Severity
Medium
Analysis Summary
NetWire RAT is a is a publicly available, multiplatform remote administration tool (RAT) that has been used by criminal and APT groups since at least 2012. In this scenario the NetWire RAT is distributed via through GuLoader.using Microsoft Word documents. The chain starts with fake email which contains a web link for a Microsoft Word document. The word document has macro code that retrieves a Windows executable for GuLoader. The executable retrieves an encrypted data file used for NetWire.
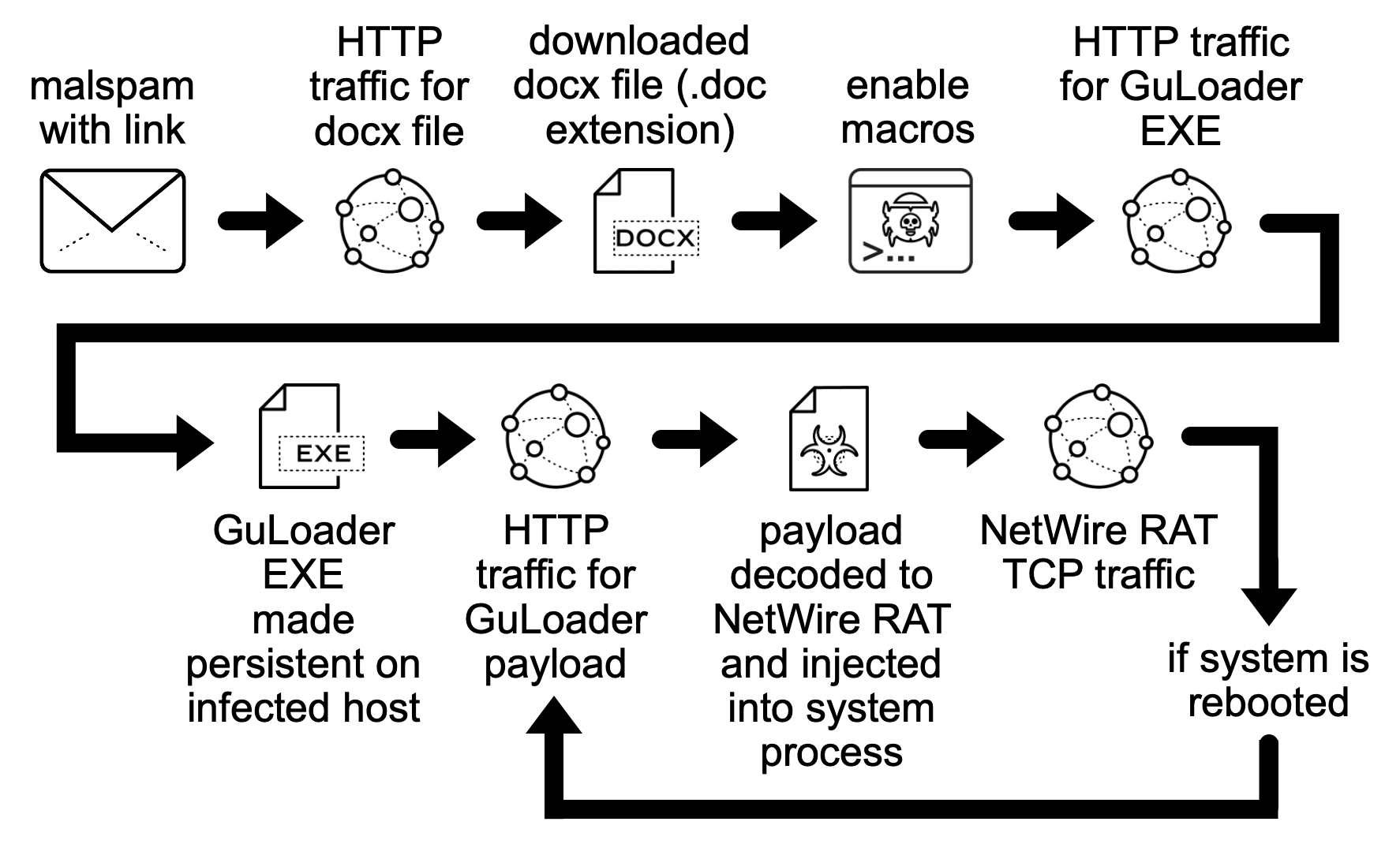
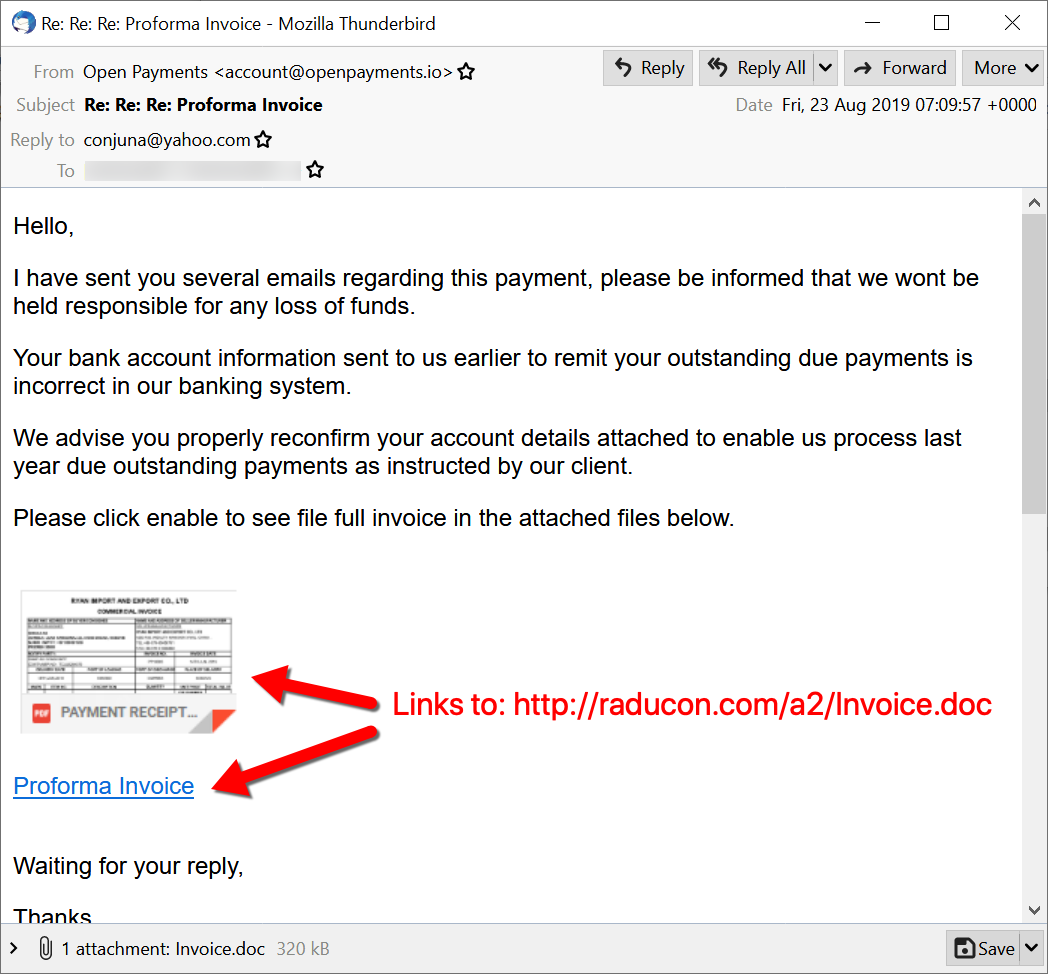
In previous campaigns of Netwire RAT the same procedure has been used to kickoff the infection chain and similar fake emails were followed up with the web links for the users to click on the malicious attachments and lures for malspam pushing NetWIre RAT.
Impact
- Information theft
- Exposure of sensitive data
Indicators of Compromise
MD5
- ae1a12d04352572a7c426a0653bd0996
- 343c3b31aa339ce68e8f7a9454e27e07
- 5599333a0dc6a4f1d5dcafaab6840216
SHA-256
- cc554633c0b734778211a6289e1d6d383d734a3e1a8edeb13d6d0fafc8a2f162
- 661d9c0c23e9c17412eee8d72cc1bb66c1b4e5f73908c8cce48f89420f38b205
- aadc6031fed895de570214afb8b6cdc66f17d01f1df0407f4d57f1d04313ae2b
- 4d373131b0d3254d72f1a06ea168267376b8cc8f805daa53963db5f051631967
- c87e798118a539a136baa0bb9d2539a6e074b0ee640cf0a4ed1ef17936f69ebf
SHA1
- 203d5a5fe71d2d733d9cf9204aeb7e9661410a5a
- 4df8eadb7f64f6582cc6a684586c8b474f077032
- dccc69b8025bfecb73da72853747d1eb5fbf5a73
URL
- http[:]//wwwrossogatocom/ROSSO_encrypted_54E9BA0bin
- http[:]//wwwartizaacom/Andys_18US_Taxdoc
- http[:]//matpincscrcom/tec_encrypted_340BD0bin
- http[:]//saidialxocom/lpexe
- http[:]//murthydigitalscom/PM_2019_Screen_18_Tax_Filedoc
- http[:]//ptgteftcom/Exten/TY1920/TY30exe
Remediation
- Block all threat indicators at your respective controls.
- Always be suspicious about emails sent by unknown senders.
- Never click on the links/attachments sent by unknown senders.

