Using an ATM machine is something we all do often but we do not realize the importance of protecting sensitive information while using an ATM. During the past few years ATM skimming has gained a lot of attention as victims suffer, resulting in loss of millions of dollars. Skimming is act of capturing the information or data that is on the magnetic strip of an ATM card through different techniques and further cloning it on a blank ATM card that has a similar magnetic strip which then allows the bad guys to use cards of the victims of ATM skimming.
Bad guys are able to intercept personal identification information using various custom and homemade devices attached to ATM machines. Skimmers use portable data collectors by mounting them over the regular card reading slot where the card is swiped in an ATM machine or fake keypads can be mounted over existing keypads to gather information. After the transaction is complete, the criminal retrieves the device that was placed on the ATM that contains a mini portable storage behind the device that actually captures the information of various ATM users.
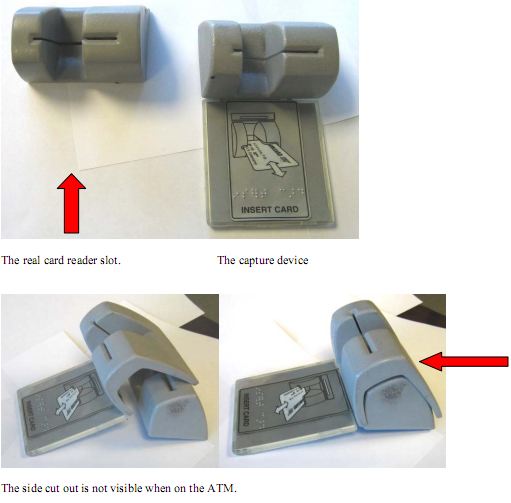
Some of the information that is included on the magnetic strip includes the user’s full name, account number, bank details along with other series of information that is required to allow the card to function properly. As a result, a card that is swiped in a slot that has been tampered gives bad guys the ability to steal large amount of cash. Some of the places where these skimming devices are mounted include the lighting fixtures of an ATM, the brochure plastic case, the ATM card swipe slot itself, and the keypad. Skimmers use a number of ways to gain sensitive information of users. One of the mostly used technique is through the use of spy cameras after mounting the card skimmer in the card swipe slot. One such example is shown in the picture below where the scammer has placed a camera in a small wood box that was then attached to the ATM machine along with the card skimmer.


The following picture shows a closer view of the card skimming device that was attached to the card swipe slot which was aimed to gain and record data from the magnetic strip on the ATM cards. Criminals may then use the financial information gained along with the PIN that is achieved through spy cameras and withdraw cash from accounts of victims.
Only recently did ATM skimming hit Pakistan when a couple of university students in Islamabad designed a skimmer and robbed people off millions of rupees before being caught by the Federal Investigation Agency (FIA). According to the investigative report a total of Rs. 12 million was robbed through a single skimming device which included 187 PSO cards and a second skimming device for 1192 ATM cards. The university students that were held responsible for the crime included, Nasir Abbas, Muhammad, Zaheer Ahmed, Mustaqeem and Amir Shahzad, Javed.
According to the FIA, Zaheer Ahmed owned two skimming devices which caused a loss of almost Rs. 12 million to the government and private sector. The skimmer that Ahmed owned was used to derive information of credit cards through the magnetic strip behind a card which holds the card owner’s details after which a clone of the cards were made and were used for fraudulent reasons or the information derived from the cards were also used to make transactions online. The second skimmer was a device that is mounted to an ATM machine which gathers the information of ATM users once they swipe their cards in the slot along with a device that records the keystrokes entered to gather the personal identity numbers (PINs) of ATM users.
Skimmers are getting better at what they do day by day. Over the past couple of months, new skimming devices have been introduced by criminals which allow skimmers to connect to the devices attached on ATM machines through which wirelessly transmit sensitive information of the victim as soon as he enters.
Skimming is not easy to detect but ATM users can be aware of some signs to prevent being victims of such a crime. There are many ways to protect yourself from becoming a victim. It is very important to observe the ATM machine before swiping your card in i.e. whether the ATM looks normal other than the usual wear and tear markings or is there anything strange in the appearance of the machine such as glue residue, cracks, exposed wires, etc. Check the card device reader; whether it looks normal or seem to have an attached device to it. One of the most important ways that you can protect yourself while using an ATM machine is by covering the keypad when typing in your PIN since if there is any chance of a hidden camera being present your PIN would be protected and the criminals would be unable to gain that very vital information. Also it is very important to always be aware of your surroundings because you may never know who or what can be spying on you.
According to law enforcement, ATM skimming is a process that is hard to track which makes it very attractive for thieves. ATM skimming maybe on the rise but staying informed and educated can reduce the likelihood being swiped by criminals.


