Severity
High
Analysis Summary
The BlackCat ransomware group, also known as ALPHV, has been conducting malvertising campaigns to deceive users into visiting fake websites that mimic the official WinSCP file-transfer application’s website. WinSCP is a widely used SFTP, FTP, S3, SCP client, and file manager for Windows. BlackCat uses this legitimate software as a lure to target system administrators, web admins, and IT professionals, aiming to gain initial access to valuable corporate networks.
Analysts discovered this previously unknown infection vector employed by ALPHV. The malicious ads promoting the fake WinSCP pages were found on both Google and Bing search pages. The attack begins when victims search for “WinSCP Download” and click on the malicious ads that appear above the legitimate download sites. These ads redirect users to websites hosting tutorials about automated file transfers using WinSCP.
While these sites don’t contain anything malicious to evade detection by Google’s anti-abuse crawlers, they ultimately redirect users to a clone of the official WinSCP website, featuring a download button. The clone domains resemble the genuine winscp.net domain, such as winsccp[.]com.
When users click the download button, they receive an ISO file containing “setup.exe” and “msi.dll.” The setup.exe acts as a lure, while the msi.dll functions as a malware dropper triggered by the executable. When executed, setup.exe calls msi.dll, which extracts a Python folder from the DLL RCDATA section, creating an appearance of a genuine WinSCP installer. Additionally, the process installs a trojanized python310.dll and establishes persistence by creating a run key named “Python” with the value “C:\Users\Public\Music\python\pythonw.exe.”
The executable pythonw.exe loads an obfuscated python310.dll that contains a Cobalt Strike beacon, enabling communication with a command-and-control (C2) server. With Cobalt Strike active, ALPHV can execute additional scripts, fetch tools for lateral movement within the compromised network, and deepen the compromise. Some of the tools observed in the subsequent phases include AdFind, PowerShell commands, AccessChk64, Findstr, PowerView, Python scripts, PsExec, BitsAdmin, Curl, AnyDesk (abused for persistence), KillAV BAT script, PuTTY Secure Copy client (for exfiltration), and the SpyBoy “Terminator” EDR and antivirus disabler.
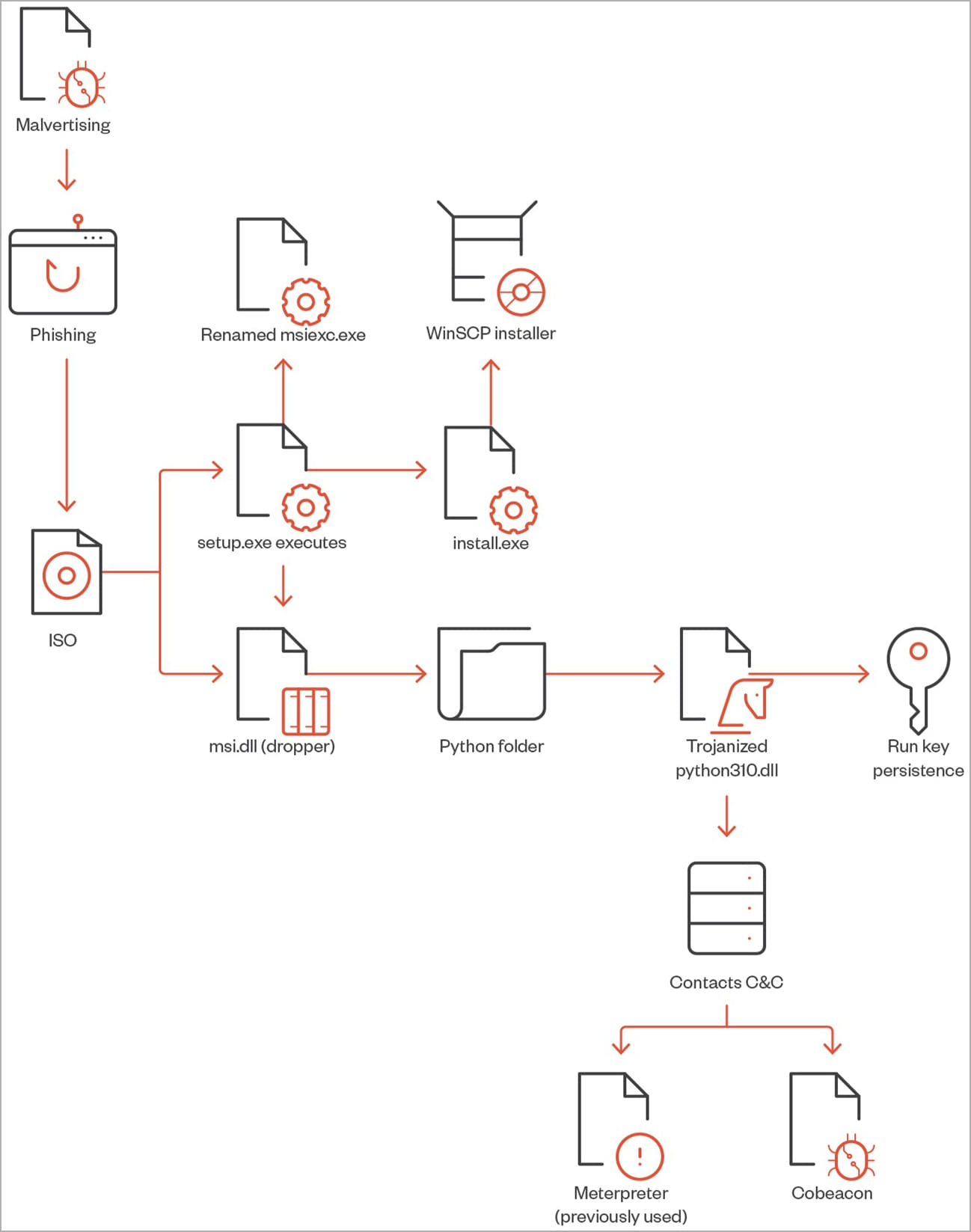
Researchers have linked these tactics, techniques, and procedures (TTPs) to confirmed ALPHV ransomware infections. They also discovered a Clop ransomware file on one of the investigated command-and-control domains, suggesting possible affiliation between ALPHV and multiple ransomware operations.
This detailed information outlines the BlackCat ransomware group’s strategy of using malvertising campaigns to lure users into fake WinSCP pages and their subsequent deployment of Cobalt Strike and various tools to compromise targeted networks and carry out ransomware attacks.
Attackers have become more skilled at exploiting vulnerabilities that victims are unaware of and using tactics that organizations don’t expect. It is important for organizations to continuously work on preventing unauthorized access, but early detection and response are also crucial. Immediate action is necessary to mitigate damage. By understanding attack scenarios, organizations can identify vulnerabilities and take preventive measures to protect against them.
Impact
- Sensitive Information Theft
- File Encryption
- Reputational Damage
- Financial loss
Indicators of Compromise
Domain Name
- aleagroupdevelopment.com
- azurecloudup.online
- cloudupdateservice.online
- devnetapp.com
- situotech.com
IP
- 104.234.11.236
- 157.254.195.108
- 157.254.195.83
- 104.234.11.226
- 141.98.6.56
- 166.0.95.43
- 167.88.164.91
- 193.42.32.143
- 45.12.253.51
- 45.12.253.50
- 45.66.230.215
MD5
- 1e49cdfc621240c2e1ce1c7c735dcf27
- 6c69cceb7541e7bab1986ac54ab396ef
- e80ed5e6c78f16690b8cae9c5bd0f631
- 514a72b9628574eac1dfb7d5061769f6
- b17435075407f7aa9e48e74a426035f7
- 689a0c77af5442657b703e44365bbeb7
- cc83d2123769e0615c4d35fdb24346b6
- 0f9f8018891559f0c48055a74f27425a
- 6f5e7beb8fba48143c95692af66f89d8
- f21106d2f63112f8db10169d503c635a
- d82eaea0554bcc516d43ae3e1615a88a
- 0f7b6bb3a239cf7a668a8625e6332639
- af107f3ce32d6c018cb701aa54a46279
- 70f9bf7caf38a0b864fc190fe238b066
SHA-256
- 25467df66778077cc387f4004f25aa20b1f9caec2e73b9928ec4fe57b6a2f63c
- 4a4d20d107ee8e23ce1ebe387854a4bfe766fc99f359ed18b71d3e01cb158f4a
- 13090722ba985bafcccfb83795ee19fd4ab9490af1368f0e7ea5565315c067fe
- 8859a09fdc94d7048289d2481ede4c98dc342c0a0629cbcef2b91af32d52acb5
- bacbe893b668a63490d2ad045a69b66c96dcacb500803c68a9de6cca944affef
- c7a5a4fb4f680974f3334f14e0349522502b9d5018ec9be42beec5fa8c1597fe
- 3ce4ed3c7bd97b84045bdcfc84d3772b4c3a29392a9a2eee9cc17d8a5e5403ce
- 21e7bcc03c607e69740a99d0e9ae8223486c73af50f4c399c8d30cce4d41e839
- 9e5205865a23c4b8a60935a3fdf1f203286b3e240940bfbeaf0101b00cfc68d6
- d53f1143d5910f025e48389f8ebb5c983007b84f2c485eba7658aa34b74e846e
- 4b8be22b23cd9098218a6f744baeb45c51b6fad6a559b01fe92dbb53c6e2c128
- 18051333e658c4816ff3576a2e9d97fe2a1196ac0ea5ed9ba386c46defafdb88
- 7eade755a832eeaaa1323c8a2126bc9a77195959b49d1899bfd823466175ef70
- 8dfac6521ef877efede0a82bf46d94f590127e2607b78d08321953796fddbba9
SHA-1
- 94e2eb70f2873cdcf967ee526a7e68ae629e3107
- e6e7f30f06b16b8a946a757ff5c19336c12bb41d
- 7254fc0e84357c95a33b100d34bf84c22d1b9f88
- cf9fa97058a4645df43b0d6dcfcdcf663bdef32d
- 6ea353f143f21a339628bfa9422abb06200c06a3
- 52d415ca1ab75236f9fff784e6b83e57f8280506
- 3f6a5bd2e4ff1bf58f85e5a365386ef3a5687a1d
- 1674ba9037321494b08f0a31eda5d1104550b6c6
- aae1b17891ec215a0e238f881be862b4f598e46c
- c82b28daeb33d94ae3cafbc52dbb801c4a5b8cfa
- 5cbb6978c9d01c8a6ea65caccb451bf052ed2acd
- 5263a135f09185aa44f6b73d2f8160f56779706d
- 337ca5eefe18025c6028d617ee76263279650484
- e862f106ed8e737549ed2daa95e5b8d53ed50f87
URL
- http://104.234.147.134/python/python.zip
- https://167.88.164.40/python/python.zip
- http://172.86.123.226/python/python.zip
- https://45.66.230.240/python/python.zip
- https://closeyoueyes.com/python/python.zip
- https://firstclassbale.com/python/python.zip
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Maintain Offline Backups – In a ransomware attack, the adversary will often delete or encrypt backups if they have access to them. That’s why it’s important to keep offline (preferably off-site), encrypted backups of data and test them regularly.
- Conduct regular backups of your important data and ensure that these backups are stored offline or in a separate network. This will help protect your data from being compromised by ransomware attacks.
- Deploy advanced threat detection and monitoring solutions to identify potential ransomware activity in real-time. Monitor network traffic, system logs, and behavior anomalies to detect and respond to ransomware incidents promptly.
- Educate users, especially system administrators and IT professionals, about the risks of downloading software from unofficial sources or clicking on suspicious ads. Encourage them to verify the authenticity of websites before downloading any files.
- Direct users to official software distribution channels or trusted download sources for applications like WinSCP. Emphasize the importance of downloading software from reputable websites to minimize the risk of malware infection.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- If a device on the network has been infected with ransomware, immediately disconnect it from the network to prevent the malware from spreading to other devices. This will help contain the attack and limit further damage.
- Employ web filtering solutions that can identify and block malicious ads or websites. These solutions can prevent users from accessing malicious sites and clicking on potentially harmful links.
- Deploy a centralized logging system to collect and analyze logs from various network devices and systems. This will enable real-time monitoring of network traffic, user activities, and system logs to promptly detect any unusual or suspicious behavior.
- Develop a robust incident response plan that outlines the necessary steps and procedures to be followed in the event of a breach. This plan should provide clear guidance on containing and mitigating the incident. Additionally, establish effective communication channels to promptly inform relevant stakeholders, including employees, customers, and regulatory bodies, about any breaches that occur and the measures being taken to address them.
- If your organization lacks the in-house expertise or resources to effectively handle the aftermath of a breach, consider engaging a reputable cybersecurity firm. These professionals can assist with incident response, conduct forensic analysis to determine the scope and impact of the breach, and provide guidance on security improvements to prevent future incidents.

