Severity
High
Analysis Summary
Over the last year, more than 140,000 phishing websites have been discovered to be connected to the PhaaS platform Sniper Dz, suggesting that many cybercriminals are using it to steal credentials.
Sniper Dz provides an online admin panel with a catalog of phishing pages for would-be phishers. Phishers have two options: they can download Sniper Dz phishing templates to host on their own servers, or they can host these phishing pages on Sniper Dz's infrastructure. The fact that these services are given away for free may be what makes it even more profitable. That said, the credentials harvested using the phishing sites are also exfiltrated to the operators of the PhaaS platform, a technique that Microsoft calls double theft.
PhaaS platforms, which enable even those with little technical expertise to mount phishing attacks at scale, have become an increasingly common way for aspiring threat actors to get into the world of cybercrime. These phishing kits are available for purchase on Telegram, where there are groups and channels devoted to every step of the attack chain, including hosting and phishing message distribution.
The threat actors behind Sniper Dz have over 7,170 subscribers on their Telegram channel as of October 1, 2024, so they are not an exception. May 25, 2020, saw the creation of the channel. It's interesting to note that the channel owners activated the auto-delete feature, which will automatically remove all posts after a month, the day after the report went live. Even though previous messages are still visible in the chat history, this probably indicates an attempt to hide evidence of their activity.
The website's home page states that to "get your scams and hack tools," users must first create an account on the clearnet's PhaaS platform. The service provides ready-to-use scam templates in English, Arabic, and French for several online sites, including X, Facebook, Instagram, Skype, Yahoo, Netflix, Snapchat, and PayPal, according to a January 2021 Vimeo video. To date, the video has received over 67,000 views.
Researchers have also discovered instructional videos on YouTube that walk users through the various steps needed to download templates from Sniper Dz and create phony landing pages for Free Fire and PUBG on trustworthy websites like Google Blogger. It's unclear, though, whether they are merely users of the service or if they are connected in any way to the people who created Sniper Dz.
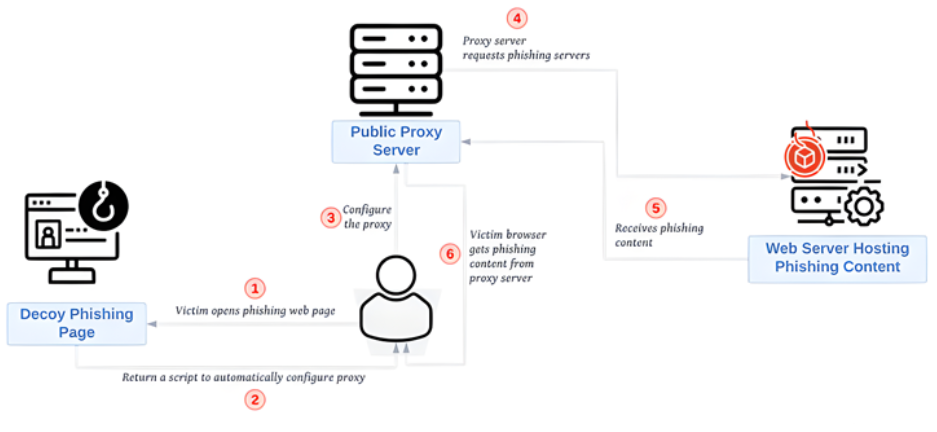
Phishing pages can be hosted on Sniper Dz's own infrastructure, and custom links can be created to direct users to those pages. To avoid being discovered, these websites are then concealed behind a reputable proxy server. Without establishing direct contact, the group behind Sniper Dz sets up this proxy server to automatically load phishing content from its own server. Since the proxy server will be perceived by the victim's browser or a security crawler as having loaded the phishing payload, this technique can aid Sniper Dz in protecting its backend servers.
Cybercriminals also have the option of downloading phishing page templates as HTML files offline and hosting them on their own servers. Sniper Dz also provides extra tools for converting phishing templates to blogger format, which can be hosted on Blogspot domains. Upon logging into the clearnet site, one can ultimately view the compromised credentials on an admin panel.
Researchers reported that beginning in July 2024, they noticed an increase in phishing activity using Sniper Dz, mainly aimed at American internet users. Via a centralized infrastructure, Sniper Dz phishing pages track down victims by exfiltrating their credentials. This might facilitate the acquisition of victim credentials by Sniper Dz from phishers using their PhaaS platform.
Impact
- Credential Theft
- Data Exfiltration
Indicators of Compromise
Domain Name
- sniperdz.com
- dev-cdn370.pantheonsite.io
- automaticgiveaway.000webhostapp.com
- facebookbusiness0078.blogspot.be
URL
- http://raviral.com/k_fac.php
- http://raviral.com/host_style/style/js-track/track.js
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enable two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting only to allow approved software to run on systems, reducing the risk of executing unauthorized applications.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

