Severity
High
Analysis Summary
The notorious banking Trojan, TrickBot, has resurfaced with a new Android variant known as “TrickMo,” as investigated by Researchers. Initially detected in September 2019, TrickMo has evolved, utilizing JsonPacker to conceal its code. Unlike earlier versions, the latest TrickMo boasts enhanced capabilities, including overlay injection—a more sophisticated technique compared to traditional screen recording for capturing sensitive information.
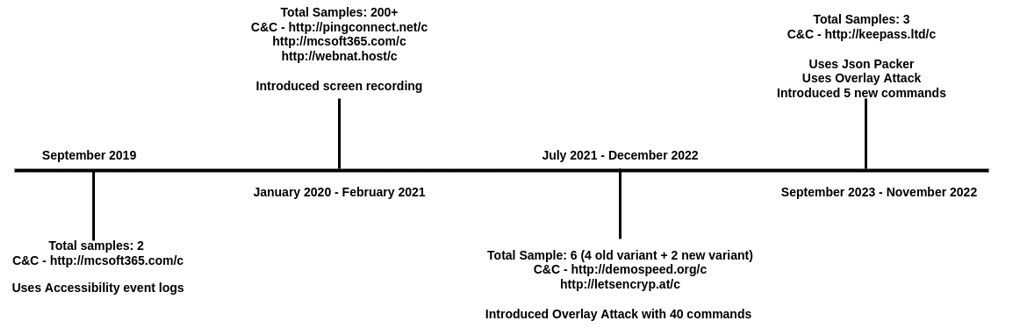
Overlay Attack allows TrickMo to efficiently carry out activities like exfiltrating device screen content, downloading runtime modules, and executing overlay attacks on targeted banking apps and browsers. This represents a notable advancement in TrickMo’s tactics since its inception, showcasing a more evolved and potent threat.
The Clicker function within TrickMo automates predefined actions on specific applications defined by the malware author. This automation occurs without the victim’s knowledge, emphasizing TrickMo’s increased level of sophistication. Notably, TrickMo has shifted from screen recording via the MediaProjection API to collecting Accessibility event logs, which are then sent to the malware author as a zip file.
TrickMo’s success on a target device requires the victim to grant Accessibility Service access, a step the malware prompts repeatedly. The Android Operating System’s built-in Accessibility Service typically discourages such activities, highlighting the necessity for user cooperation in TrickMo’s execution.
The latest variant of TrickMo incorporates 45 commands in its arsenal, each designed for malicious purposes, including compromising and exfiltrating sensitive data from victims’ devices.
Impact
- Sensitive Information Theft
- Credentials Theft
Indicators of Compromise
MD5
- c74014b6ce3190c195fc2d22bfbab99e
- bef3e6f5851be75415eeb95909377af2
- a72522b93107881ebb4651ad9258bce2
- a6de677f5557816f8bddf306c81eaebc
SHA-256
- 55554c599507947c5eb96264a7db9acaa65d2b42742b39b15686836d0fac2ba0
- a03c968ed6f639f766cf562493a90ae7a61e909d99e098aea2abbbf607003337
- 43e19c7bbaf2d85c3952c4f28cb11ff3c711c3bb0d8396b2ac48a9d4efb955e8
- 65d7a2019922d8c97cdc38a2b0f1bb046bf0ec35780847ac5c8fb38469e6cd58
SHA-1
- 2b763a2f9abbb2157a9237c48d56ac985b4a8388
- 943670e1fa503b482c38df29cc9e99c9c2cfd0f7
- 55e3647bb960f0faba06b39a5ddec26485f03c16
- 381a8ba257c028e302d6db14170d8c000363d718
URL
- http://keepass.ltd
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Install software exclusively from authorized app stores like the Play Store or iOS App Store.
- Implement robust passwords and enable multi-factor authentication whenever feasible.
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets
- Ensure that Google Play Protect is consistently activated on Android devices.
- Exercise discretion when granting permissions to applications.
- Regularly update devices, operating systems, and applications to maintain optimal security.
- Along with network and system hardening, code hardening should be implemented within the organization so that their websites and software are secure. Use testing tools to detect any vulnerabilities in the deployed codes.
- Maintain up-to-date patches and antivirus software to prevent the exploitation of known vulnerabilities.
- Organizations should conduct regular vulnerability assessments and penetration testing to identify and mitigate potential security weaknesses.
- Implement robust security measures such as two-factor authentication, endpoint detection and response (EDR) tools, and employee security awareness training.

