Severity
High
Analysis Summary
Systems that were previously attacked by the RustyStealer infostealer malware are now encrypted by a new ransomware family known as "Ymir" which has been discovered in the wild. Although the RustyStealer malware family was first identified in 2021, its co-occurrence with ransomware serves as another illustration of the current pattern of cybercrime groups collaborating.
The new ransomware strain, Ymir, is noteworthy for its in-memory execution, usage of the African Lingala language in a code comment, use of PDF files as ransom notes, and extension setting options, according to the researchers who found it during an incident response. Ymir cannot exfiltrate data, although researchers have discovered evidence that it connects to external servers that could do so. The ransomware campaign began targeting businesses all around the world in July 2024.
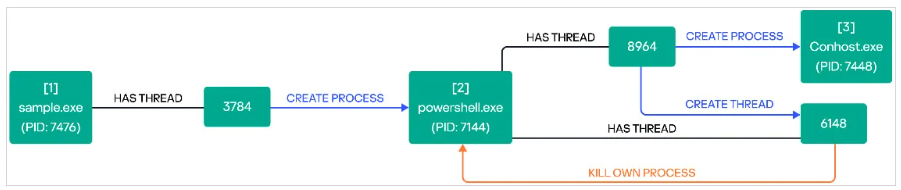
Two days before Ymir's deployment, Rusty Stealer had compromised several systems within the targeted infrastructure. Essentially a credential-harvesting tool, RustyStealer allowed attackers to enter systems without authorization by breaching authentic high-privilege accounts that were helpful for lateral movement. Tools such as Windows Remote Management (WinRM) and PowerShell for remote control made it easier to move laterally across the network. The attackers also installed programs like Advanced IP Scanner and Process Hacker at the same time.
They then ran scripts linked to the SystemBC malware and created secret channels with the attackers' infrastructure, potentially for data exfiltration or command execution. Ymir ransomware was distributed as the last payload after establishing a foothold and potentially stealing data using RustyStealer. Ymir is a new strain of Windows ransomware that runs solely in memory and uses tools like "malloc," "memove," and "memcmp" to avoid detection.
In order to ascertain whether it operates on a sandbox, it does system reconnaissance upon launch by obtaining the system's date and time, identifying any processes that are active, and monitoring the system's uptime. To prevent the system from becoming unbootable, it then ignores file extensions according to a hardcoded list.
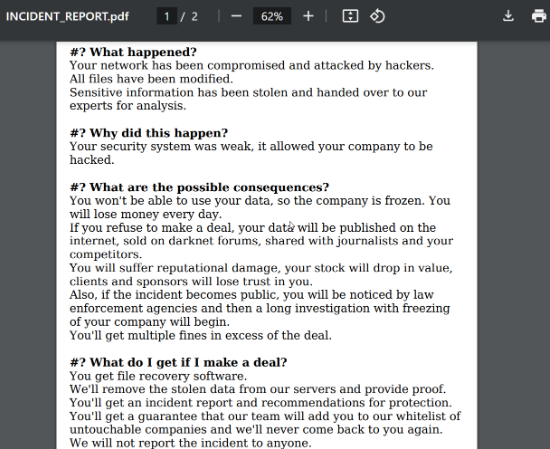
Ymir encrypts files on the victim's computer using the ChaCha20 stream cipher, a sophisticated and quick encryption method. Random extensions, such as ".6C5oy2dVr6," are appended to encrypted files, and the ".data" part of the Ymir binary is used to create a ransom letter called "INCIDENT_REPORT.pdf" in every directory that contains encrypted files.
Additionally, before a user signs in to an encrypted computer, the ransomware will alter the Windows Registry's "legalnoticecaption" value to display an extortion demand. According to the ransom note, the victim's machine had data stolen, and researchers speculate that this might have happened with tools that were in place before Ymir. To avoid detection and analysis, Ymir lastly checks the system for PowerShell and uses it to remove its executable.
Although Ymir hasn't set up a site for data leaks yet, threat actors may have only recently begun to gather victim information. Researchers caution that this new ransomware family may become a major danger very soon due to Ymir's exploitation of infostealers as access brokers.
Impact
- File Encryption
- Sensitive Data Theft
- Financial Loss
- Unauthorized Access
- Command Execution
Indicators of Compromise
IP
- 74.50.84.181
- 94.158.244.69
- 5.255.117.134
- 85.239.61.60
MD5
- dd7799d822f052cfa8ad1e16b33bb2cb
- 4efafe2dd9abb5b22b4f15a861b7c804
- 5ee1befc69d120976a60a97d3254e9eb
- 0fd79133bd46b420056204b475719cd5
- f4e832261cc90a83ae7a65ec2a0fb987
- 4176233617a9d682e17e8cf97d8925b1
SHA-256
- 04dce8eb632250f64f1741f47707e6cb991926d35f4157d540c2fc3230b6a92f
- 659e9566120d02301b34aad279ca1bcb20855cf52b0bd1b67cf5f6f5b3c83f9e
- 7c00152cc68f0104e7436f9ce8b4c99e685d05f4361f50af307d4bfdbc90bca0
- 8287d54c83db03b8adcdf1409f5d1c9abb1693ac8d000b5ae75b3a296cb3061c
- 51ffc0b7358b7611492ef458fdf9b97f121e49e70f86a6b53b93ed923b707a03
- b087e1309f3eab6302d7503079af1ad6af06d70a932f7a6ae1421b942048e28a
SHA-1
- fe6de75d6042de714c28c0a3c0816b37e0fa4bb3
- f954d1b1d13a5e4f62f108c9965707a2aa2a3c89
- e6c4d3e360a705e272ae0b505e58e3d928fb1387
- 79e581dee9b2a19943fe79136d58859e4ac5dffa
- 8d2e9dc4c786d6ba2bee397cdc470fb90644e2a5
- 7249fb9226c81142bd0266f0268579a1b4d370b1
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

