Severity
Medium
Analysis Summary
Infostealer is one of the most profitable tools for cybercriminals, as information gathered from systems infected with this malware could be sold in the cybercrime underground or used for credential stuffing attacks. Researchers came across a new Infostealer called PurpleWave, which is written in C++ and silently installs itself onto a user’s system. It connects to a command and control (C&C) server to send system information and installs new malware onto the infected system.
Upon execution of the PurpleWave binary, it gives a fake error message in the Russian language that can be customized by the attacker in their panel. But in the background, it performs all of its malicious activities.
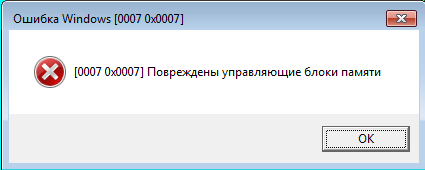
The name of the stealer (PurpleWave) and the version (1.0) are hardcoded and encrypted in the binary. Most of the strings in the binary are encrypted, but they get decrypted on runtime with the help of the decryption loop present in the binary .The PurpleWave binary creates a mutex with the name “MutexCantRepeatThis” to avoid multiple executions of malware instances. After that, it sends the HTTP POST request with the custom header and body to the C&C URL to get the configuration data.
Impact
- Information theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- 9e4d3f4439ed39c01f3346fbdb7488ae
- ac17a56355914e231b2ad52e45d6f779
- 30898909fd4bf93fe23c62e6962bed11
- b5fb35be12c66f16f55af2c2abc77e55
- 394298eed78d455416e1e4cf0deb4802
- b18bcb300ae480b16a0e0b9110e1c06c
- 02350ffa6b82cd2079797ed4ba1dd240
- 01c8d886bd213f983d0fd5ad35d78a9a
- 7a728f42940f5bcb50ac9a5c57c1d361
- e23ded17cdf532790f708e8a550969eb
- 0212eb9562992da05ab28effb9d64d8a
- 53bc8e68a9028c58941b78e4ad867b83
- 657c3ddaff433067c7f74f3453c7eb37
- bc693652d5f57e792551c3a62049ba0b
- e770544551f94296b9a867e42435206f
- ad24a6614c528de81283fe4a618682c7
- d8a36dce73e91780b52b6f387c5cfd78
SHA-256
- a3714c4409ab0020bd29ac0ec2ab5600b1a14de23be9e15b9b7271b0044070da
- d820ec7f9196a5cc3dbc2b5860334a2e174fede80efc3b8463756fb8767dddf9
- eddb45dfe783cb38e0597ba1a04b8fe9cdc126970dba9287f7325e05f62329ce
- 77db7f8715797944c651f23ef60a033b7e84ce76dedabe1e5de359715a8de1aa
- a70bbb5e3e77de0cce83a4631fd8b078d645b33f9578168a7f18734eb4c1f38d
- 4b3cb90581dcd77c9ceffbd662b8dac70b68de5a03cd56940434cc035209d61d
- 7de7b866c46f34be28f7085fb1a1727ab939d65abd3128871fb68c42371af2df
SHA1
- fa2a087f838f4ba878712e604110435d992e0951
- 027ed0ce372846f0906011392d9add7cb8cfdbf9
- 597713b0225680528e9a9154a7acca984ef67075
- d8d97ae6c7356168bde0a4426d4d9dc311921ded
- 3dd8e1d7006eb1f27d54ca6f2c80f1b7dab23706
- 9af3260f4ee0a6318db721d478a39fb91889e717
- 5f40b43fdc5f9303f4107ca4ca17dd3db6025503
URL
- http[:]//bibaiboba[.]beget[.]tech/config
- http[:]//bibaiboba[.]beget[.]tech/gate
- http[:]//h98801x4[.]beget[.]tech/config
- http[:]//h98801x4[.]beget[.]tech/gate
- http[:]//ikaschyn[.]beget[.]tech/config
- http[:]//ikaschyn[.]beget[.]tech/gate
- http[:]//manget6z[.]beget[.]tech/config
- http[:]//manget6z[.]beget[.]tech/gate
- http[:]//sh1213709[.]a[.]had[.]su/config
- http[:]//sh1213709[.]a[.]had[.]su/gate
- http[:]//sh1213709[.]a[.]had[.]su/loader/9ZNzBRpT
- http[:]//sh1213709[.]a[.]had[.]su/loader/Ds5UabYT
- http[:]//sh1213709[.]a[.]had[.]su/loader/Kv2TDW4O
- http[:]//sh1213709[.]a[.]had[.]su/loader/MTIQK8lV
- http[:]//sumakokl[.]beget[.]tech/config
- http[:]//sumakokl[.]beget[.]tech/gate
Remediation
- Block all threat indicators at your respective controls.
- Search for IOCs in your environment.

