Severity
High
Analysis Summary
ViperSoftX, a sophisticated malware first detected in 2020, has evolved to distribute itself as eBooks via torrents. This latest variant of ViperSoftX uses the Common Language Runtime (CLR) to load and execute PowerShell commands, dynamically creating a PowerShell environment within AutoIt.
This approach allows the malware to integrate PowerShell functionality seamlessly executing malicious activities while evading detection mechanisms that might flag standalone PowerShell activity. The malware exemplifies the continuous innovation of threat actors to remain stealthy and circumvent defenses adopting advanced anti-analysis techniques such as byte remapping and web browser communication blocking.
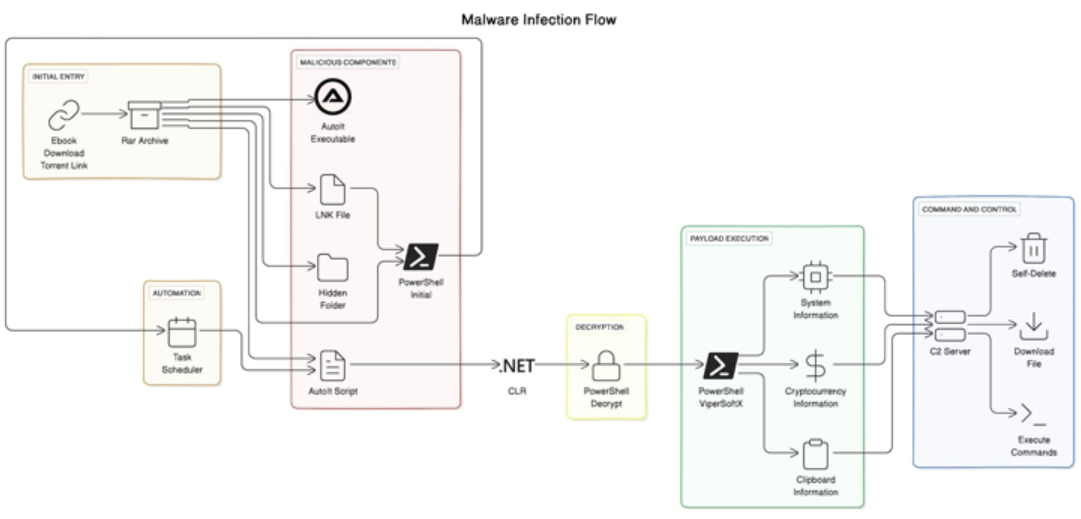
Security researchers' report highlights that ViperSoftX’s new distribution method involves eBook lures containing hidden folders and deceptive Windows shortcut files within supposed eBook RAR archives. Executing the shortcut initiates a multi-stage infection process starting with PowerShell code that reveals the concealed folder and sets up system persistence. This then launches an AutoIt script interacting with the .NET CLR framework to decrypt and run a secondary PowerShell script, ultimately executing ViperSoftX. The AutoIt language’s user-defined functions (UDF) provide a gateway to the CLR library, granting access to PowerShell’s capabilities.
The malware is adept at exfiltrating sensitive information from compromised Windows hosts, scanning for cryptocurrency wallets via browser extensions capturing clipboard contents, and dynamically downloading and executing additional payloads and commands from a remote server. It also features self-deletion mechanisms to avoid detection. One of its hallmark features is the integration of the CLR to orchestrate PowerShell operations within AutoIt, which allows the seamless execution of malicious functions while evading traditional detection mechanisms.
Additionally, ViperSoftX's capability to patch the Antimalware Scan Interface (AMSI) before executing PowerShell scripts demonstrates its sophisticated approach to bypassing security measures. Recent campaigns as of May 2024 have leveraged ViperSoftX to distribute other malware such as Quasar RAT and TesseractStealer utilizing cracked software and torrent sites, with the eBook lure method being a newly observed tactic. This evolution highlights the ongoing challenge for cybersecurity defenses in keeping up with the innovative tactics employed by threat actors.
Impact
- Sensitive Data Theft
- Data Exfiltration
- Cryptocurrency Theft
Indicators of Compromise
URL
- https://security-microsoft.com/connect
- https://borcano.org/connect
MD5
- c9bd4557a1e96b0cfac3714f10b78456
- 0286c174a5bacddc05ef222ff7c5efdb
- 92fa3936ce03cd99262a5782d05d9925
- ae3e95988588a6e4c7f5cc32a26d7553
- ea8f4d39f68ca2723b2aacf0f3b0f830
- e50a3183667b67f233ac133aeb275378
- 49a76efb0b1567f7ad3e12754b70bd5e
- e7c0577a9dd6921d6b0c3fdb4c73c786
- e6891a114faa4555acd0c94a57175aea
- b7aa1ce0f53521cd196849f1bdad284d
- 674c4877653a8672cc9b1d935b0a2d55
- e06311b5ab62f5e7832e1e124edcc1be
- 69c76e596f20df20c54db82bd02f6a1e
SHA-256
- 1177fb1b6b4a6ac1cd75c0f0784bb87a3202c70fe748bf5bc7fd0dd0fd41169b
- 07ee16f72b1dd81e7cf79aa1396f44f3ed29d343dd8fa0c6aecf1bb3d36d4e34
- f2503068aa274eb6c73dfd1a31c7e878f84f3fb60f3ae23f001bb143eb6f196f
- 96a1666152dfe5cc4113b855a059195227f55773d8ad46cc92fe5090010035f1
- de05f6f97b475ed6464541665e59252869b5d531c63698a9ad70c3875954c92c
- acf98f0c2b3823f9213b220fcd79237037d0d3f087a3faa4f10ea6d147a9f059
- 7701e4bf5074f0527c0126fff1dbd0e6368ddb7d0131bac1fba72b19511af127
- 4d365958397af1b7c2c62f62d21b35b948c03dd17f730a58b6145cd003a7922c
- 39e0199d3d501acc3377af56c4e79ec4c4f8aaa21ac1a449fe8da69c4c267dd7
- f8ef5f403474624e61ef0b83adc9e15ea6ca47534f7316c4c43db6f064e21c76
- a544293ad41861129c77aaaea1620b884982378721bed31c60702b3e3d3c1590
- 87d809543079ae5770b6cdc1849e7be55dec1a37c3f90ea63a5d5f5a2b3d4c32
- 594948597aae36cd9fcf30dec7ef1be70bc70ee618f0e33dd8268c12982da7c9
SHA-1
- 866f1c5e47a013c452b13509a3a7f2947e8b10b8
- c90e77f22b509dd26442571c2a46f03551bf3ae0
- 26564ab151f4a682be4b0a7a224caf9f12b4cc3c
- cae2c3563f0af1427f3315e9db4bdedf97d905e1
- db1fccbe1b99ee81abd0efdeaf8dfd53d8cc728e
- 5ace393d64e9793c900047b0f9946c1396470946
- 22c6a8cbd27e92788a60f6a0639ad222992ea4b7
- 7070d5970f1d13c38cd306c80159e69c28ef2917
- b725dbfa2afdb74141c09eacaad341e5a727bbe7
- e942c4f4e836e2b92dfafb4ca1d4af456dff760b
- 59dba24dd4e1747fd5a844757cbe8172d68d2092
- 338105c31ae86bf704f224e228bd60228f6c10b5
- 2493c6a0ee1348c386ecce37ce862d40ab266ad7
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Ensure all operating systems and software are up to date with the latest security patches.
- Employ reliable antivirus and antimalware software to detect and block known threats.
- Regularly update these tools to maintain the latest threat intelligence.
- Implement IDPS to detect and prevent unusual network activity, system behavior, or similar threats.
- Enable two-factor authentication (2FA) on your accounts adds an extra layer of security and can help prevent unauthorized access even if your login credentials have been stolen.
- Regularly backing up your important data can help ensure that you don’t lose any critical information in the event of a malware infection or other data loss event.
- Be wary of emails, attachments, and links from unknown sources. Also, avoid downloading software from untrusted sources or clicking on suspicious ads or pop-ups.
- Use email filtering solutions to block malicious attachments and links that may deliver malware to users via phishing emails.
- Segment your network to limit lateral movement for attackers.
- Employ application whitelisting to only allow approved software to run on systems, reducing the risk of unauthorized applications being executed.
- Implement robust monitoring solutions to detect any unusual or suspicious activities, such as unauthorized access attempts or data exfiltration. Establish an effective incident response plan to respond to and mitigate any potential breaches quickly.
- Make sure all of your software, including your operating system and applications, is up-to-date with the latest security patches. This can help prevent vulnerabilities that info-stealers and other types of malware could exploit.

