Severity
Medium
Analysis Summary
A latest campaign of well-known banking Trojan named Ursnif (aka Gozi aka Dreambot) is active and actively distributing malware featuring a new multistage payload distribution technique. The campaign has switched from using PowerShell in its second-stage payload to mshta. Microsoft HTML Applications (HTAs) are applications that when run by mshta.exe, can use the same models and technologies as those available to Internet Explorer, but without running the browser. Malicious scripts composed of JavaScript or VBScript will function just as if they were being executed by the browser.
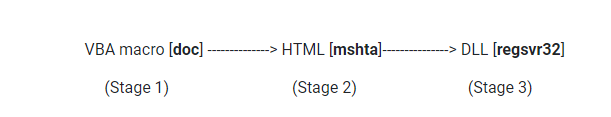
Running under mshta, these HTAs can even bypass application whitelisting solutions and security settings that would normally restrict IE. The infection vector for this campaign was a Word document that contained malicious macros to download and run the second-stage payload. The second stage, after garbage code is removed, boils down to HTML, JavaScript, and ActiveX code. These are used to download the final stage – index.dll
Impact
- Security bypass
- Exposure of sensitive data
Indicators of Compromise
MD5
8212E2522300EF99B03DFA18437FCA40
URL
- hxxp[:]//xolzrorth[.]com/kundru/targen[.]php?l=zoak2[.]cab
- hxxp[:]//grumnoud[.]com/kundru/targen[.]php?l=zoak4[.]cab
- hxxp[:]//gandael6[.]com/kundru/targen[.]php?l=zoak6[.]cab
- hxxp[:]//chersoicryss[.]com/kundru/targen[.]php?l=zoak2[.]cab
- hxxp[:]//xolzrorth[.]com
- hxxp[:]//grumnoud[.]com
- hxxp[:]//gandael6[.]com
- hxxp[:]//chersoicryss[.]com
Remediation
- Block all threat indicators at your respective controls.
- Search for IOC’s in your environment
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.

