Severity
High
Analysis Summary
Bitter, a suspected South Asian cyber espionage threat group, sent two C++ malware families, WmRAT and MiyaRAT, to a Turkish defense sector business in November 2024. The attack chain delivered a shortcut (LNK) file that generated a scheduled task on the victim's computer to download more payloads using different data streams in a RAR package.
The researchers are tracking the threat actor as TA397. The adversary is also known as APT-C-08, APT-Q-37, Hazy Tiger, and Orange Yali and has been active since at least 2013. The APT group has a strong Asian focus, as seen by previous attacks that used malware, including BitterRAT, ArtraDownloader, and ZxxZ, to target organizations in China, Pakistan, India, Saudi Arabia, and Bangladesh.
According to previous reports, Bitter has also been connected to cyberattacks that have spread Android malware variants including PWNDROID2 and Dracarys. Researchers disclosed earlier this March that on February 1, 2024, Bitter launched a spear-phishing attempt against an unidentified Chinese government agency, delivering a trojan that could steal data and take over remotely. The threat actor used a lure concerning public infrastructure projects in Madagascar to trick potential victims into opening the booby-trapped RAR archive attachment in the most recent attack chain.
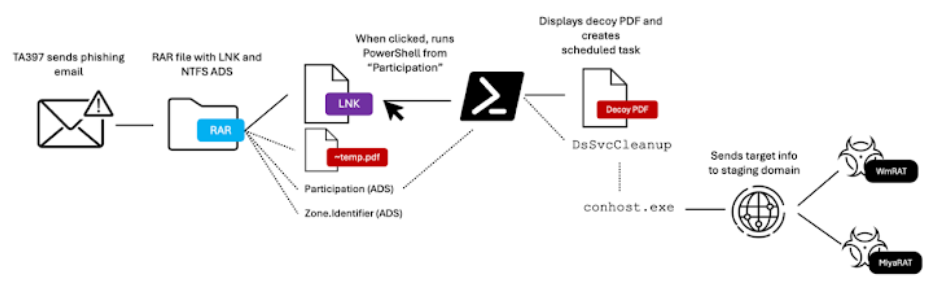
The RAR archive contained a covert alternate data stream (ADS) file with PowerShell code, a Windows shortcut file posing as a PDF, and a fake file regarding a World Bank public effort for infrastructure development in Madagascar. The New Technology File System (NTFS), which Windows uses to attach and read data streams to files, introduces a feature known as ADS. Threat actors can use it to covertly hide the existence of a dangerous payload inside the file record of a harmless file by smuggling extra data into it without changing its size or appearance.
While the second ADS contains a Base64-encoded PowerShell script to open the lure document and set up a scheduled task responsible for fetching the final-stage payloads from the domain jacknwoods[.]com, the first data stream contains code to retrieve a decoy file hosted on the World Bank site if the victim launches the LNK file. WmRAT and MiyaRAT both have standard remote access trojan (RAT) features that let the malware gather host information, upload or download files, take screenshots, obtain geolocation information, list files and directories, and execute arbitrary commands using PowerShell or cmd.exe.
Because MiyaRAT has been used selectively in a small number of campaigns, it is thought that its use is limited to high-value targets. These campaigns are most likely intelligence-gathering operations to further the objectives of a South Asian administration. To install harmful backdoors inside target businesses and obtain access to sensitive data and intellectual property, they consistently use scheduled activities to interact with their staging domains.
Impact
- Unauthorized Access
- Sensitive Data Theft
- Code Execution
- Data Exfiltration
- Cyber Espionage
Indicators of Compromise
Domain Name
- academymusica.com
IP
- 38.180.142.228
- 96.9.215.155
MD5
- 5b232b7417cb3965a942201de88f5055
- ecea1286158a462f7e3abfc13b6ed36e
- 7c96a61ae944b68d72a30f0483e25017
SHA-256
- f6c77098906f5634789d7fd7ff294bfd95325d69f1be96be1ee49ff161e07733
- 10cec5a84943f9b0c635640fad93fd2a2469cc46aae5e43a4604c903d139970f
- c7ab300df27ad41f8d9e52e2d732f95479f4212a3c3d62dbf0511b37b3e81317
SHA1
- f01472fd8ffbcd0c2b54075ee01bde6a2cc4f4e6
- 37c5abc5cc561431f1801f91460f0b496bb4e61f
- dd2f8bf8d9f0b787267eccaad64d30d101e6b838
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Along with network and system hardening, code hardening should be implemented within the organization to secure its websites and software. Use testing tools to detect any vulnerabilities in the deployed codes.
- Patch and upgrade any platforms and software on time and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions on time. Using a multi-layered protection is necessary to secure vulnerable assets.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Enable two-factor authentication.
- Do not download documents attached in emails from unknown sources and strictly refrain from enabling macros when the source isn’t reliable.

