Severity
High
Analysis Summary
Cybersecurity researchers unveiled the latest techniques used by a malware strain dubbed GuLoader. These continuous updates in GuLoader’s obfuscation techniques make it a challenge to analyze the malware, turning it into a resource-intensive and time-consuming process.
“One of these recent changes is the addition of exceptions to its Vectored Exception Handler (VEH) in a fresh campaign, adding more complexity to its already long list of anti-analysis tricks,” said the threat hunters.
GuLoader (aka CloudEyE) was first discovered in 2019 as an advanced shellcode-based malware downloader used to spread a variety of payloads like information stealers, featuring a lot of sophisticated anti-analysis techniques used to evade detection from antivirus solutions. Constant open-source reporting on the malware in the past few months has shown that its developers have improved their ability to bypass old and new security solutions.
Usually, phishing campaigns are used to distribute GuLoader in which target users are tricked into downloading the malware and executing it through malicious email attachments with ZIP archives or links that contain a Visual Basic Script (VBScript) file. It was also revealed recently that GuLoader is now sold under a new alias on the same platform as Remcos.
One of the latest updates to the malware is an improvement of an anti-analysis technique centered around its Vectored Exception Handling (VEH) ability that was first disclosed by researchers in December 2022. GuLoader uses the VEH technique mainly for hiding the execution flow and to make analysis slower. This method consists of disrupting the normal flow of code execution by adding a large number of exceptions and handling them in a vector exception handler that can transmit control to a dynamic address.
GuLoader is the only malware family that has received constant updates, with DarkGate being another notable example of a remote access trojan (RAT) capable of enabling threat actors to fully compromise the target systems. It is sold as a malware-as-a-service (MaaS) on dark web forums for a fee of $15,000 per month and the malware utilizes phishing emails that contain malicious links for spreading the initial infection vector, which is a Microsoft Software Installer (MSI) or VBScript file.
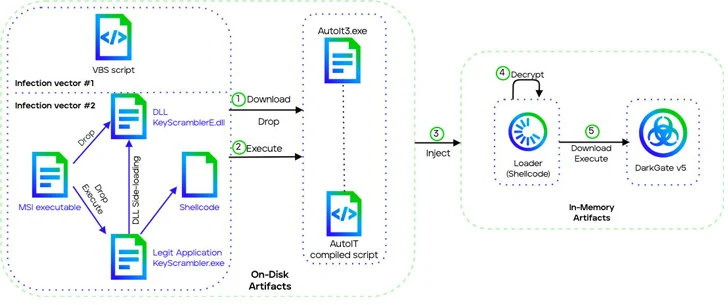
The actors seem to be monitoring threat reports and use them to make fast changes to evade detection. The adaptability, depth of its evasion methods, and the speed at which it changes proceed to show how sophisticated modern malware threats have become.
Impact
- Sensitive Information Theft
- Security Bypass
Indicators of Compromise
MD5
- 9b40ae8c6dc8f35af3535a7b30c51d80
- 0302fdbd19aa907837711dca1d2eaeaa
- ab0a2dc85b78848f7f2bb5e3fab1abea
- 6d17bb6761d398982b36ec58718f48bb
SHA-256
- 6ae7089aa6beaa09b1c3aa3ecf28a884d8ca84f780aab39902223721493b1f99
- 71292d3b2da517ff4f8a8238dc79ff299a3ee60531475ea7c549376a94b34150
- 9d945c09e66b900e545974bb911b9aa97b8132e09b192ed7bf824d7ef53b04db
- f1921797e44af27d89007f013248706f6dd159ee3013c5b5270c7b8aff9caf51
SHA-1
- 6526c781106b303b7f21861e8bcc255d4f356143
- a47f1aa4265224c5ee122b8e949cbac7a1253873
- 821d62c2cdea939acc5097c8992b7c2ef54529dc
- 9d77828cf50c7821abfb904dc355e01708321867
URL
- http://101.99.75.183/MfoGYZkxZIl205.bin
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Emails from unknown senders should always be treated with caution.
- Never trust or open links and attachments received from unknown sources/senders.
- Limit access to administrative accounts and portals to only relevant personnel and make sure they are not publicly accessible.
- Enforced Access Management Policies

