Severity
High
Analysis Summary
Gamaredon is a Russia-backed advanced persistent threat (APT) that has been operating since at least 2013. The main goal of this APT is to use the malicious document to gain control of the target machine. The exploit document uses the template injection technique to infect the victim’s computer with further malware. When the document is opened, it connects to the hacker’s server and downloads the payload file. Gamaredon’s tools are simple and designed to collect sensitive information from hacked systems and propagate it further. Its information-gathering efforts are nearly comparable to those of a second-tier APT, whose primary purpose is to collect and disseminate information with their units. The Gamaredon APT group’s current attack leverages a decree document from the Russian Federation government as bait. This APT group continues to target Ukraine, in its latest campaign, threat actors used sfx file disguised as a word icon, clicked to launch batch file to release legal digital signature file VNC remote control. This group has shown no signs of being interested in adopting crimeware tactics to monetize their operation; instead, their primary focus has been on espionage.
Gamaredon APT threat actor has recently started using a new custom information-stealing malware to target employees of the Ukrainian government, defense, and law enforcement institutions.
The group uses malicious LNK files delivered in RAR packages to target users in Ukraine. Threat actors use phishing documents with lures connected to the Russian invasion of Ukraine in order to spread further payloads and exfiltrate data. They utilized VBScript, PowerShell, and LNK files to get initial access to the target before deploying malicious payloads after infection.
Gamaredon APT attackers most likely entered targeted networks by phishing emails that contained malicious Microsoft Office documents. This is in line with the spear-phishing methods used often by this APT. The APT gang uses malicious VBScript macros in weaponized Microsoft Office documents with remote templates. The next-stage malware is downloaded and activated by the macros after they open and download LNK files from RAR packages.
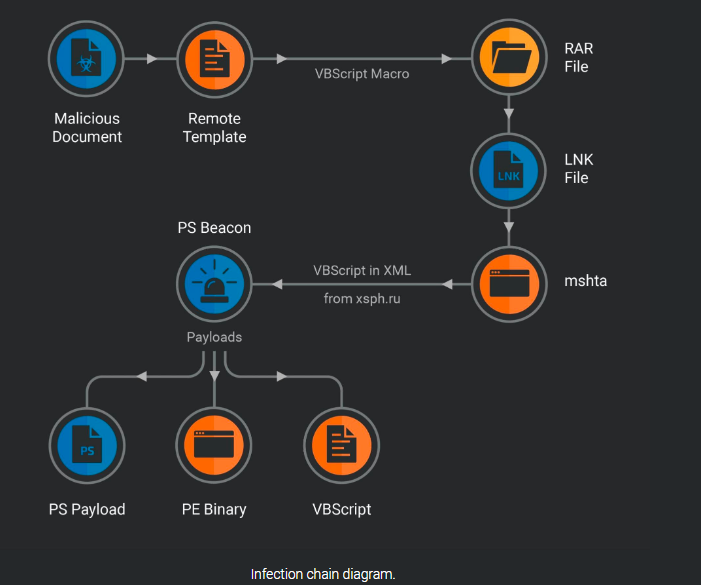
According to researchers,
The infostealer is a dual-purpose malware that includes capabilities for exfiltrating specific file types and deploying additional binary and script-based payloads on an infected endpoint.
One of the executables that the attackers used to spread their malware via the PowerShell script had an information stealer that exfiltrated files with the following extensions from the infected endpoint: doc, .docx, .xls, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z and .mdb.
According to experts, this infostealer was not a part of earlier activities linked to Gamaredon. It is a speculative claim that it could be a component of Gamaredon’s “Giddome” backdoor family, but they do not yet have any supportive evidence.
Once started, the malware scans all attached storage devices looking for files with the aforementioned extensions. For each one, the malware makes a POST request with metadata about the exfiltrated file and its content.” concludes the report
Since its debut in 2013, Gamaredon has continued to be a prolific group that doesn’t seem to be deterred by the raising attention of its actions. This gang has also targeted educational institutions in U.S, European telecom companies, and large hosting companies in Africa.
Impact
- Template Injection
- Exposure of Sensitive Data
Indicators of Compromise
MD5
- defc47401dfb4f80c67550b03bf9a0f3
- 68781941893f72c8f29ae3d3c5318d67
SHA-256
- 5264e8a8571fe0ef689933b8bc2ebe46b985c9263b24ea34e306d54358380cbb
- ff7e8580ce6df5d5f5a2448b4646690a6f6d66b1db37f887b451665f4115d1a2
SHA-1
- 2697274c0fa478e8e81610ad79dcc95405be0803
- 50edf11dd9a5394a353a205571b409d47d15ed59
URL
- http[:]//a0705269[.]xsph[.]ru/instruct/deaf[.]txt
- http[:]//a0705269[.]xsph[.]ru/prok/gur[.]html
- http[:]//a0705581[.]xsph[.]ru/guinea/preservation[.]txt
- http[:]//a0705880[.]xsph[.]ru/band/sentiment[.]txt
- http[:]//a0705880[.]xsph[.]ru/based/pre[.]txt
- http[:]//a0705880[.]xsph[.]ru/selection/seedling[.]txt
- http[:]//a0706248[.]xsph[.]ru/reject/headlong[.]txt
- http[:]//a0707763[.]xsph[.]ru/decipher/prayer[.]txt
Remediation
- Block all threat indicators at your respective controls.
- Search for IOCs in your environment.

