Severity
High
Analysis Summary
Recently the cybersecurity researchers reported a phishing campaign targeting WordPress users. The fraudulent email, posing as WordPress, falsely warns of a non-existent Remote Code Execution vulnerability (CVE-2023-45124) on the user’s site. The email urges recipients to download a supposed “Patch” plugin, potentially leading to a malicious installation. Users are advised to exercise caution and verify such communications to avoid falling victim to the phishing attempt.
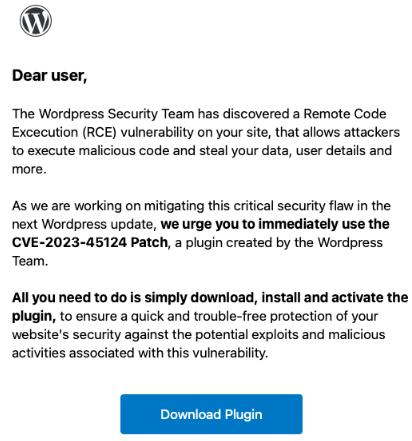
source: phishing email
The Download Plugin link redirects the victim to a convincing fake landing page at en-gb-wordpress[.]org:
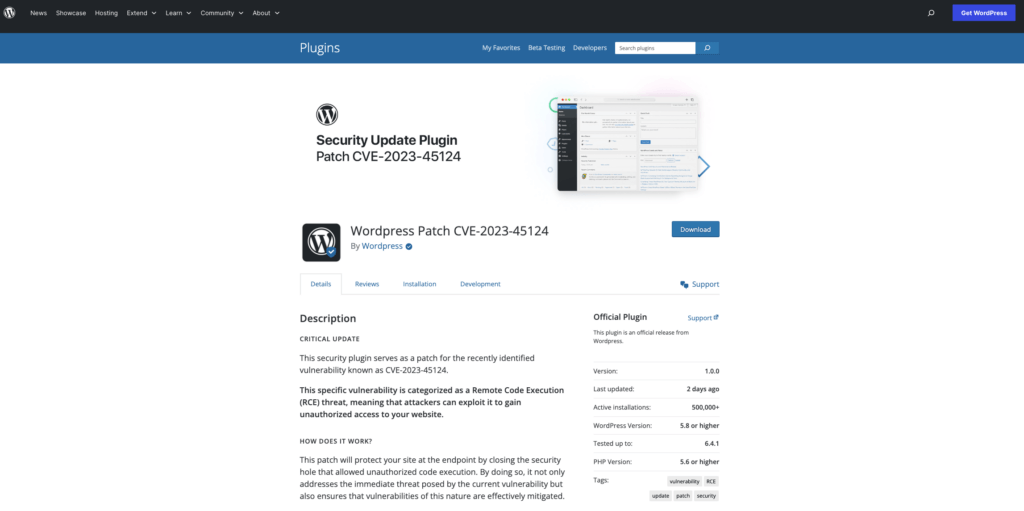
Upon downloading and installing the malicious plugin with the slug “wpress-security-wordpress,” victims unwittingly create a threat to their WordPress site. The plugin, once installed, introduces a nefarious administrator user named “wpsecuritypatch.” This user’s credentials, along with the site URL, are sent to a command-and-control (C2) domain: wpgate[.]zip. The plugin ensures the covert presence of this user. Furthermore, it fetches an additional backdoor from wpgate[.]zip, saving it as wp-autoload.php in the webroot. This secondary backdoor comes equipped with a hardcoded password and features such as a file manager, SQL Client, PHP Console, Command Line Terminal, and the display of server environment information. The intricate attack poses a severe security risk, emphasizing the importance of vigilant measures and caution when handling plugins in the WordPress environment. Users are urged to stay informed about potential threats and adopt security practices to prevent unauthorized access and malicious activities on their websites.
This gives attackers complete control over both the WordPress website and the web user account on the server, enabling them to retain persistence through a variety of access methods, researchers mentioned.
Impact
- Remote Code Execution
- Unauthorized Access
Indicators of Compromise
Domain Name
- wpgate.zip
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Always verify the legitimacy of emails, especially those claiming to be from WordPress or any security authority. Check the sender’s email address and be cautious of unexpected or unsolicited communications.
- Verify the domain of any URLs provided in the email.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.
- Implement advanced email filtering solutions that can detect and block phishing emails before they reach users’ inboxes.
- Enhance the security of your WordPress site by implementing two-factor authentication.
- Keep your WordPress core and all installed plugins up to date.
- Conduct regular security audits of your WordPress site.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Maintain daily backups of all computer networks and servers.
- Keep all software, operating systems, and applications up to date with the latest security patches.
- Continuously monitor network and system logs for unusual or suspicious activities.
- Review and secure website code to prevent open redirect vulnerabilities.
- Educate all site administrators about security best practices and the potential risks associated with phishing emails, fake security advisories, and malicious plugins.

