Severity
High
Analysis Summary
Recently, researchers reported that the notorious Cyclops ransomware gang has started offering a Go-based info stealer to other cybercriminals. This tool can be used to steal sensitive information such as login credentials, credit card details, and other personal data from infected hosts.
“The threat actor behind this RaaS promotes its offering on forums. There it requests a share of profits from those engaging in malicious activities using its malware.” said in a report
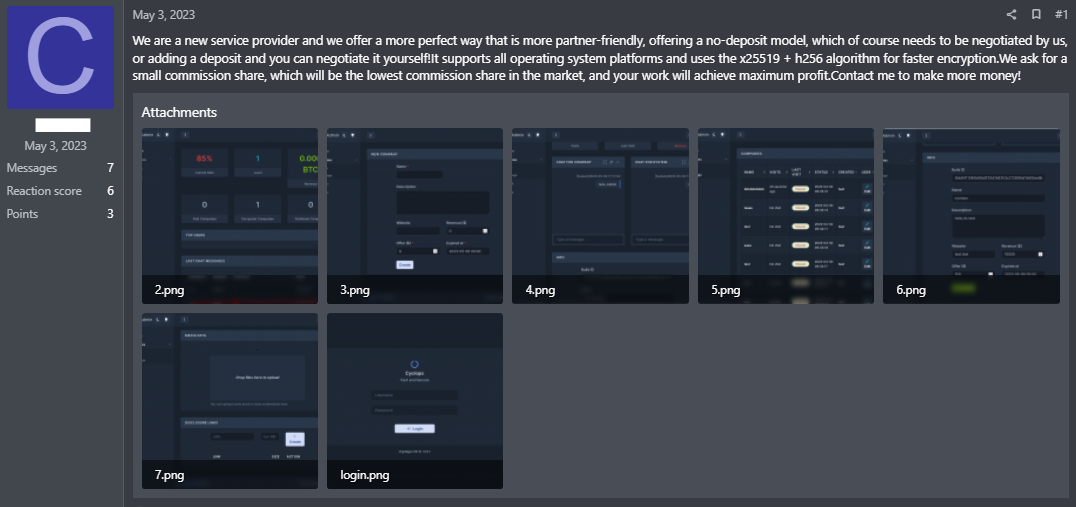
The group is known for using advanced techniques to evade detection and encryption to lock victims’ files. With this new offering, the Cyclops gang is expanding its reach and potentially increasing the number of victims it can target.
Cyclops ransomware is a notable threat that targets multiple operating systems, including Windows, macOS, and Linux. Its cross-platform capability allows it to infect and encrypt files on a wide range of systems, potentially impacting users across different environments.
One aspect of Cyclops ransomware is its use of Golang, or the Go programming language, for the macOS and Linux versions. Golang is known for its efficiency and cross-platform support, making it an attractive choice for developing malware that can target multiple operating systems.
The Go-based stealer associated with the Cyclops ransomware is specifically designed to target both Windows and Linux systems. It aims to gather various system-related details such as the operating system information, computer name, and the number of running processes. Additionally, it focuses on capturing files that match specific extensions of interest.
The targeted file extensions include .TXT (text files), .DOC (Microsoft Word documents), .XLS, .PDF, .JPEG and .JPG, and .PNG. These file types often contain valuable and sensitive information. Once the data has been harvested, the Go-based stealer proceeds to upload the collected files to a remote server. This allows the threat actors to access the stolen data from an admin panel.
The information stealer component of the Cyclops ransomware designed to be accessed by the threat actors’ customers through an admin panel, suggests a possible ransomware-as-a-service (RaaS) model.
The emergence of this information stealer highlights the increasing sophistication and diversification of cyber threats. Organizations and individuals should remain vigilant, maintain up-to-date security measures, and employ best practices to protect their systems and data from such malicious activities.
Impact
- Sensitive Information Theft
Remediation
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Never trust or open links and attachments received from unknown sources/senders.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Promoting user awareness and education is crucial in preventing successful attacks. Users should be cautious when handling email attachments, visiting suspicious websites, or downloading files from untrusted sources. Providing education on phishing techniques and implementing robust email filtering can significantly mitigate these risks.
- Regularly backing up critical data is indeed essential to mitigate the impact of ransomware attacks. It’s crucial to ensure that backups are securely stored and regularly tested to guarantee data integrity and availability in the event of an incident.
- Implementing multi-factor authentication (MFA) for critical systems and sensitive data access is a recommended practice. MFA adds an extra layer of security by requiring additional authentication factors, making it more challenging for attackers to gain unauthorized access even if they have compromised a user’s credentials.
By incorporating these measures into an organization’s security strategy, the risk of successful attacks, including those involving the Cyclops ransomware gang and information stealers, can be significantly reduced.

