Severity
High
Analysis Summary
Cicada3301 is a new ransomware-as-a-service (RaaS) operation that has rapidly emerged on the cybercrime scene already listing 19 victims on its extortion portal. The group uses double-extortion tactics which involve breaching corporate networks, stealing data, and encrypting devices. Victims are then threatened with data leaks unless they pay a ransom. The ransomware operation is named after the mysterious online game Cicada 3301 but has no connection to the original project which has condemned the group’s actions. Cicada3301 was first observed recruiting affiliates on the RAMP cybercrime forum on June 29, 2024, but earlier attacks suggest it may have operated independently before that.
An analysis by researchers indicates that Cicada3301 shares many similarities with the ALPHV/BlackCat ransomware suggesting it could be a rebrand or a fork from ALPHV’s core team members. These similarities include both ransomware strains being written in Rust using the ChaCha20 encryption algorithm, and employing identical commands for VM shutdown and snapshot wiping. Both also use the same command parameters, file naming conventions, ransom note decryption methods, and intermittent encryption techniques. These overlaps point to a strong connection between the two operations, possibly even involving some of the same individuals.
Cicada3301 also appears to have potential partnerships or collaborations with the Brutus botnet for initial access to networks particularly targeting VPN appliances from vendors like Cisco, Fortinet, Palo Alto, and SonicWall. The botnet is known for its VPN brute-forcing activities, and its emergence aligns with the shutdown of ALPHV, further suggesting a possible link. The ransomware is equipped with both Windows and Linux/VMware ESXi encryptors with a special focus on targeting VMware environments. This indicates a strategic design to maximize damage in enterprise environments as many organizations rely on virtualized infrastructure.
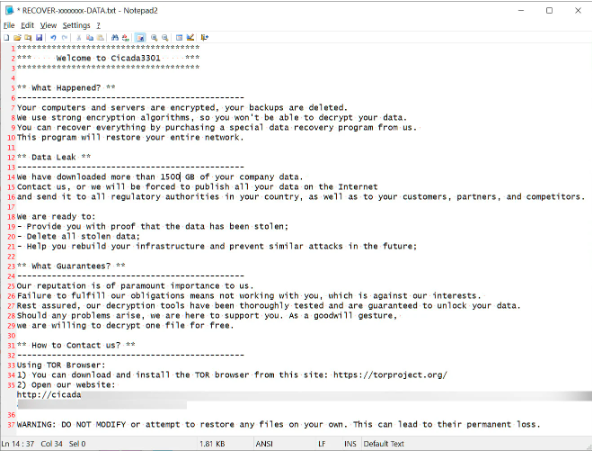
The ransomware’s encryptor uses a combination of ChaCha20 for file encryption and RSA for key protection, employing a command-line argument to initiate encryption and a "no_vm_ss" parameter to encrypt VMware ESXi virtual machines without prior shutdowns. By default, it utilizes commands like 'esxcli' and 'vim-cmd' to shut down VMs and delete snapshots aiming to disrupt operations and remove recovery options. This approach ensures a high-impact attack, affecting entire networks and infrastructures, thereby increasing pressure on victims to pay the ransom. The ransomware's aggressive tactics and technical capabilities highlight its potential to cause significant disruption and financial damage to targeted organizations.
Impact
- Data Breach
- File Encryption
- Double Extortion
- Financial Loss
Remediation
- Ensure all operating systems, software, and firmware, including VMware ESXi, are up-to-date with the latest patches to protect against known vulnerabilities that Cicada3301 and similar ransomware might exploit.
- Given that the Brutus botnet is associated with VPN brute-forcing, ensure VPN appliances (such as those from Cisco, Fortinet, Palo Alto, and SonicWall) are secured with strong, complex passwords and, where possible, multi-factor authentication (MFA). Regularly update VPN firmware and monitor for any unauthorized access attempts.
- Segment your network to limit the spread of ransomware. Ensure critical systems are isolated and employ strict access controls to minimize lateral movement if an attacker breaches the network.
- Regularly back up critical data and ensure that backups are stored securely and are not accessible from the primary network to prevent them from being encrypted or deleted by ransomware. Test backup restoration procedures periodically to ensure data integrity and availability.
- Ransomware often uses built-in tools like PowerShell, esxcli, and vim-cmd for malicious activities. Restrict and monitor the use of these tools to legitimate administrative purposes only, and use logging to detect unusual activity.
- Utilize EDR solutions to detect and respond to malicious activities quickly. Focus on identifying behaviors associated with ransomware attacks, such as the unusual creation of files, modifications to system processes, and encryption-related commands.
- Since Cicada3301 targets VMware ESXi environments, configure these environments with security best practices, such as disabling unnecessary services, limiting access to management interfaces, and employing strong authentication methods.
- Conduct regular training sessions to educate employees on identifying phishing emails and other social engineering tactics that could be used to deliver ransomware. Encourage reporting of suspicious emails and activities.
- Develop and routinely test an incident response plan specifically tailored for ransomware incidents. This plan should include procedures for isolating affected systems, communicating with stakeholders, and safely restoring operations.
- Regularly perform security audits and penetration testing to identify and remediate vulnerabilities in your network that could be exploited by ransomware attackers.

