Severity
High
Analysis Summary
GoldenJackal, a lesser-known threat actor, has been connected to several cyberattacks against embassies and government agencies that attempt to breach air-gapped systems by utilizing two different custom toolkits.
According to the researchers, victims included an institution affiliated with the European Union (EU) and an embassy from South Asia located in Belarus. GoldenJackal appears to have as its ultimate purpose stealing sensitive data, particularly from well-known computers that may not be online.
When a Russian security company disclosed the threat cluster's attacks on diplomatic and governmental targets in the Middle East and South Asia, the world learned about GoldenJackal for the first time in May 2023. The threat group has roots dating back to at least 2019. The usage of a worm called JackalWorm, which may infect connected USB sticks and distribute a trojan called JackalControl, is a crucial aspect of the invasions.
There is tactical overlap with malicious tools used in campaigns associated with Turla and MoustachedBouncer, the latter of which has also targeted foreign embassies in Belarus, even if there is not enough information to definitively link the activities to a particular nation-state threat. GoldenJackal artifacts were reportedly found by cybersecurity researchers in August and September of 2019 and again in July 2021 in a South Asian embassy in Belarus. The threat actor's ability to use an entirely redesigned toolkit against an EU government agency between May 2022 and March 2024 is very noteworthy.
Given the level of complexity involved, it is remarkable that GoldenJackal was able to create and implement not one, but two distinct toolkits intended to breach air-gapped systems in just five years. This illustrates the group's inventiveness. Apart from JackalControl, JackalSteal, and JackalWorm, it is said that three separate malware families were used in the attack against the South Asian embassy in Belarus:
- GoldenDealer, which is used to distribute executables to the air-gapped system using compromised USB drives.
- GoldenRobo is a file collector and data exfiltration tool.
- GoldenHowl is a modular backdoor with the ability to establish scheduled tasks, upload and receive files to and from a remote server, and create an SSH tunnel.
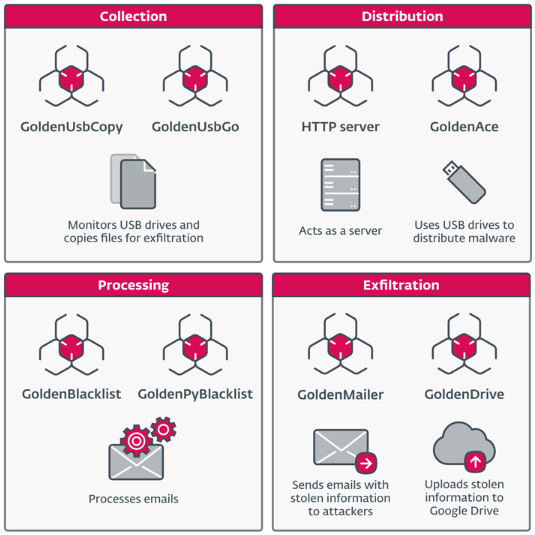
On the other hand, it has been discovered that the attacks directed toward the unidentified European government institution use a whole new collection of malware tools, the majority of which are written in Go. They are designed to exfiltrate data, gather files from USB devices, disseminate malware via USB drives, and utilize some machine servers as staging servers for payload distribution to other hosts:
- The USB drive monitoring and file copying tools GoldenUsbCopy and its enhanced replacement GoldenUsbGo are used for exfiltration.
- GoldenBlacklist and its Python implementation GoldenPyBlacklist are designed to process email messages of interest for subsequent exfiltration.
- GoldenAce is used to spread the malware, including a lightweight version of JackalWorm, to other systems (not necessarily those that are air-gapped).
- GoldenDrive is a tool that uploads stolen data to Google Drive.
- GoldenMailer is a tool that emails attackers with stolen data.
How GoldenJackal obtains the initial compromise to infiltrate target environments is currently unknown. Still, researchers had previously hinted at the prospect of malicious Microsoft Word documents and trojanized Skype installers serving as entry points. When a USB drive is plugged, GoldenDealer, which is already installed on a machine that is linked to the internet and is distributed through an as-yet-unknown method, activates and copies itself together with an unidentified worm component into the detachable device.
It is believed that the unknown component is run when the compromised USB drive is attached to the air-gapped system, after which GoldenDealer records the machine's data on the USB drive. The second time the USB device is placed into the previously described internet-connected computer, GoldenDealer transmits the data from the drive to an external server, which reacts by sending the necessary payloads for the air-gapped system to execute.
The executables that were downloaded are also copied to the USB drive by the malware. In the last stage, when the device is connected to the air-gapped machine again, GoldenDealer grabs the transferred executables and runs them. GoldenRobo, for its part, is also running on the internet-connected PC and is ready to transfer the files from the USB drive to the server under the attacker's control. The Go-written malware derives its name from the fact that it copies the files using robocopy, a Windows program.
According to the experts, the process of moving the files from the air-gapped PC to the USB drive itself is handled by a different module that has not yet been found. GoldenJackal is a skilled threat actor who is aware of the network segmentation utilized by its targets because it was able to create two distinct toolsets for breaching air-gapped networks in just five years.
Impact
- Sensitive Data Theft
- Data Exfiltration
Indicators of Compromise
Domain Name
- assistance.uz
- xgraphic.ro
IP
- 83.24.9.124
- 196.29.32.210
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enabling two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

