Severity
High
Analysis Summary
Raspberry Robin, once a USB-borne worm, has emerged as a more sophisticated and concerning threat. Recent developments reveal an alarming evolution in its capabilities, demanding immediate attention from organizations. The malware now leverages unpublished “0-day” exploits, granting it access to vulnerabilities before security patches are available. This grants it a significant advantage in breaching systems and bypassing traditional defenses.
Researchers have discovered that Raspberry Robin now utilizes Discord, a popular online platform, to distribute malicious payloads. This shows that the malware has shifted its tactics and is no longer just lurking on USB drives. Now, it hides inside seemingly harmless archive files downloaded from Discord. These archives contain a legitimate Microsoft program (OleView.exe) alongside a malicious, signed DLL disguised as another legitimate file. When OleView launches, it loads the hidden DLL, unleashing the malware. This sneaky trick leverages users’ trust in both the program and the signature, making it harder to detect.
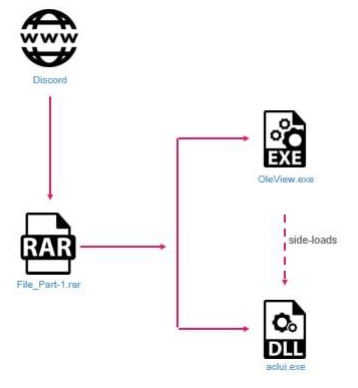
These advancements show a significant leap in Raspberry Robin’s threat level. Organizations must recognize this evolving danger and take immediate action to prioritize patching. Ensure that systems are updated with the latest security patches, especially for vulnerabilities targeted by Raspberry Robin (CVE-2023-36802 and CVE-2023-29360).
Raspberry Robin continues to evolve, using different exploits for vulnerabilities shortly after they’re disclosed for example, it exploited CVE-2023-36802, a Windows vulnerability, even before it was publicly disclosed. In one instance, an exploit for CVE-2023-36802 was sold on the dark web months before it was officially acknowledged. Raspberry Robin previously used exploits for CVE2023-29360 and CVE-2021-1732 shortly after their disclosure. The malware’s ability to quickly utilize these exploits increases its threat level.
Raspberry Robin utilizes Discord for stealthier distribution to propagate malicious payloads. This tactic leverages social interactions and makes detection more challenging, as downloads might appear legitimate within conversations. The incorporation of new local privilege escalation (LPE) exploits allows the malware to gain higher access within compromised systems. This grants it control over critical functions and facilitates further lateral movement across networks, expanding its potential damage.
The advanced malware also uses PAExec.exe for lateral movement instead of PsExec.exe. PAExec.exe is less recognized than PsExec.exe, allowing for stealthier movement within networks. Raspberry Robin’s communication method involves attempting to contact legitimate Tor domains before connecting to C2 servers. If no response is received, it avoids communicating with the real C2 servers.
Organizations need to educate their employees about social engineering tactics and the dangers of downloading unknown files, even from seemingly trusted sources like Discord. Traditional security measures might not be enough. Consider advanced solutions capable of detecting and neutralizing sophisticated threats.
Impact
- Sensitive Data Theft
- Unauthorized Access
- Privilege Escalation
Indicators of Compromise
MD5
- 44a2db5100969f92fe9d6ac24532ed57
- 8fcebbb2c052b5ebb719dc1848068d4c
- 6d318ff2678b1220beeaec046bae7630
- 019c5c8d20f254c205461d6b6cf7999a
- 8183a631688475883230373d637eb333
- b63f1216d13bcae5140f62f757203efc
- 124647404628e55ef763d14c3547cabe
- 47542011329eb8bf8b89e6eb78aff721
SHA-256
- 7e8315426befbcf3a2fca9a3ad4d0f072d9a184467ae7939920389b4a89f5116
- 07e5004a0a3a9129560237ab22d73f44d263204c5b6e15bbb7f17cd6171c87e1
- c0c92c3c7925965e6b1131e36d76c97f6719bb37c0cedbeab3e906bf600fcef0
- 697c15125b83c58c29d4235fd7b37c3f48c10630046be4952c220a4631acf05b
- c6074b63c0ad279ae67a54677a8f037775c6dfbcf9085a0ff0c2a63245b60093
- f856db3dc69a1b816804a021e6e458ba4b3bf9a93e7fe2e0b57725ebdff1819d
- 189f22d5372806c1faaec4d89aaf8bc6837ce653281248d4fc90126d8a6755d0
- 1235a8b1f7484da4a7efbae115f56b521dd3028b752786656498ec07e156f853
SHA-1
- 7ca1236f5dfd61b7d6913b3178db8d5bc3cbcf0a
- 8da8e6fcaee588a5434141ca1f1d68b3db398a87
- 8e92079064dc500c852e8b3bb500cc2f5baa4fbe
- a779795179fa3c5728e94080ac9d551ea09a6671
- 02d9c68f076a47b627574d8a0f68463be4c3b4bf
- 7761a4f710e8951a37c40547341ada954b646ea5
- c55ce97266be01e64aa20fd5e82efa96b259a70f
- cf18db4167f46033209362d7c66131daad6fdc96
URL
- https://cdn.discordapp.com/attachments/1162077513514754089/1162934432156631091/Chapter-File1.rar
- https://cdn.discordapp.com/attachments/1161358666172203019/1161672256091607130/File.Part_1.rar
- https://cdn.discordapp.com/attachments/1162077513514754089/1162608133387075706/Part_File-1.rar
- https://cdn.discordapp.com/attachments/1163001512285446147/1163850004423786669/Part.File1.rar
Remediation
- Use Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.
- Ensure that all systems, software, and applications are up-to-date with the latest security patches. Regularly check for and apply updates to eliminate known vulnerabilities that attackers could exploit.
- Educate employees about phishing emails, social engineering tactics, and safe online behavior. Effective training can reduce the likelihood of users inadvertently initiating an attack.
- Regularly back up critical data and systems to offline or isolated storage. Test the backup restoration process to ensure that it is effective in case of an attack.
- Deploy security solutions that utilize behavioral analysis and anomaly detection to identify unusual patterns of activity that may indicate the presence of malware.
- Enforce multi-factor authentication for sensitive accounts, including cryptocurrency wallets and other financial services, to add an extra layer of security against unauthorized access.
- Develop and regularly test an incident response plan to ensure a swift and effective response in case of a security incident.
- Deploy strong endpoint protection solutions that include advanced threat detection, behavior monitoring, and real-time protection against malware and ransomware.
- Employ robust email filtering and anti-phishing solutions to detect and prevent malicious attachments and links from reaching user inboxes.
- Conduct regular penetration testing and security assessments to identify vulnerabilities and weaknesses in your network and systems. Address any findings promptly.
- Thoroughly assess third-party vendors and software before integrating them into your environment. Ensure they have strong security practices and adhere to cybersecurity standards

