Severity
High
Analysis Summary
DeathStalker is a unique threat group that appears to target law firms and companies in the financial sector, as well as others at times. This actor isn’t motivated by financial gain. They don’t deploy ransomware, steal payment information to resell it, or engage in any type of activity commonly associated with the cybercrime underworld. Their interest in gathering sensitive business information shows that it’s a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles. Its intrusion vector is spear-phishing emails with attached archives containing a malicious LNK file that leads to cmd.exe. These shortcut files have the following structure: clicking them initiates a convoluted sequence resulting in the execution of arbitrary code on the victim’s machine. A short PowerShell script, passed through cmd.exe’s arguments, bootstraps the following chain:
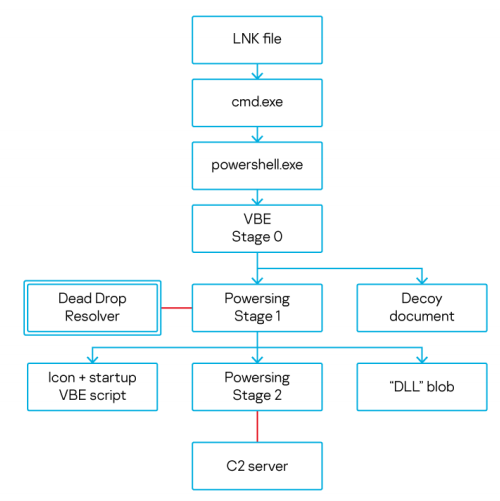
Communications with the C&C server involve the exchange of JSON-encoded objects. Powersing only has two tasks:
- Capture periodic screenshots from the victim’s machine, which are immediately sent to the C&C server (two built-in commands allow operators to change screenshot quality and periodicity)
- Execute arbitrary Powershell scripts provided by the C&C
Impact
- Command execution
- Data exfiltration
- Theft of sensitive business information
Indicators of Compromise
MD5
- d83f933b2a6c307e17438749eda29f02
- d330f1945a39ceb78b716c21b6be5d82
- 3b359a0e279c4e8c5b781e0518320b46
- e1718289718792651fa401c945c17079
- 85ed6ab8f60087e80ab3ff87c15b1174
- 540bc05130424301a8f0543e0240df1d
- 6f965640bc609f9c5b7fea181a2a83ca
SHA-256
- 880607cc2da4c3213ea687dabd7707736a879cc5f2f1d4accf79821e4d24d870
- 5039e8f97dc499fef344b56270ae534a0cea1c93ddacf17ae46c7f922f6139d8
- 22ede766fba7551ad0b71ef568d0e5022378eadbdff55c4a02b42e63fcb3b17c
- 4920e6506ca557d486e6785cb5f7e4b0f4505709ffe8c30070909b040d3c3840
- 7eb4ea6277bd62653cc474cf1125165c9bdc43858811c0d88be25e2ec34bc14d
- 0c7e8427ee61672568983e51bf03e0bcf6f2e9c01d2524d82677b20264b23a3f
- f4610b65eba977b3d13eba5da0e38788a9e796a3e9775dd2b8e37b3085c2e1af
SHA1
- 321d9fd40650b91451742694eb0354f44b6167d9
- 1c1475d89505d3f7aa91c584a62d41e9f0111fc0
- a885bc145a3d1cd7e1d226a8dcd5de953c0318dc
- ab23520a9a627fa9b0fd71cfd4be01b752bb47e1
- 6907e717352376e84d410a1e7cc265fcd3d33aef
- d2dc391a9b79caa1239b93817f74a6ded9c5af59
- c5399596240bc764ff7e053fabe14efd08b8d504
Source IP
- 91[.]229[.]77[.]120
- 54[.]38[.]192[.]174
- 91[.]229[.]77[.]240
- 105[.]104[.]10[.]115
- 91[.]229[.]76[.]153
- 91[.]229[.]79[.]120
- 91[.]229[.]76[.]17
Remediation
- Block the threat indicators at their respective controls.
- Do not download files attached in untrusted emails.

