Severity
High
Analysis Summary
Using a new Python-based malware named PXA Stealer, a threat actor who speaks Vietnamese has been connected to an information-stealing campaign that targets government and educational institutions in Europe and Asia.
According to the researchers, the malware targets users' personal data, such as login credentials for multiple online accounts, VPN and FTP clients, financial information, browser cookies, and data from gaming software. To steal the saved credentials of numerous online accounts, PXA Stealer can decode the victim's browser master password. Vietnamese remarks and a hard-coded Telegram account called "Lone None" in the stealer program—the latter of which features an icon of the Vietnamese national flag and a picture of the logo for the Ministry of Public Security—are the sources of the ties to Vietnam.
The attacker was selling SIM cards and Facebook and Zalo account credentials on the Telegram channel "Mua Bán Scan MINI," which has been connected to another threat actor known as CoralRaider. Additionally, Lone None has been discovered to be active on "Cú Black Ads - Dropship," another Vietnamese Telegram group run by CoralRaider. However, it is unclear at this time whether these two incursion sets are connected or if their campaigns are being run separately.
The automated tools that the attackers in the group shared are made to handle multiple user accounts. A Hotmail cookie batch modification tool, an email mining tool, and a Hotmail batch creation tool are among these tools. The threat actor's compressed packages frequently include both the executable files and the source code for these tools, enabling users to make changes as necessary.
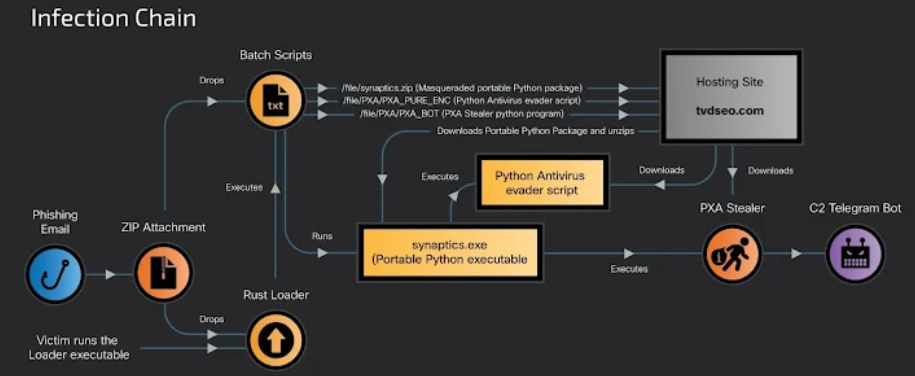
Evidence suggests that these applications are sold through other websites that advertise free hacking and cheating tools. There is a deliberate attempt to promote these products, as evidenced by the sharing of usage tutorials through YouTube channels. A phishing email with a ZIP file attachment that contains a Rust-based loader and a secret folder that packs in multiple Windows batch scripts and a fake PDF file is the first step in the attack chains that spread PXA Stealer.
The loader's execution starts the batch scripts that open the Glassdoor job application form, and the lure document, and uses PowerShell commands to download and run a payload that can disable the host's antivirus software before launching the stealer itself. PXA Stealer's focus on Facebook cookie theft, session authentication, and interaction with Facebook Ads Manager and Graph API to obtain further account information and related ad-related data is a notable feature. Vietnamese threat actors have a history of targeting Facebook business and advertising accounts, and PXA Stealer is just another example.
Impact
- Sensitive Information Theft
- Financial Loss
- Command Execution
- Security Bypass
Indicators of Compromise
Domain Name
- tvdseo.com
MD5
- 2d75aef413501fbb2905fe091e5f306f
- ccd71f7ad7eb8dbb03fef4ce87cf4234
- a8e76dc110985f1eff6b15505160acf1
- 722028ebcfee5bb1cf83f687d73232a4
- 7c46c934839cbbe8cc99cf2c1324c797
- f68d003cf3dd7461dfb67584c9b4608a
- adabb1b5ab34eceebe677ec0c83131cd
SHA-256
- fdad95329954e0085d992cba78188a26abd718797f4a83347ec402f70fe65269
- 7db49da15fd159146fe869d049e030a4ecd0d605a762bea4cc4eb702a6ce9ee6
- 707004559c8d625f2d4b296ede702def1f9f52cadf4c52dadc41f3077531d04f
- bc15114841e39203b4e0f5d2cdeef11cc4eceba99eb0c3074a1c6d7b3968404a
- a9e3f6b9047b5320434bc7b64f4ba6c799d2b6919d41ed32e9815742f3c10194
- 782da8904a729971fab86286dd1f44e8de686b7bc66b855079381e1c9e97f6da
- e689601d502cc0cd8017f9d6953ce7e201b2dad42f679dc33afa673249ea1aa4
SHA1
- ca2266ae6a876ab0ff981a278591409c744781b3
- e43a4d5f98e74bedd59770bf9406fd3c848f6128
- b5948e51494faf2b5e75fe87d23922d080c64efd
- 23db1e7bc517b77310149c27be6838a23149de59
- 4ee651adf3738eac5a897c15acaa199b042c6992
- e20ed07a312efb5597f3cab4e61e1cf2abc6068f
- 327775de37951a78263245e4b1c648f134e74775
URL
- https://tvdseo.com/file/synaptics.zip
- https://tvdseo.com/file/PXA/PXA_PURE_ENC
- https://tvdseo.com/file/PXA/PXA_BOT
- https://tvdseo.com/file/Adonis/AdFnis_Bot
- https://tvdseo.com/file/Adonis/Adonis_Bot
- https://tvdseo.com/file/Adonis/Adonis_XW_ENC
- https://tvdseo.com/file/Adonis/Adonis_Bot0
- https://tvdseo.com/file/STC/Cookie_Ext.zip
- https://tvdseo.com/file/STC/STC_XW_ENC
- https://tvdseo.com/file/STC/STC_PURE.b64
- https://tvdseo.com/file/STC/STC_PUP
- https://tvdseo.com/file/STC/STC_OTO
- https://tvdseo.com/file/PXA/Cookie_Ext.zip
- https://tvdseo.com/file/STC/STC_PURE_ENC
- https://tvdseo.com/file/STC/STC_BOT
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

