Severity
High
Analysis Summary
Dark Pink is an Advanced Persistent Threat (APT) group that has been identified and tracked by a Threat Intelligence platform. The group has been found to have launched at least seven successful attacks between June and December of 2022, and is believed to be targeting government agencies and military bodies in the APAC region (Cambodia, Indonesia, Malaysia, Philippines, and Vietnam), and one organization in Europe (Bosnia and Herzegovina).
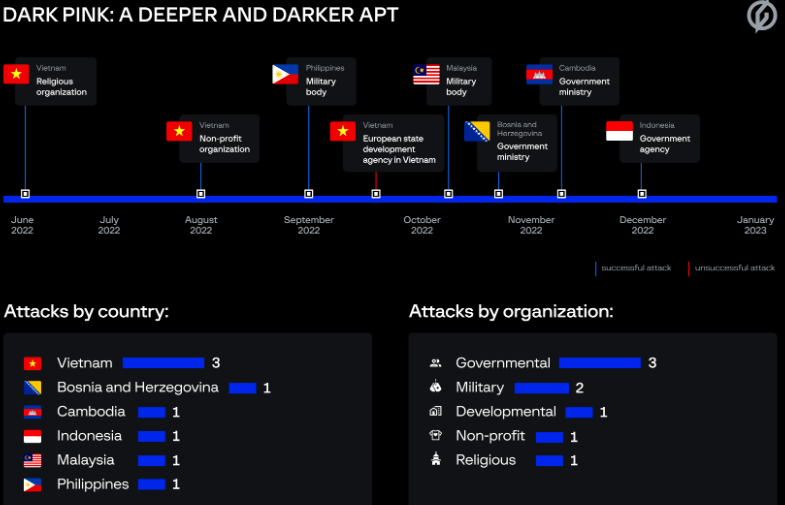
DarkPink APT timeline
Researchers provided more details on the group’s tactics, techniques, and procedures, which involve the use of USB drives to spread malware and steal information.
The primary vector of attack used by Dark Pink is targeted spear-phishing emails, where the threat actors pose as job applicants. The group’s activities include stealing confidential information, exfiltrating data from messengers, and capturing audio from the infected device microphone. This group’s operations have been known to be sophisticated and well-co-ordinated, with a wide range of tools being used to exploit victims
To protect against DarkPink and other APT groups, organizations should implement a robust cybersecurity posture, including regularly patching systems and software, using anti-virus and intrusion detection/prevention systems, and providing security awareness training for employees. In addition, organizations should implement strong access controls, limit the amount of sensitive information that is stored on systems and networks, and regularly monitor their networks for signs of compromise.
Impact
- Confidential Information Theft
- Documents Exfiltration
- Audio Capturing
Indicators of Compromise
MD5
- 3c7eabf0851627dc65bba32aa2ea9c25
- 057477447e3b88dd596369984462d85e
SHA-256
- 34cfef42cdaf9a7fdea54d2be7bcff0a91a418e815bbe9756c91eb067667b9c7
- 73efe4fc5b3426c7dbdb3159c27cc65b81c489638f69912bbc584fdef29c36bf
SHA-1
- 1300bd5c168f2ef40c5ece2cd2018239b272f501
- ad46d337baa8d7cfa882fc16306092a73234a6ba
Remediation
- Block all threat indicators at your respective controls.
- Search for Indicators of compromise (IOCs) in your environment utilizing your respective security controls
- Emails from unknown senders should always be treated with caution.
- Never trust or open ” links and attachments received from unknown sources/senders.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions in a timely manner. Using multi-layered protection is necessary to secure vulnerable assets
- Implement strong access controls, limit the amount of sensitive information that is stored on systems and networks

