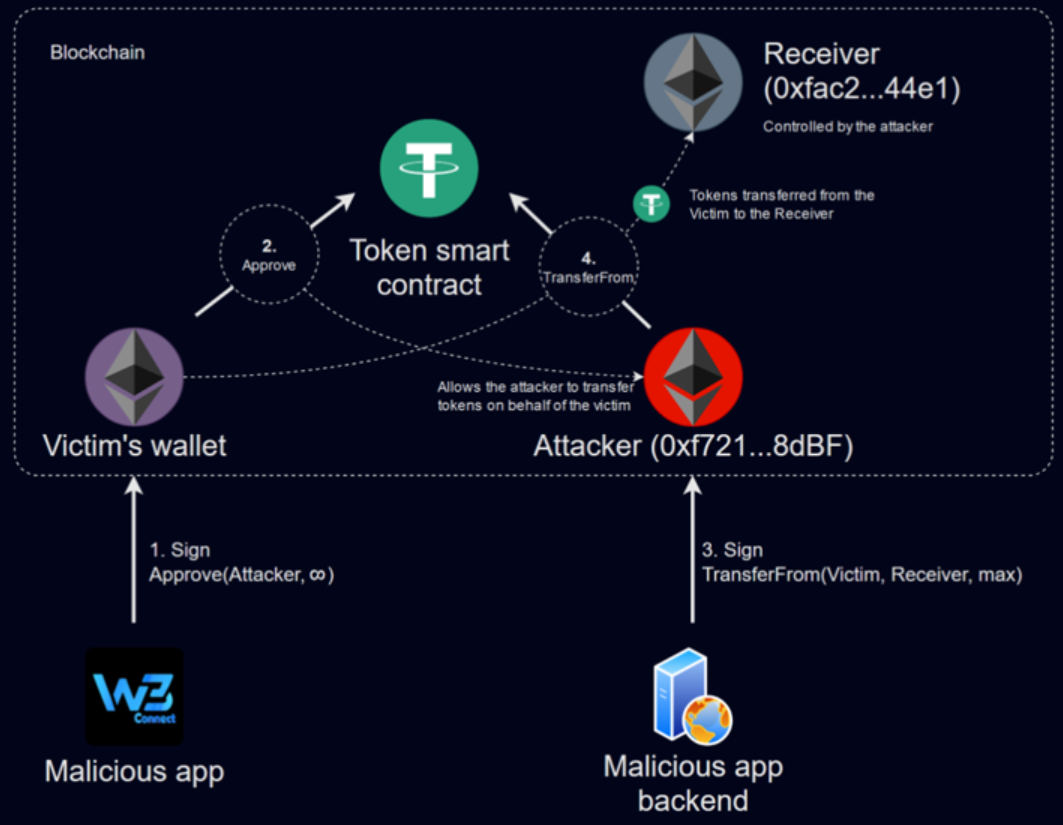
The malware identified as MS Drainer, functioned by prompting users to connect their cryptocurrency wallets and sign several transactions. Once the victim’s information was entered, it was transmitted to a command-and-control server which instructed the app to initiate unauthorized transfers from the victim’s wallet to the attacker's addresses. Victims unknowingly granted permission for the attackers to continually withdraw digital assets from their wallets.
Researchers highlighted the app’s sophisticated use of smart contracts and deep links to drain funds without relying on traditional methods like permissions or keylogging. A similar app, "Walletconnect | Web3Inbox," was found on the Play Store in early 2024, further illustrating the growing complexity of threats in decentralized finance (DeFi) and the risks associated with third-party tools in managing digital assets.
Impact
- Gain Access
- Financial Loss
- Crypto Theft
Indicators of Compromise
MD5
- 1c5a7bc2dfcbc10b3ac5249147e4ec7f
- c324bbc6dcfd1fed08bf24b279555dd9
- bf6af7b0945bb848a37d2f5032249122
SHA-256
- ea526792150e71402f896ddaf1f04aedcb1356aea3bfebbcaf6c90bcdde7aa0c
- bf557e975733c113acc38daa18ca1849a1022b4c30b118899f68210cd3c7f990
- 42330ccaaacea8a18794c7e9fad100de31ea415bff7821e407b9ac70ef690032
SHA-1
- d727dd6a6495d7450a338f714e1858d59d5ea46e
- f608331fbd48f348baa24a11d606af85e778624e
- dd2ad7bd5cafde8a4d66b3815cc1d35c0e0ffdef
Remediation
- Block all threat indicators at your respective controls. Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Enabling two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly change passwords for all accounts and use strong, unique passwords for sensitive accounts.
- Carefully check the URLs before entering credentials or downloading software.
- Implement multi-factor authentication (MFA) on all accounts to add an extra layer of security to login processes.
- Consider the use of phishing-resistant authenticators to further enhance security. These types of authenticators are designed to resist phishing attempts and provide additional protection against social engineering attacks.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations need to stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.
- Never trust or open links and attachments received from unknown sources/senders.

