Severity
High
Analysis Summary
Gh0st RAT is a remote administration tool (RAT) that was created by a Chinese hacking group called C. Rufus Security Team in 2008. It was released as open-source software, which made it widely available and easy for threat actors to obtain and customize. Gh0st RAT has a range of features, including surveillance, persistence, and information stealing capabilities. It can be used to remotely access and control infected systems, steal sensitive information, and perform a variety of malicious actions. The tool has been used in various cyber attacks and is a known threat to organizations, particularly those in sensitive industries such as healthcare.
Gh0st RAT has a long history of being used by Chinese nation-state threat actors to target high-value organizations, such as governments, embassies, economic targets, and media. One notable operation was the GhostNet operation in 2009, which used Gh0st RAT to conduct surveillance and espionage on the Dalai Lama’s Tibetan exile centers in multiple countries. Despite being first identified almost 15 years ago, Gh0st RAT is still actively distributed today, as evidenced by the recent phishing campaign targeting a European-owned medical technology organization in China. The malware was delivered via an embedded link affiliated with Tencent and based in Hong Kong, and the C2 server was located on the CHINANET Jiangsu province network in the city of Nanjing. This highlights the ongoing threat posed by Gh0st RAT and the need for organizations to remain vigilant against such attacks.
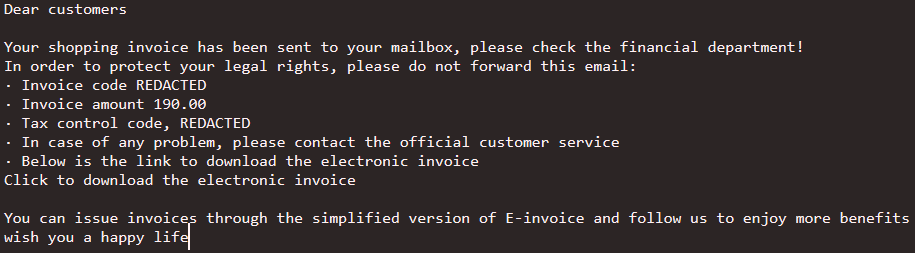
phishing email to deliver Gh0st RAT via an embedded link: source
To protect against Gh0st RAT and other types of malware, it is important to keep your operating system and software up-to-date, use strong passwords and two-factor authentication, and avoid opening suspicious emails or downloading files from untrusted sources. Additionally, using anti-virus software and performing regular system scans can help detect and remove any potential infections.
Impact
- Credential Theft
- Unauthorized Access
- Theft of Sensitive Information
- File manipulation
- Remote command execution
Indicators of Compromise
MD5
- 9e6c45b6b8b20bf3c5959dbba8f27117
- 96e4b47a136910d6f588b40d872e7f9d
- 317f9ff06c076e87e5b1d11242396d5f
- 4723a2a8f68c1eaf82809cff29b8e56f
SHA-256
- a7579376b40d4afb7535df9148b74143d23490c415eae5103de5ea1b3177f2c8
- f788ed739241f79688653d27aeefd18c9d8142a31fe0b5342535e392c040dd9b
- 0e10625daf43a3f4c67f2840ced29d535d0307148819c8ec73a7e76241e9f644
- d817badc2ec3677d18a6b7a3f7c17cee5c768928f8af89fe3427ac4c918f92ee
SHA-1
- 3f92403135c5c9e2c7bba370fcc7a615ab429395
- 0d2eae5df6a4bbf79ec8cd3505d00c4bdabf331e
- 29868086fe5adb4b32c0216d953c419b596246c7
- c74dbcc5f60a3c7ee79932453db4a374fdde58e6
URL
- https://api.youkesdt.asia/admin/down/hash/79b7c6ed-c4d8-4b36-b1cd-f968e6570010
- http://datacache.cloudservicesdevc.tk/picturess/2023/SqlVersion9.dll
- http://61.160.223.114:18076/
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Patch and upgrade any platforms and software timely and make it into a standard security policy.
- Keep your operating system and software up-to-date: Gh0st RAT can exploit vulnerabilities in outdated operating systems and software. By keeping your system up-to-date with the latest security patches and updates, you can reduce the risk of being infected with Gh0st RAT.
- Use strong passwords and two-factor authentication: Strong passwords and two-factor authentication can make it more difficult for attackers to gain unauthorized access to your system.
- Be cautious with email attachments and links: Gh0st RAT can be distributed through phishing emails with malicious attachments or links. Be wary of emails from unknown senders and avoid opening attachments or clicking on links unless you are sure they are safe.
- Use a firewall: A firewall can help block unauthorized traffic from entering your system and prevent Gh0st RAT from connecting to its command and control servers.
- Regularly back up your important data: Backing up your data regularly can help you recover from a Gh0st RAT infection and minimize the impact of any data loss.
- It’s important to note that prevention is key when it comes to Gh0st RAT and other types of malware. By following these remediations and staying vigilant, you can reduce the risk of being infected and protect your system and data.

