Severity
High
Analysis Summary
A new hacking group, the "Belsen Group", has leaked sensitive data from over 15,000 FortiGate devices on the dark web, exposing critical technical information to cybercriminals. The leaked data includes:
- Configuration files
- IP addresses
- Passwords
Organized by country and further divided into subfolders for each device's IP address, the 1.6 GB archive contains sensitive details like private keys and firewall rules, significantly compromising the security of affected networks.
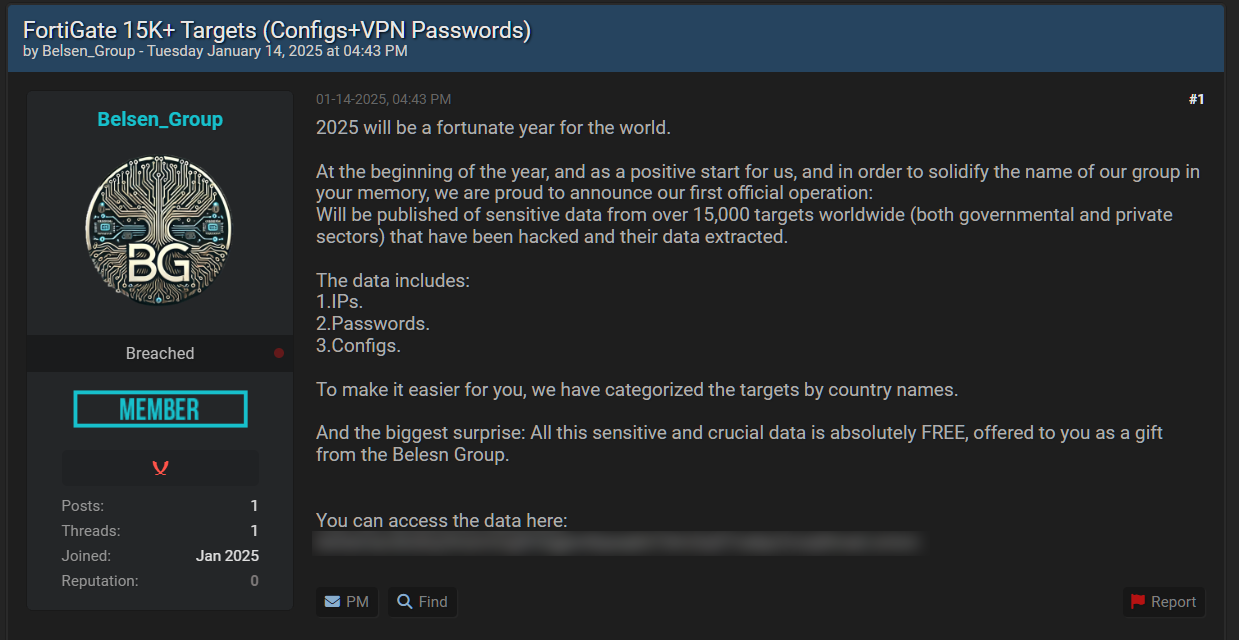
The Belsen Group, which surfaced on cybercrime forums and social media this month, claimed the leak as their inaugural operation. They announced on a hacking forum their intent to release data from over 15,000 global targets across governmental and private sectors. To bolster their reputation, the group posted the data for free on a Tor website, making it accessible to other threat actors.
Cybersecurity Researcher analyzed the data and confirmed that the breach is tied to a 2022 zero-day vulnerability, CVE-2022–40684. This flaw allowed attackers to download configuration files and create a malicious super-admin account, "fortigate-tech-support." The data dump appears to have been assembled in October 2022 when the vulnerability was actively exploited, though the data has only now been released publicly. Researcher also verified that usernames and passwords in the leaked data matched the compromised devices.
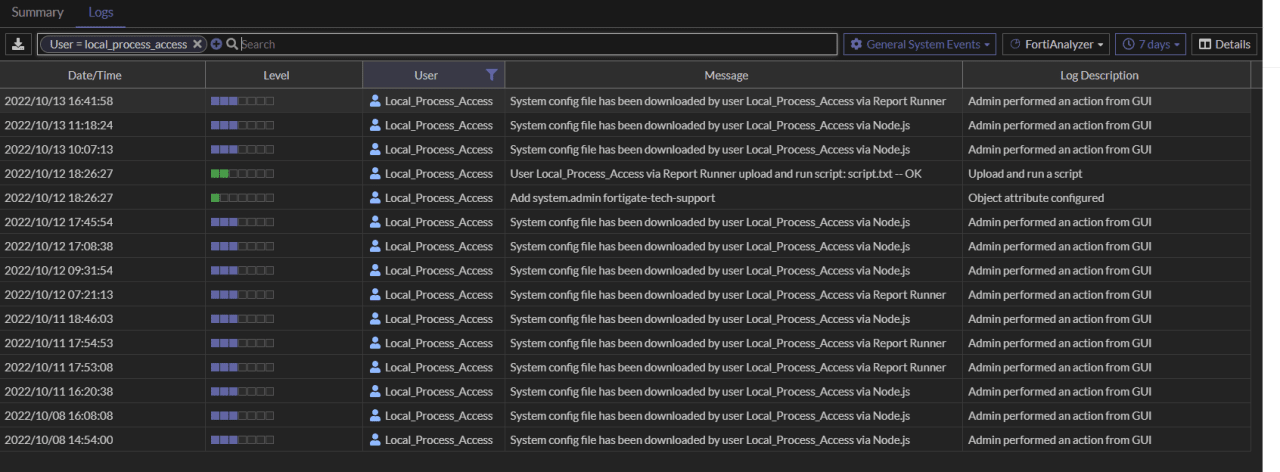
German news site corroborated that the devices involved were running FortiOS firmware versions 7.0.0 to 7.0.6 or 7.2.0 to 7.2.2. Notably, FortiOS 7.2.2 fixed CVE-2022–40684, raising questions about how some devices with this version were compromised. The data includes sensitive information, such as firewall rules and credentials, that could reveal insights into a network's defenses.
Researcher warns that organizations impacted by this leak should immediately change any credentials that remain unchanged since the breach and review their firewall rules to prevent further exploitation. He plans to release a list of the impacted IP addresses to help FortiGate administrators determine if their devices are included in the data dump.
This is not the first significant breach involving Fortinet devices. In 2021, nearly 500,000 Fortinet VPN credentials were leaked, tied to CVE-2018-13379. Fortinet has not yet commented on the Belsen Group's leak.
The incident underscores the critical need for timely patching and robust security practices. Organizations using FortiGate devices are urged to audit their systems, change credentials, and ensure they are running the latest, secure firmware versions.
Impact
- Exposure of Sensitive Data
- Unauthorized Gain Access
- Security Bypass
- Reputational Damage
Indicators of Compromise
- CVE-2022-40684
Affected Vendor
Fortinet
Affected Products
- Fortinet FortiOS 7.0.5
- Fortinet FortiOS 7.2.0
- Fortinet FortiOS 7.0.0
- Fortinet FortiOS 7.0.2
- Fortinet FortiOS 7.0.1
- Fortinet FortiProxy 7.0.0
- Fortinet FortiOS 7.0.3
- Fortinet FortiProxy 7.0.1
Remediation
- Refer to FortiGuard Advisory for patch, upgrade, or suggested workaround information.
- Organizations must test their assets for the vulnerabilities mentioned above and apply the available security patch or mitigation steps as soon as possible.
- Implement multi-factor authentication to add an extra layer of security to login processes.
- Regularly monitor network activity for any unusual behavior, as this may indicate that a cyberattack is underway.
- Organizations must stay vigilant and follow best practices for cybersecurity to protect their systems and data from potential threats. This includes regularly updating software and implementing strong access controls and monitoring tools.
- Develop a comprehensive incident response plan to respond effectively in case of a security breach or data leakage.
- Maintain regular backups of critical data and systems to ensure data recovery in case of a security incident.
- Adhere to security best practices, including the principle of least privilege, and ensure that users and applications have only the necessary permissions.
- Establish a robust patch management process to ensure that security patches are evaluated, tested, and applied promptly.
- Conduct security audits and assessments to evaluate the overall security posture of your systems and networks.
- Implement network segmentation to contain and isolate potential threats to limit their impact on critical systems.


