Severity
High
Analysis Summary
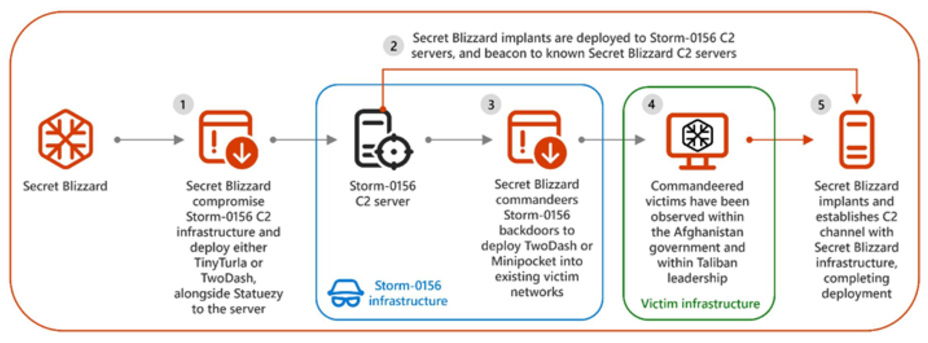
Since 2022, Turla, an advanced persistent threat (APT) group associated with Russia, has been connected to an as-of-yet-unreported campaign in which it gained access to the command-and-control (C2) servers of Storm-0156, a hacking gang based in Pakistan, in order to carry out its own activities.
According to the researchers, the activity, which was initially noticed in December 2022, is the most recent example of the nation-state adversary embedding themselves in the destructive activities of another group to achieve their own goals and cloud attribution initiatives. Turla first obtained control of a Storm-0156 C2 server in December 2022, and by the middle of 2023, they had extended their authority to other C2s connected to the Storm-0156 actor.
Through their access to these servers, Turla has been discovered to use the breaches previously planned by Storm-0156 to introduce unique malware families known as TwoDash and Statuezy into a limited number of networks associated with different Afghan government organizations. Statuezy is a trojan that tracks and logs data saved to the Windows clipboard, whereas TwoDash is a custom downloader. According to Microsoft, Storm-0156 infrastructure was the source of Turla’s command-and-control (C2) traffic, including infrastructure that Storm-0156 utilized to compile data that had been illicitly obtained from campaigns in Afghanistan and India.
Turla is believed to be connected to Russia's Federal Security Service (FSB). Other names for Turla include Blue Python, Iron Hunter, Pensive Ursa, Secret Blizzard (formerly Krypton), Snake, SUMMIT, Uroburos, Venomous Bear, and Waterbug. The threat actor has been active for almost 30 years and uses a wide range of advanced tools, such as Snake, ComRAT, Carbon, Crutch, Kazuar, HyperStack (also known as BigBoss), and TinyTurla. Its main objectives are military, diplomatic, and governmental institutions.
Additionally, the APT has a history of using the infrastructure of other threat actors for its own ends. The U.S. and U.K. governments disclosed in October 2019 that Turla had exploited the backdoors of an Iranian threat actor to further their own intelligence needs. Turla gained access to Iranian APTs' command-and-control (C2) infrastructure and utilized it to distribute their own tools to targeted victims.
Then, in January 2023, Mandiant, a company owned by Google, discovered that Turla had delivered its own spying and backdoor tools to targets in Ukraine by using attack infrastructure utilized by a commodity malware known as ANDROMEDA. When QUIETCANARY was deployed in September 2022 via the Tomiris backdoor, which was ascribed to a threat actor operating in Kazakhstan and tracked as Storm-0473, researchers noted the third case of Turla repurposing another attacker's weapon in April 2023.
The fact that Turla frequently uses other threat actors' tools or infrastructure to co-opt or take over them implies that this is a deliberate part of their strategies. According to the most recent attack campaign discovered by the researchers, the threat actor used Storm-0156 C2 servers to install backdoors on Afghan government devices and targeted C2 servers in India that housed data that had been exfiltrated from Indian military and defense-related organizations. Turla has also been able to take control of Storm-0156 C2 servers' backdoors, including Crimson RAT and a Golang implant known as Wainscot that was not previously known.
In particular, Turla downloaded and ran TwoDash in August 2024 via a Crimson RAT infection created by Storm-0156 in March 2024. Alongside TwoDash, another custom downloader called MiniPocket is also installed in victim networks. It uses TCP to connect to a hard-coded IP address or port to retrieve and execute a second-stage malware. The campaign reportedly escalated significantly when the Kremlin-backed attackers laterally moved to the Storm-0156 operator's workstation, most likely abusing a trust relationship to obtain valuable intelligence about their tooling, C2 credentials, and exfiltrated data gathered from previous operations.
This enables Turla to gather information about Storm-0156's South Asian targets of interest without going after those groups directly. Turla can gain traction on networks of interest with comparatively little labor by exploiting other people's campaigns. However, the information gathered using this method might not fully match Turla’s collection priorities because these early footholds are created on the targets of interest of another threat actor.
Impact
- Unauthorized Access
- Sensitive Data Theft
- Data Exfiltration
Indicators of Compromise
Domain Name
- connectotels.net
- hostelhotels.net
IP
- 154.53.42.194
- 173.212.252.2
- 185.213.27.94
- 167.86.113.241
- 109.123.244.46
- 146.70.158.90
- 161.35.192.207
- 91.234.33.48
MD5
- 837a823641bc5ba36bc3f49f4e9e8f2d
SHA-256
- aba8b59281faa8c1c43a4ca7af075edd3e3516d3cef058a1f43b093177b8f83c
SHA1
- 386b3cbf6be3512ee05638cf79225650dd9361a4
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Conduct regular security awareness training to educate employees about phishing threats and safe email practices.
- Enable multi-factor authentication (MFA) to strengthen account security and prevent unauthorized access.
- Implement robust email filtering mechanisms to identify and block phishing emails, reducing the risk of malware delivery.
- Ensure timely updates and patches for all software to address known vulnerabilities.
- Segregate critical systems and sensitive data from the rest of the network through network segmentation to limit lateral movement.
- Deploy comprehensive endpoint protection solutions to detect and block malware and ransomware, safeguarding devices from compromise.
- Collaborate with cybersecurity organizations and law enforcement agencies to share threat intelligence and stay informed about emerging threats.
- Develop and regularly update an incident response plan to efficiently handle cyber attacks, reducing downtime and minimizing the impact of a breach.

