Severity
High
Analysis Summary
A newly discovered critical zero-day vulnerability tracked as CVE-2025-33073 affects multiple Windows systems and enables attackers to escalate privileges via a novel Reflective Kerberos Relay Attack. Patched by Microsoft on June 10, 2025, this flaw has been assigned a CVSS score of high, highlighting its critical nature due to low attack complexity and high potential impact. The vulnerability allows threat actors to achieve NT AUTHORITY\SYSTEM access, the highest privilege level in Windows, through a sophisticated abuse of Kerberos authentication mechanisms.
According to the Researcher, the attack represents a major evolution in authentication relay techniques, effectively bypassing NTLM reflection protections introduced back in 2008. It begins with authentication coercion, where an attacker forces a Windows system to authenticate back to the attacker’s machine over SMB using its own computer account. The technique leverages a CredUnmarshalTargetInfo/CREDENTIAL_TARGET_INFORMATIONW trick, an approach pioneered by James Forshaw, that decouples the coercion target from the Service Principal Name (SPN), allowing attackers to deceive Kerberos into issuing tickets for a spoofed hostname.
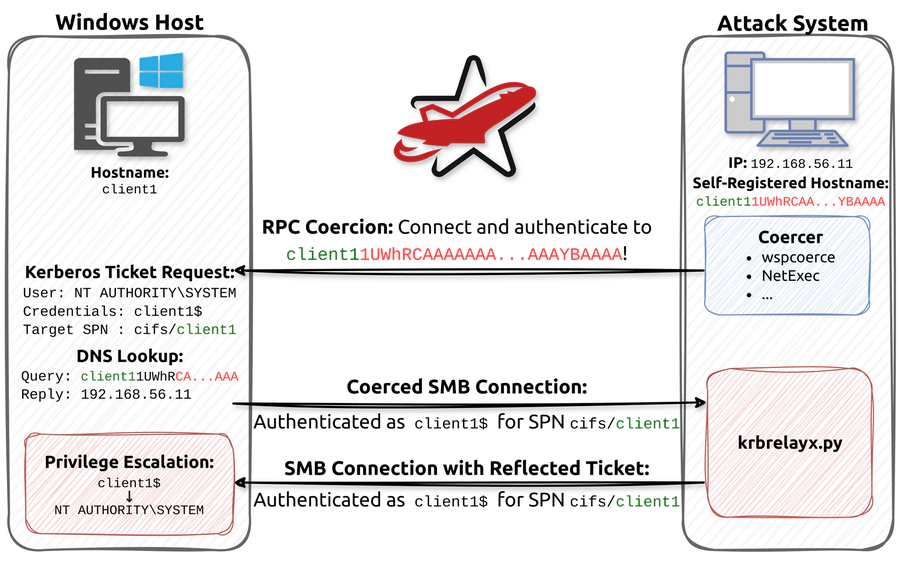
A particularly dangerous outcome of this attack is the unexpected privilege escalation. Normally, relaying a Kerberos ticket from the computer account would yield low privileges. However, in this attack scenario, relaying the ticket back to the originating host tricks the system into granting SYSTEM-level privileges. Researchers believe this is due to how Windows links Kerberos tickets to originating processes via KERB_AD_RESTRICTION_ENTRY and KERB_LOCAL structures. This behavior confuses the security model, causing a low-privileged authentication to inherit SYSTEM-level trust when initiated by a high-privilege process.
The vulnerability affects all Windows 10 versions, Windows 11 (pre-24H2), and Windows Server 2019–2025. While no version is immune without the patch, exploitation depends on the attacker’s ability to coerce SMB authentication and relay Kerberos tickets. The most effective mitigation includes enabling SMB signing (which blocks relaying), Channel Binding, and Extended Protection for Authentication (EPA). These are enforced by default only in newer builds like Windows 11 24H2. Organizations are urged to immediately apply patches and harden their Kerberos and SMB configurations, as this attack underscores the rising threat of advanced Kerberos exploitation techniques in enterprise environments.
Impact
- Sensitive Data Theft
- Privilege Escalation
- Gain Access
- Security Bypass
Indicators of Compromise
CVE
- CVE-2025-33073
Affected Vendors
Microsoft
Affected Products
- Windows 10 (all versions)
- Windows 11 (pre-24H2)
- Windows Server 2019–2025
Remediation
- Use Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
- Enable server-side SMB signing to block SMB relay attacks: Enforced by default on Windows 11 24H2 clients and domain controllers and must be manually enabled on older Windows Server versions.
- Enable Extended Protection for Authentication (EPA) to strengthen session bindings.
- Implement Channel Binding (CB) for Kerberos and NTLM to prevent credential relay misuse.
- Disable or restrict SMBv1 and unnecessary SMB services to reduce the attack surface.
- Use strong network segmentation to isolate sensitive systems and limit lateral movement.
- Harden SPN management and avoid overly permissive Kerberos delegation settings.
- Monitor for unusual SMB or Kerberos traffic patterns, especially involving computer accounts.
- Deploy intrusion detection/prevention systems (IDS/IPS) capable of flagging authentication coercion attempts.
- Train IT and security staff on modern Kerberos and NTLM-based attack techniques for better detection and response.

