Severity
High
Analysis Summary
Sodinokibi ransomware was found infecting systems via Microsoft Office documents. After encryption, the following ransom note is found on infected systems.
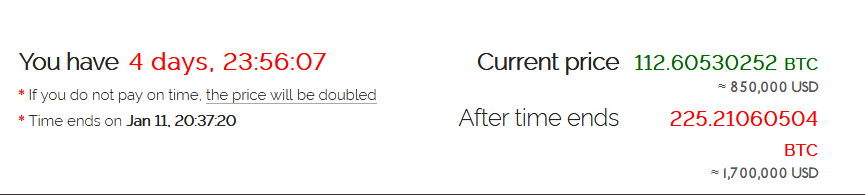
The ransomware demands a ransom of $850k or $1.7m for decrypting the files on target system, as below.
Impact
- Files Encryption
- Information Disclosure
Indicators of Compromise
MD5
- 4903f3effb98da65c49bb9591c16615d
- 3ad4c27f8d0e7135f401474811bd9b25
- 853ab7bdeecf03306178f4af40eff694
- b4fe61c29e23014fdab44ad0d8df1d2d
- 395015986431f15f5bfd25aa1966ccb0
- 27c8b1cb19c4f6df337dff38ab1f3592
- 85de4dc5e49dbafcf3da67434f013733
- a63cdd7c9362540da0fc61db193f9a93
- 6a85fe97ccaa29d09e5df824d4eaad59
- 8b24ea434d60f99e1ff50810fb8d28da
- d8e850611733076fc9d523b586e76ff7
- f45b3caa097afbdd50358ede4042a88f
- 6640d80b412edfbdd836a5c3808a7748
- 722e15d85827d3ac13e56e8108688012
- 9d78f811a13af1cee9ee635a9dd3f10a
- 1ebf922138d1d821c11bac32b63d3b2d
- c932f03098bcfea3f7a6c7bf11c0d653
- 6bf8720c0741f11219f38e747392b73e
- c37804708ee284575f87bd0e365be9d9
- 3846bbbb0efc50218aedd4a4ef3d877a
- f7f3fd2b59b0979bb7c8265122547f9a
- b64f01f8a72ec9c9670909b4ce1a9b4f
- c12c84d72868e4c4be6af913d62da2bb
- 4fe625f696602d23e0c1129ee8c609c9
- 579ebea24bc90cf01b7ba3e6c376f06b
- 6df070be3d54fb2f6eb4ac1a3415857b
SHA-256
- 42996516b6604ba136ff909d9b59d2a676a72eaafa30c729cdfaddd96b20fc83
- 2011f4ed15d6ad002670fdfe8fffc2fbd7cff4c8e7bd9d16746f9884a79a24b1
- 5cb49636a0d759cf24bd19ce17003a62f1e8d4d076844b9110af8b9172413508
- 12bb06bc5da9d7f24634bb37a809ad69896c2eb47b7957846124fe09fbf573bf
- 0e468c960706b3f4181f54a35650b8edbd0960785dda89a72cdd1e5d600f188b
- 9a253acfa25c1feefe603a9b8060d997c34aa110f0d1811005eb1f5ca28d2795
- 7549bc8a7c896dae3f1026dfeeba7d4e0990b896e8715cef55f88763b2aa3908
- ba68f6b7d0be7f6abcbd6679627ed61fac0d0044f05ddbca38b564f1b27bef48
- c678c05b05790006e56a25659eaa97520f426c6b2bbd7ccfb3ea30cc46d672f9
- 5bfb1237443e270d7297a9bb2d4cc44cbc4f3ad0f71db00012a4cc0ae461e6d2
- b7e7878b4f87f1b29fb3c7002d90196c69bffe1eb70ae08d2563b79e1bc41a06
- 9106117da853d8baa45ff6fdbf1ceada81dd4c2ce896787e445170a8d8c13148
- a4b205d9ebfe4b6b08f4ead27a79aea247215df4463f9e95c9cfe1db7b30b02a
- 578e1b00157447f99716b646af6b0c33d0f6c32257a19376d6cc9d003ff0fba1
- b7b136e1efb27c05f80163b6ba73575b4430d7326b07cb629d23794f0049c1a6
- 68a35bd6540394cd28a8c8271dbf2befc4a839aa53d1ba28f9ed81f411a09c01
- 515e79a2813ecc480d47480275b18426e281d77488ac2dce669f00dc41d4b6ce
- 1e1589de70ea7ebad976aa1c1ebdb32e0695ee268aa5f7f8ac834ed3960a4803
- d6a0b7812b3ee8fbf81d40db94094facc25645689f4109e5d7983e8cb49990ec
- 4c15a0bfdc8af00dd509aa990c2d7926ee7c714da88a767ee7f4e5276094de6d
- bb7707d5672a409d7b69356ca1f2ed947bc5c76a683431c8b636e60845fa17ed
- 4d7bb7fc137d4e4db98835612daa8e4f36b365dad71bd5c763521d7e8a29915a
- f4e2cf1a788a104226e6c577ad19c8570624371f8563a3ec0e9cb43501c18665
- 9bc861c341955bbbb8ac281b7195ee238b068981b7212375c93e6e4cd5ff2a04
- 830a8208fe916dabfc1ee63c3e889d8277fbae954a9b00d64b2c920e1d9a2536
- a49fe8df263baded151476232daafd20122f7a66325c2fc6395c965296a8d746
Remediation
- Block the threat indicators at their respective controls.
- Do not download files from random sources on the internet.
- Do not download files attached in emails coming from untrusted sources.

