Severity
Medium
Analysis Summary
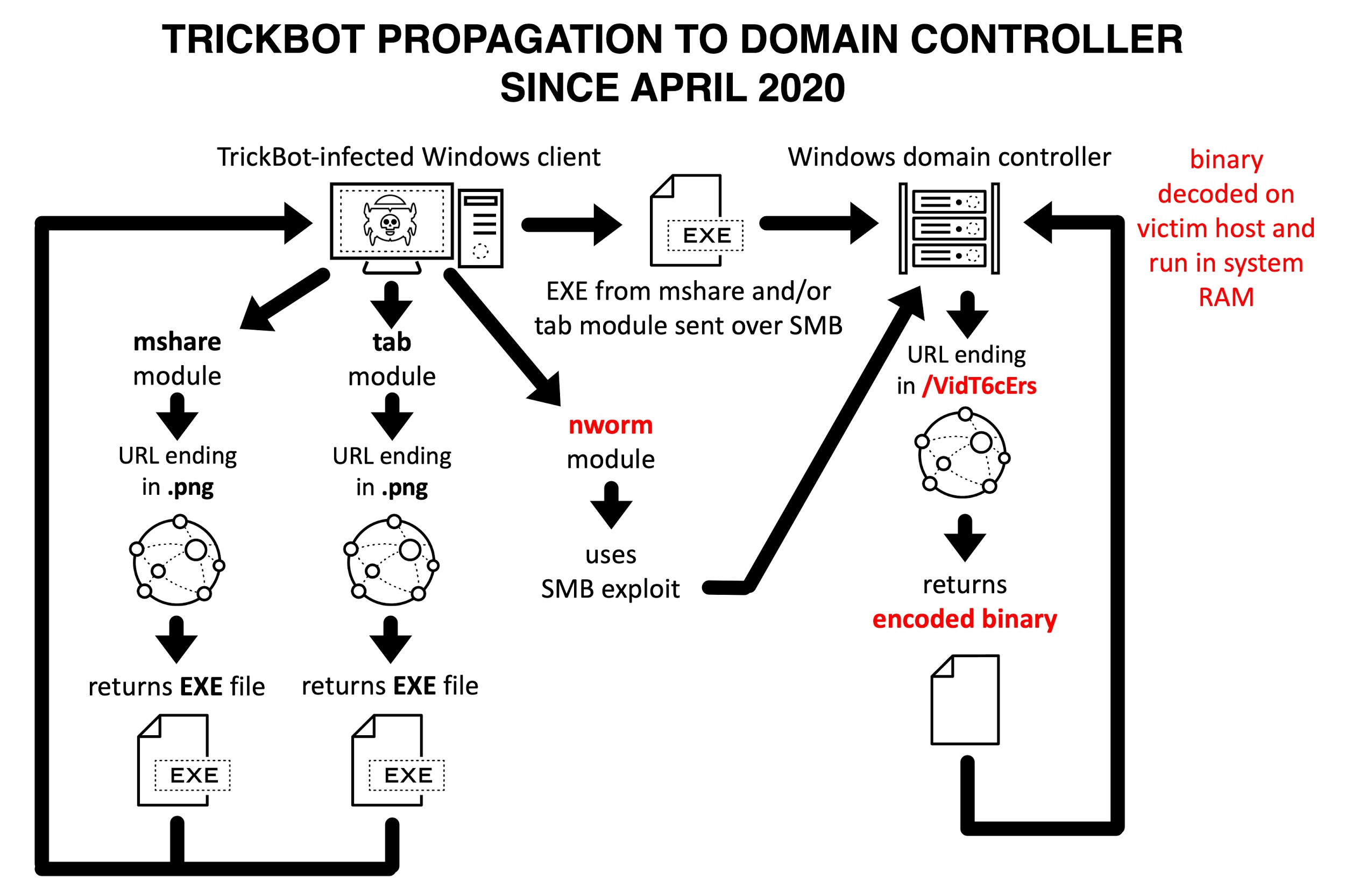
Trickbot, a modular malware using various binaries to perform differing functions has been updated. One module, “mworm” has been updated to “nworm” in an effort to leave no artifacts on infected DCs which disappear after reboot or shutdown. Other differences include retrieval of an encrypted and encoded binary representing a TrickBot executable file. Previously, “mworm” would be retrieved unencrypted and unencoded. Additionally, “nworm” is run from system RAM and does not contain persistence. This evolutionary change allows for TrickBot to remain hidden and, thus, difficult to analyze since no remnants remain on the infected machine. As with previous iterations of TrickBot, it is a malicious Windows executable saved to disk. This EXE is often called TrickBot loader as it is used to load TrickBot modules, such as “nworm.” The URLs presented by TrickBot appeared in the form of IP addresses rather than the typical URLs. “mworm” stopped being presented in April 2020 and was replaced by “nworm.” Two other modules remain the same and perform as previously seen; “mshare” and “tab” remain persistent on the DC.
Impact
- Credential theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- 53bea2686837735d76e7f8b42ec100f6
- 6892e13a05f90fd584c4a3762258785b
SHA-256
- 85d88129eab948d44bb9999774869449ab671b4d1df3c593731102592ce93a70
- 900aa025bf770102428350e584e8110342a70159ef2f92a9bfd651c5d8e5f76b
SHA1
- 1f42b249b783a256995145a59d80ad502fdd3578
- 623d448a9054af73b323e41e5c84218fefc09d99
URL
- hxxp[:]//107[.]172[.]221[.]106/ico/VidT6cErs
- hxxp[:]//107[.]172[.]221[.]106/images/cursor[.]png
- hxxp[:]//107[.]172[.]221[.]106/images/imgpaper[.]png
- hxxp[:]//23[.]95[.]227[.]159/ico/VidT6cErs
- hxxp[:]//23[.]95[.]227[.]159/images/cursor[.]png
- hxxp[:]//23[.]95[.]227[.]159/images/imgpaper[.]png
Remediation
- Block all threat indicators at your respective controls.
- Check for IOC’s in your existing environment.

