Severity
High
Analysis Summary
A cyber-espionage group associated with North Korea has been seen using job-themed phishing lures to target potential victims in the energy and aerospace verticals and infect them with MISTPEN, an as-yet-undocumented backdoor.
Under the codename UNC2970, the activity cluster is being monitored by Google-owned Mandiant, which says that it coincides with the threat group TEMP.Hermit, also known as Diamond Sleet (previously Zinc) or Lazarus Group in general. Since at least 2013, the threat actor has a history of targeting international financial, defense, telecommunication, and government organizations to gather strategic intelligence that advances North Korean interests. It is associated with the General Bureau of Reconnaissance (RGB).
The threat intelligence company reported that it has seen multiple entities in the United States, the United Kingdom, the Netherlands, Cyprus, Sweden, Germany, Singapore, Hong Kong, and Australia being targeted by UNC2970. UNC2970 poses as a recruiter for well-known companies and targets victims under the pretense of employment openings. Additionally, the selected job descriptions are aimed at managers and senior personnel. This implies that the threat actor wants to obtain private and sensitive data that is normally only accessible by higher-ranking staff members.
The attack chains, also referred to as Operation Dream Job, involve interacting with victims via email and WhatsApp using spear-phishing lures to gain their trust before forwarding a malicious ZIP archive file that appears to be a job description. A curious quirk is that the description's PDF file can only be viewed with a malicious copy of Sumatra PDF, a genuine PDF reader program that is included in the download and is used to distribute MISTPEN through BURNBOOK, a launcher.
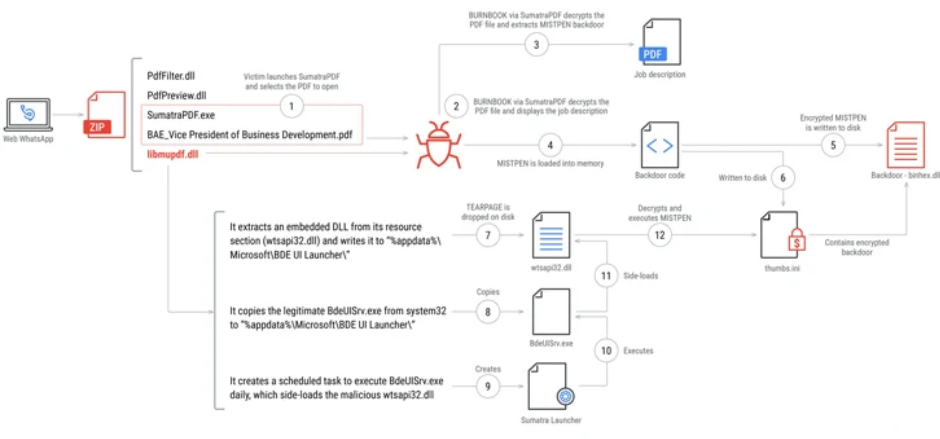
It is important to clarify that neither a supply chain attack nor a software vulnerability is implied by this. Instead, it has been discovered that the attack uses an outdated version of Sumatra PDF that has been modified to start the infection chain. Mandiant and Microsoft both emphasize the use of a variety of open-source software, including PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software installer for these attacks. This is a tried-and-true technique that the threat actor group has been using since 2022.
It is thought that the threat actors most likely give the victims instructions on how to open the PDF file with the accompanying weaponized PDF reader tool to cause the malicious DLL file, BURNBOOK, a C/C++ launcher, to execute. This file is a dropper for an embedded DLL called "wtsapi32.dll," which is used to launch the MISTPEN backdoor following a system reboot and is tracked as TEARPAGE. A backdoor is present in MISTPEN, a trojanized version of the genuine Notepad++ plugin binhex.dll. The loader embedded in BURNBOOK, TEARPAGE, is in charge of decrypting and starting MISTPEN. MISTPEN is a C-based lightweight implant that can download and run Portable Executable (PE) files from a command-and-control (C2) server. The following Microsoft Graph URLs are compatible with it through HTTP.
Additionally, Mandiant said it has found earlier BURNBOOK and MISTPEN evidence, indicating that these systems are being continuously enhanced to include new features and enable covert operations. Compromised WordPress websites were also used as C2 domains in the initial MISTPEN samples. To impede the study of the samples, the threat actor has enhanced their malware over time by adding new capabilities and a network connectivity check.
Impact
- Cyber Espionage
- Sensitive Data Theft
- Identity Theft
- Code Execution
Indicators of Compromise
URL
- https://dstvdtt.co.za/wp-content/plugins/social-pug/assets/lib.php
- https://cmasedu.com/wp-content/plugins/kirki/inc/script.php
- https://bmtpakistan.com/solution/wp-content/plugins/one-click-demo-import/assets/asset.php
- https://verisoftsystems.com/wp-content/plugins/optinmonster/views/upgrade-link-style.php
- https://www.clinicabaru.co/wp-content/plugins/caldera-forms/ui/viewer-two/viewer-2.php
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enable two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

