Severity
High
Analysis Summary
The LockBit ransomware group claimed responsibility for the strike against Entrust (a digital security giant) in June.
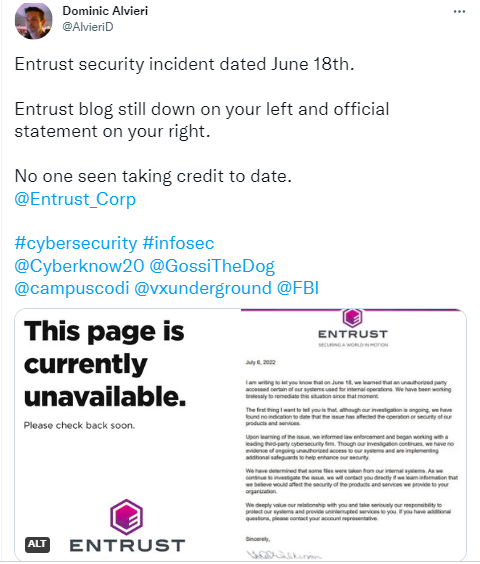
Entrust revealed a cyberattack in June of this year in which some of its data was compromised from its internal systems. Entrust informed its clients that they are investigating into the incident and will get back to them with further details.
“We have determined that some files were taken from our internal systems,” shared by Entrust
While Entrust refused to reveal any specifics about the attack or clarify whether it was ransomware, they did confirm that they were investigating the matter.
“While our investigation is ongoing, we have found no indication to date that the issue has affected the operation or security of our products and services, which are run in separate, air-gapped environments from our internal systems and are fully operational,”
A month later, Vitali Kremez, CEO of AdvIntel, informed that a well-known ransomware gang had infiltrated Entrust after paying for access to the company network through “network access sellers.”
Now Dominic Alvieri, a security expert, recently stated that LockBit was responsible for the earlier attack against Entrust, pointing to a dark website created specifically for exposing the company’s stolen information.
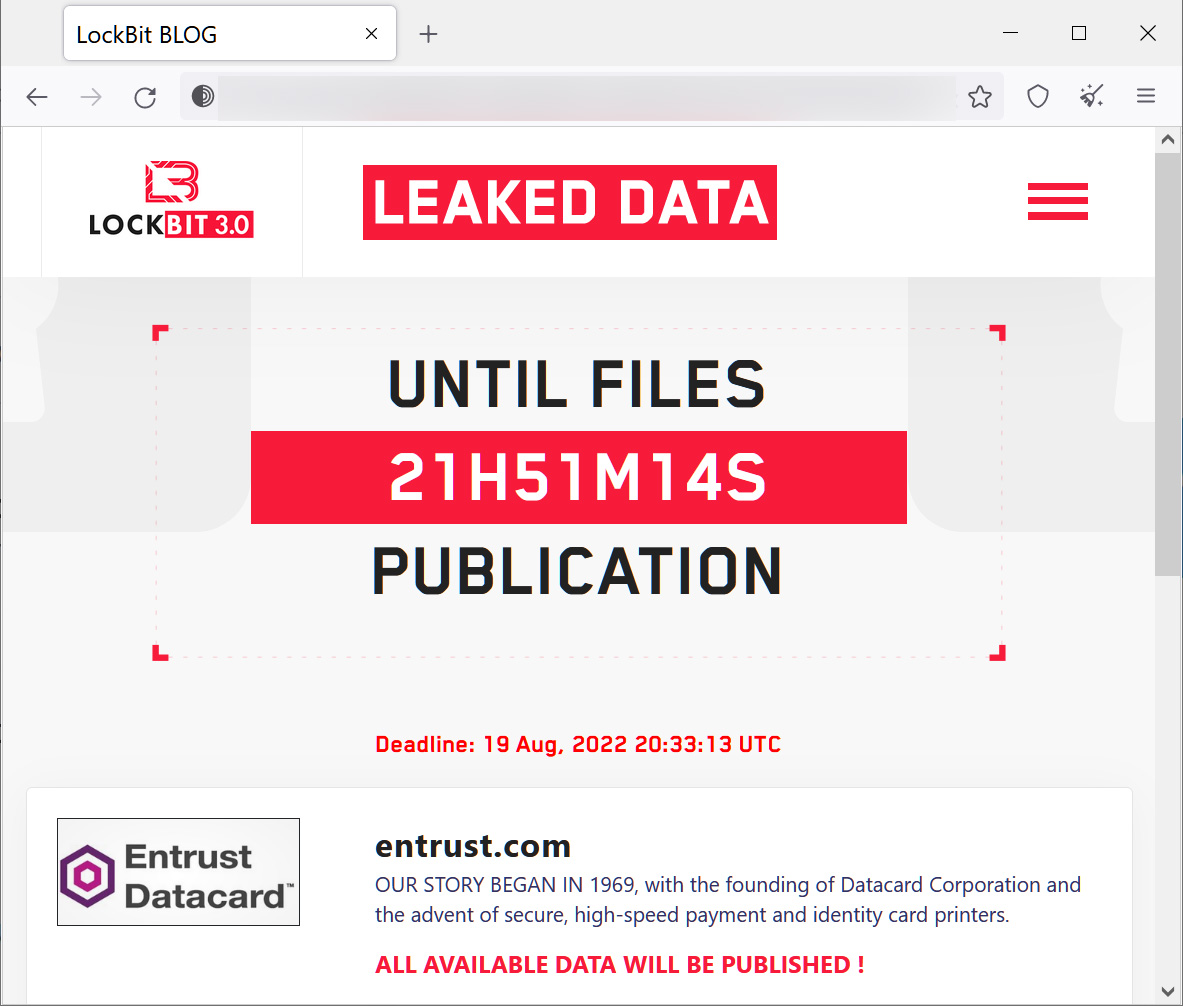
Ransomware gangs typically release data gradually so that the victim would return to the negotiating table when they publish it on their data leak sites.
The LockBit squad created a countdown on their page for the release of all the Entrust data. This leads to conclude that either Entrust has ignored a contract following unsuccessful negotiations or has not replied to LockBit’s ransom demand. Therefore, it is impossible to make inferences about what LockBit obtained from Entrust or determine how sensitive information is.
With a hit list of well-known companies and initiatives like “LockBitSupp” to actively engage with threat actors and cybersecurity researchers, LockBit is one of the most active ransomware operations at the moment. It also runs the first program of its kind in this field, a ransomware bug bounty program.
Due to the adoption of new tactics and techniques, it is critical for security and network professionals to stay up to date on the evolution of the operation and its TTPs.
Impact
- Security Bypass
- Information Theft

