Severity
High
Analysis Summary
Researchers have discovered an unprecedented botnet made up of a horde of Internet of Things (IoT) and small office/home office (SOHO) devices. This botnet is most likely run by a Chinese nation-state threat actor known as Flax Typhoon (also known as Ethereal Panda or RedJuliett).
It is estimated that the advanced botnet, tracked by the researchers as Raptor Train, has been in operation since at least May 2020 and peaked in June 2023 with 60,000 actively compromised devices. Since then, the Raptor Train botnet has been recruited by more than 200,000 SOHO routers, NVR/DVR devices, network-attached storage (NAS) servers, and IP cameras, making it one of the biggest Chinese state-sponsored IoT botnets found to date.
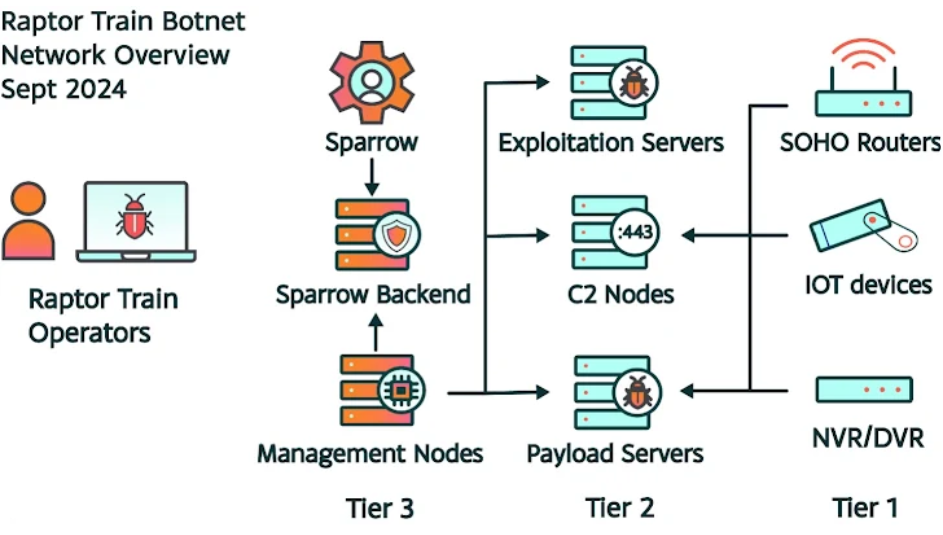
Since its creation, the botnet's infrastructure is thought to have entangled hundreds of thousands of devices. Its three-tiered design is made up of the following components:
- Tier 1: IoT/SOHO devices that are compromised
- Tier 2: Command-and-control (C2) servers, payload servers, and exploitation servers
- Tier 3: Sparrow (formerly known as Node Comprehensive Control Tool, or NCCT), a cross-platform Electron application front-end, with centralized administration nodes
The way it operates is that tasks for the bots are started from Tier 3 "Sparrow" management nodes, which then route them through the relevant Tier 2 C2 servers before sending them to the Tier 1 bots, which comprise a significant portion of the botnet. Devices from several manufacturers, including ActionTec, ASUS, DrayTek, Fujitsu, Hikvision, Mikrotik, Mobotix, Panasonic, QNAP, Ruckus Wireless, Shenzhen TVT, Synology, Tenda, TOTOLINK, TP-LINK, and Zyxel, are among those targeted.
Most of the Tier 1 nodes are geolocated in the United States, Brazil, Hong Kong, Taiwan, Vietnam, and Turkey. The average lifespan of these nodes is 17.44 days, which suggests that the threat actor can easily re-infect the devices. Most of the time, the operators neglected to provide a persistence mechanism that endures a reboot.

Raptor Train has an intrinsic persistence due to the large number of susceptible devices on the Internet and the wide variety of exploits accessible for a variety of SOHO and IoT devices. This combination contributes to the confidence in re-exploitability. An in-memory implant known as Nosedive, a customized version of the Mirai botnet, infects the nodes through Tier 2 payload servers specifically designed for this purpose. The ELF binary can perform DDoS attacks, upload and download files, and execute commands.
In contrast, Tier 2 nodes are mainly located in the United States, Singapore, the United Kingdom, Japan, and South Korea and are rotated every 75 days. Between June 2024 and August 2024, there will be at least 60 C2 nodes, up from roughly 1–5 between 2020 and 2022. These nodes are adaptable because they can function as payload servers, exploitation servers for enlisting new devices into the botnet, and even help with entity reconnaissance.
Since the middle of 2020, at least four distinct campaigns have been connected to the constantly changing Raptor Train botnet; these campaigns may be identified by the root domains they utilize and the devices they target.
- Crossbill (May 2020 – April 2022): Utilizing k3121[.]com as the C2 root domain and its related subdomains
- Finch (July 2022 – June 2023): Utilizing b2047[.]com as the C2 root domain and its related C2 subdomains
- Canary (May 2023 – August 2023): Utilizing multi-stage droppers, the C2 root domain b2047[.]com and related C2 subdomains are used
- Oriole (June 2023 – September 2024): Utilizing the w8510[.]com C2 root domain and its related C2 subdomains
The Canary campaign is noteworthy for using a multi-layered infection chain of its own to download a first-stage bash script that connects to a Tier 2 payload server to retrieve Nosedive and a second-stage bash script. The campaign primarily targeted ActionTec PK5000 modems, Hikvision IP cameras, Shenzhen TVT NVRs, and ASUS routers. Every sixty minutes, the new bash script tries to download and run a third-stage bash script from the payload server.
Although evidence suggests that the botnet has been weaponized to target American and Taiwanese organizations in the military, government, higher education, telecommunications, defense industrial base (DIB), and information technology (IT) sectors, no DDoS attacks have been recorded from it as of yet. The connections to Flax Typhoon, a threat group that has a history of attacking targets in Taiwan, Southeast Asia, North America, and Africa, are based on tactical resemblances, overlaps in the victimology footprint, and the use of Arabic.
Following a court-authorized law enforcement operation, the Raptor Train botnet was taken down, the U.S. Department of Justice (DoJ) stated on Wednesday. Additionally, it linked the Flax Typhoon threat actor to Integrity Technology Group, a publicly traded business with headquarters in Beijing. Despite the threat actors' vain attempts to obstruct the remediation action by launching a DDoS attack against the servers the FBI was using to carry out the court order, the operation saw the attackers' infrastructure seized to issue disabling commands to the malware on infected devices.
Impact
- Denial of Service
- Data Theft
- Command Execution
- Operational Disruption
Indicators of Compromise
Domain Name
- zdacasdc.w8510.com
- zdacxzd.w8510.com
- bzbatflwb.w8510.com
- qacassdfawemp.w8510.com
- apdfhhjcxcb.w8510.com
- amushuvfikjas.b2047.com
- acgtjkiufde.b2047.com
- xaqw.k3121.com
- oklm.k3121.com
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Never trust or open links and attachments received from unknown sources/senders.
- Upgrade your operating system.
- Enable antivirus and anti-malware software and update signature definitions on time. Using multi-layered protection is necessary to secure vulnerable assets.
- Immediately change default passwords on IoT devices to unique ones.
- Keep devices' firmware and software up to date to ensure that known vulnerabilities are patched.
- Implement firewalls and intrusion detection systems to monitor and control traffic to and from IoT devices.
- Employ tools that can identify unusual behavior or traffic patterns that might indicate a DDoS attack or a compromised device.
- Disable any unnecessary services or features on IoT devices to reduce their attack surface.
- Follow security best practices, such as disabling remote management if not needed and enabling security features provided by the device manufacturer.
- Deploy intrusion detection and prevention systems (IDS/IPS) to monitor for anomalous or malicious network activity.
- Set up alerts for unusual traffic patterns that might indicate a DDoS attack or a compromised device.

