Severity
High
Analysis Summary
Tens of thousands of Microsoft Exchange email servers across Europe, the U.S., and Asia are exposed on the public internet and vulnerable to remote code execution flaws. These servers are running an unsupported software version that no longer receives updates, leaving them susceptible to multiple security issues, some with critical severity ratings.
According to internet scans by The ShadowServer Foundation, nearly 20,000 Microsoft Exchange servers are currently reachable over the public internet and have reached the end-of-life (EoL) stage. As of a recent scan in late November, a security researcher discovered over 30,000 Microsoft Exchange servers with an unsupported version. These servers include 275 instances of Exchange Server 2007, 4,062 instances of Exchange Server 2010, and 26,298 instances of Exchange Server 2013.
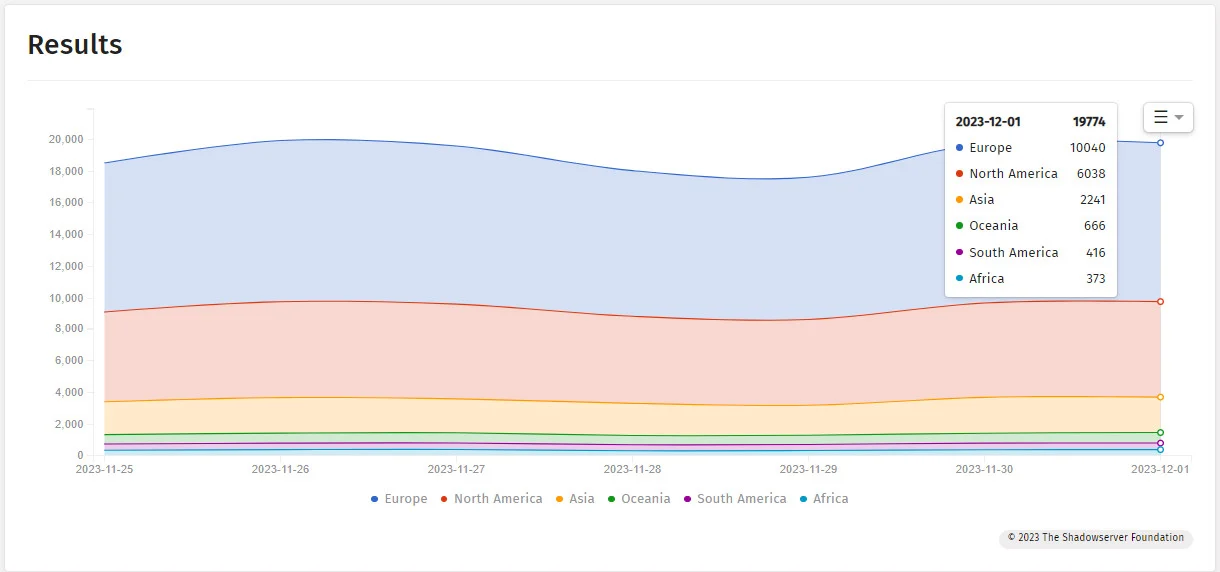
The global number of EoL Exchange servers has only dropped by 18% since April, which the researcher considers insufficient. The outdated Exchange machines found on the public web are vulnerable to various remote code execution flaws, including critical ones like ProxyLogon (CVE-2021-26855). Some machines are also susceptible to a less severe bug identified as CVE-2021-27065, which can be chained with ProxyLogon to achieve remote code execution.
Researchers revealed that, based on build numbers, close to 1,800 Exchange systems are vulnerable to ProxyLogon, ProxyShell, or ProxyToken vulnerabilities. The ShadowServer Foundation identified several security flaws in these outdated Exchange machines, including CVE-2020-0688, CVE-2021-26855 (ProxyLogon), CVE-2021-27065 (part of the ProxyLogon exploit chain), CVE-2022-41082 (part of the ProxyNotShell exploit chain), CVE-2023-21529, CVE-2023-36745, and CVE-2023-36439. While most vulnerabilities do not have a critical severity score, Microsoft marked them as “important,” and all except the ProxyLogon chain were considered “more likely” to be exploited.
Despite some companies implementing mitigations, Microsoft recommends prioritizing the installation of updates on externally facing servers. For instances that have reached the end of support, the only viable option is to upgrade to a version that still receives security updates. The situation underscores the ongoing risks associated with outdated software and the importance of timely updates to address security vulnerabilities.
Impact
- Remote Code Execution
Remediation
- Prioritize updating and patching Microsoft Exchange servers to the latest supported versions.
- Apply security updates and patches released by Microsoft to address vulnerabilities, especially critical ones like ProxyLogon (CVE-2021-26855).
- Implement available mitigations for known vulnerabilities, even if a full update is not immediately possible.
- Follow Microsoft’s guidance on mitigating specific vulnerabilities to reduce the risk of exploitation.
- Conduct a thorough risk assessment to identify and prioritize vulnerable systems within the organization.
- Evaluate the severity of the vulnerabilities and potential impact on business operations.
- Conduct regular security audits to identify and address any weaknesses or outdated systems within the network.
- Implement network segmentation to isolate critical systems, including Exchange servers, from the public internet to reduce exposure to potential threats.
- For servers that have reached end-of-life, consider upgrading to a supported version that receives security updates.
- Provide training and awareness programs for users and IT staff to recognize and report potential security threats.
- Emphasize the importance of staying vigilant against social engineering tactics.

