Severity
High
Analysis Summary
A new malware campaign named PolarEdge has been observed targeting edge devices from Cisco, ASUS, QNAP, and Synology since late 2023, aiming to integrate them into a botnet. Researchers identified attackers exploiting CVE-2023-20118, a critical vulnerability (CVSS 6.5) affecting Cisco Small Business RV series routers, allowing arbitrary command execution. Since Cisco has not released a patch due to the affected routers being end-of-life (EoL), the company previously recommended disabling remote management and blocking access to ports 443 and 60443 as a workaround.
The infection process involves executing a shell script called "q" via FTP, which downloads a malicious payload ("t.tar") from 119.8.186[.]227 (Huawei Cloud) and extracts a binary named "cipher_log". The malware establishes persistence by modifying system files and continuously executing cipher_log. Once active, PolarEdge enters an infinite loop, establishes a TLS session, spawns child processes, and executes commands sent by the C2 server.
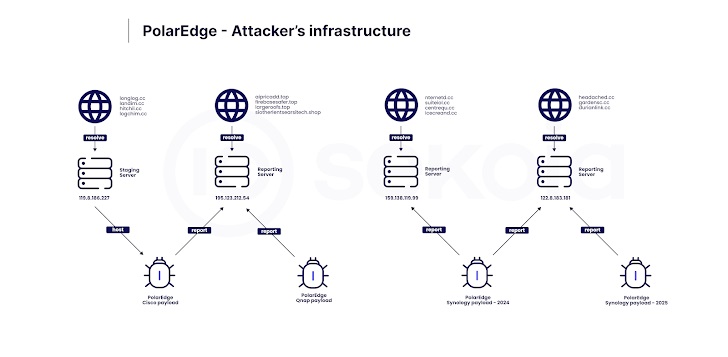
The botnet has already compromised 2,017 devices globally, with the highest concentrations in the U.S., Taiwan, Russia, India, Brazil, Australia, and Argentina. The malware’s exact purpose remains unknown, but researchers suggest it may serve as a relay infrastructure for launching cyberattacks.
Further analysis revealed similar PolarEdge payloads targeting ASUS, QNAP, and Synology devices, uploaded to VirusTotal from Taiwan. The botnet’s complexity and the use of multiple vulnerabilities across different vendors suggest it is operated by sophisticated threat actors.
Separately, Researcher discovered another large botnet comprising 130,000 infected devices, being used to conduct password-spraying attacks against Microsoft 365 (M365) accounts. Attackers exploit non-interactive sign-ins (commonly used for legacy authentication protocols like POP, IMAP, and SMTP), which bypass MFA protections. Stolen credentials from infostealer logs enable unauthorized access to sensitive enterprise data. This Chinese-affiliated campaign, linked to CDS Global Cloud and UCLOUD HK, exploits gaps in security teams' monitoring practices, allowing large-scale credential theft and unauthorized access to corporate accounts.
Both PolarEdge and the M365 botnet attacks highlight evolving threats leveraging unpatched vulnerabilities, weak authentication mechanisms, and cloud-based attack infrastructure to compromise critical systems globally.
Impact
- Data Theft
- Service Disruption
- Unauthorized Access
Indicators of Compromise
CVE
- CVE-2023-20118
IP
159.138.119.99
43.129.205.244
122.8.183.181
195.123.212.54
Remediation
- Disable remote management and block ports 443 and 60443 on Cisco Small Business RV series routers.
- Disable Basic Authentication and enforce Multi-Factor Authentication (MFA) for all accounts.
- Look for unusual activity, unauthorized connections, or signs of persistent malware.
- Although Cisco routers affected by CVE-2023-20118 are no longer supported, update firmware for all other devices where possible.
- If a device is compromised, disconnect it from the network and perform a forensic analysis.
- Deploy endpoint protection, intrusion detection systems (IDS), and firewalls to block malicious traffic.
- Remove any suspicious files like "q", "t.tar", or "cipher log" from infected devices.
- If credentials were exposed, reset passwords and revoke any unauthorized access.
- Maintain secure, offline backups of critical data in case of compromise.
- Follow cybersecurity advisories from Cisco, ASUS, QNAP, Synology, and security firms for future threats and mitigations.

