Severity
High
Analysis Summary
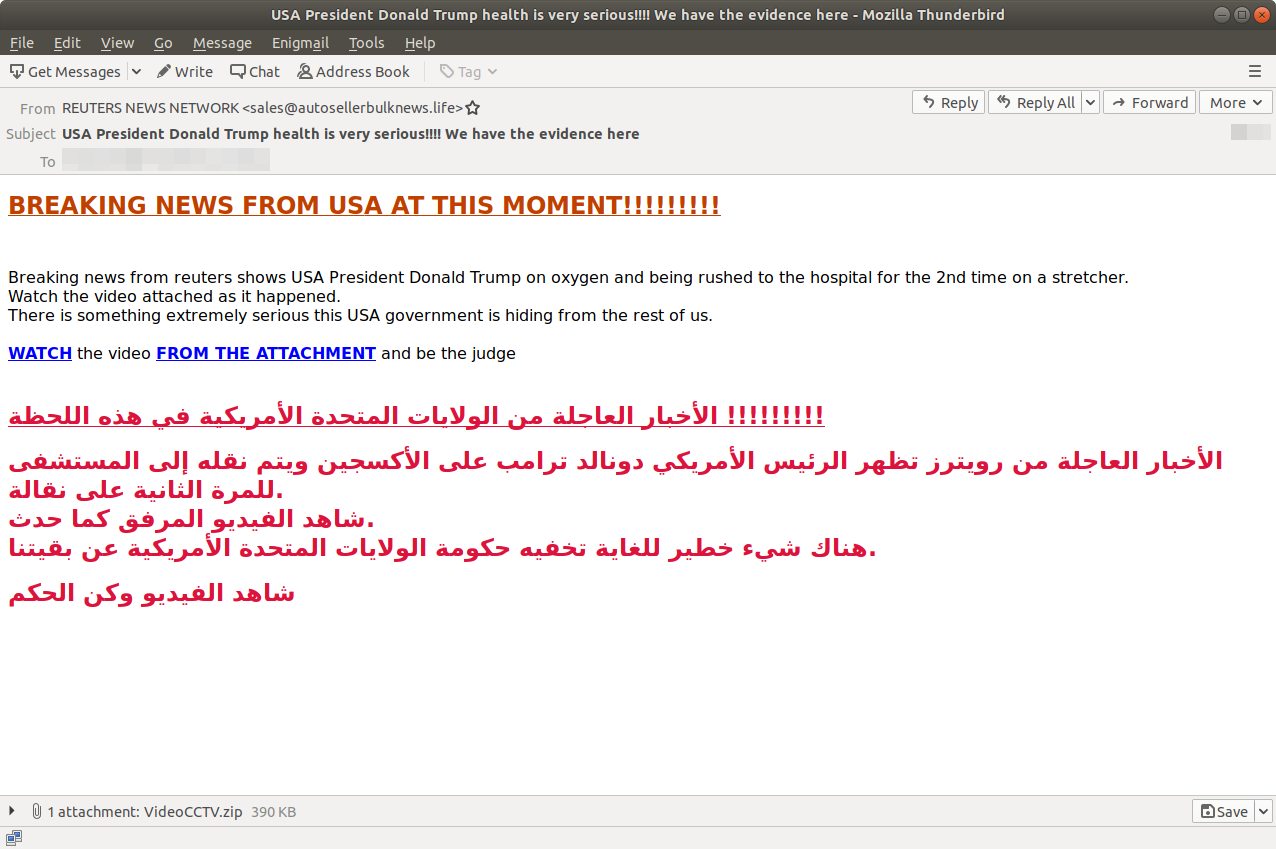
Fake emails have been detected pretending to come from “Reuters News Network”, which is a well known news organization company, using the #COVID19 infection of Donald Trump as a lure to distribute QNodeService RAT. Message body of these phishing emails is in English as well as Arabic. The email claims to break a news from America, about Donald Trump’s health, as the email subject suggests. It has an attachment which is supposed to be a video which in fact is a zip file. The malware has also been used in a Covid-19-themed phishing campaign earlier. Running the file attached in the email led to the download of a new, malware sample written in Node.js; this trojan is dubbed as “QNodeService”.The malware has functionality that enables it to download/upload/execute files, steal credentials from Chrome/Firefox browsers, and perform file management, among other things. It targets Windows systems, but its design and certain pieces of code suggest cross-platform compatibility may be a future goal.
Impact
- Credential Theft
- Data Exfiltration
- Code Execution
- Unauthorized Remote Access
Indicators of Compromise
Domain Name
piolozxx[.]ddns[.]net
Email Subject
USA President Donald Trump health is very serious!!!! We have the evidence here
From Email
sales@autosellerbulknews[.]life
MD5
- c4ceec1bf73783dcb2ee150b771e23a4
- 4589aa06add25d572381c35103b1df8c
- 7125eea628cb4e5c1fb434438a4078d5
SHA-256
- bdc561ae53aa52900af298a57b5e2f920f9cdf74bccf674735dbab318499c2d0
- 5fb3a9eac63a469c8d640cea485939caaebeabe6b56586344941f3329bdea265
- ccc9d33299c1e6c358f925183ec60168764b34b2f824fba218ba41c89b5efc85
SHA1
- 20a9f2f207bbb388076383a0ed2c5205ae299433
- 19a6edd5aa7cd9a1b75543cfade939601dd3a59b
- 42bdf99bde24425de761a6b4313e89cfc7cb8320
URL
http[:]//piolozxx[.]ddns[.]net/
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in untrusted emails.

