Severity
High
Analysis Summary
Linux servers running unpatched Webmin installations are under attack and slowly getting added to a new peer-to-peer (P2P) botnet dubbed Roboto by security researchers who tracked it for roughly three months.
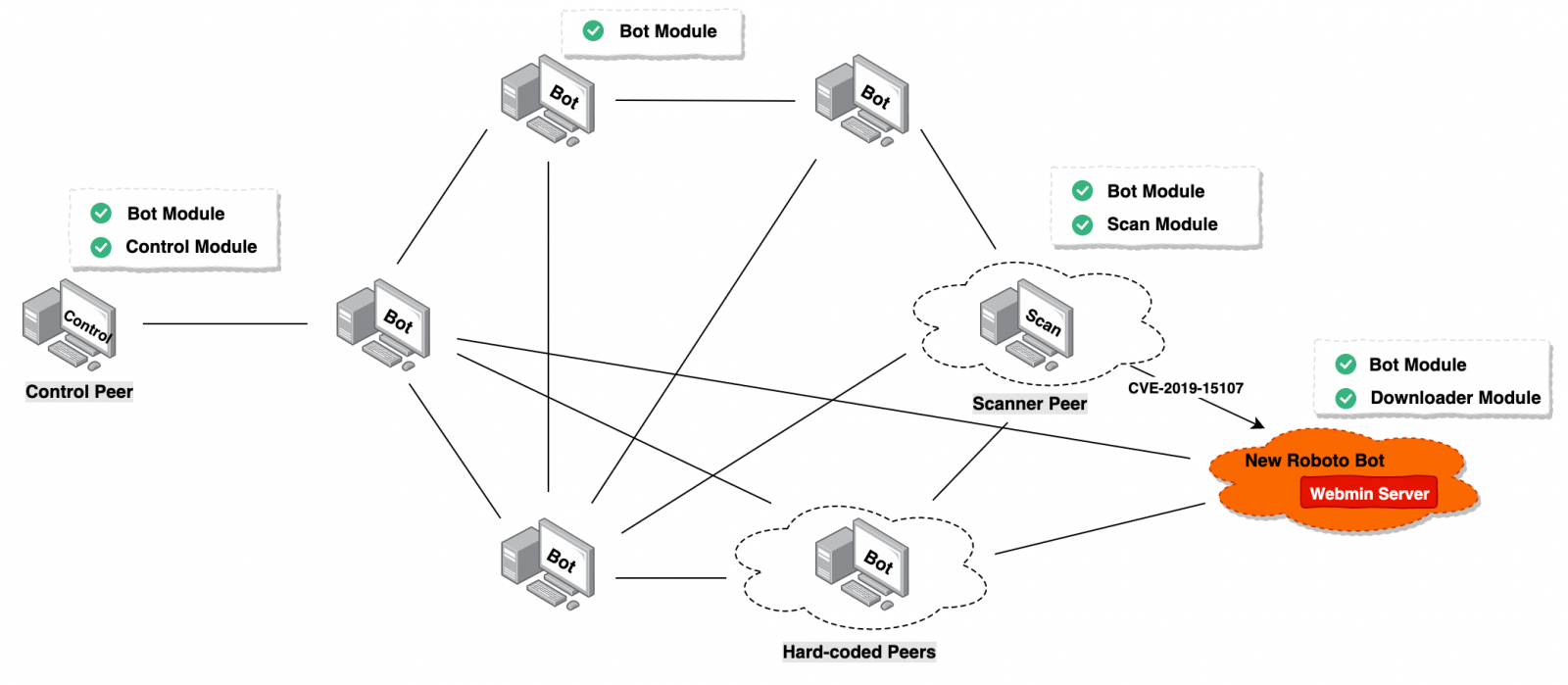
After examining the malware components captured so far, researchers found that the Roboto bots support seven functions, including reverse shell, self uninstall, system command execution, harvesting and exfiltrating process and network information, run encrypted payloads from remote URLs, and launch DDoS attacks.
While the researchers found that the DDoS module supports four types of DDoS attack methods — ICMP Flood, HTTP Flood, TCP Flood, and UDP Flood — depending on the system permissions it can gain on the compromised Linux servers, not even a single Roboto DDoS attack was detected since they started tracking it.
To compromise new systems and add them to the botnet, Roboto exploits a Webmin RCE vulnerability tracked as CVE-2019-15107 to drop its downloader module on Linux servers running vulnerable installations of Unix Webmin web-based system administration tool.
Impact
- Command injection
- Exposure of sensitive information
Affected Vendors
Linux
Affected Products
Webmin
Remediation
- Update to version Webmin 1.930 .
- Disable the user password change option.

