Severity
High
Analysis Summary
Researchers have reported a new variant of the Mallox ransomware (also known as TargetCompany, Mawahelper, and Fargo) which is now targeting Linux systems.
Unlike its previous iterations, which spread via .DLL, .EXE, or .NET-based files on compromised Windows MS-SQL servers, this updated version is delivered through a custom Python script. The ransomware employs the robust AES-256 CBC algorithm for encryption, enhancing its ability to secure and lock data, and includes functionalities for user authentication, login, password reset, and other tasks.
Detailed analysis by researchers revealed that the Python script uses the Flask framework to create a web panel facilitating the development of custom Mallox variants. This web panel also manages deployment and enables the downloading of ransomware, making it easier for cybercriminals to customize and distribute their malicious payloads. This development signifies a sophisticated approach to ransomware's evolution, leveraging popular frameworks and encryption methods to enhance its efficacy.
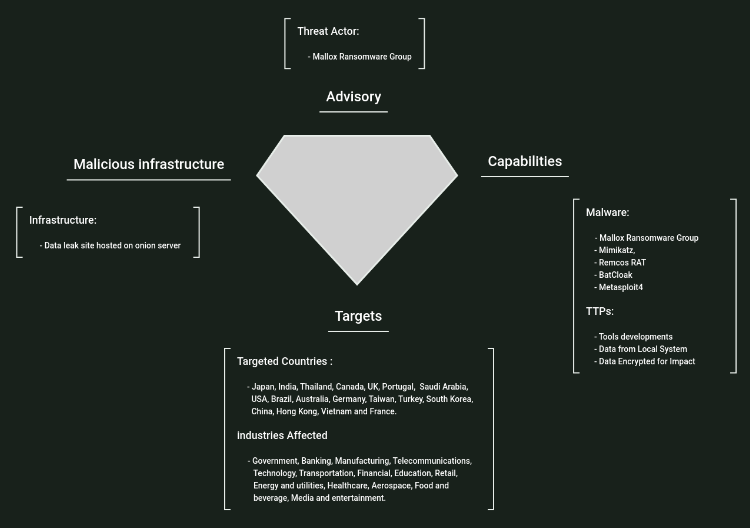
The discovery of a Mallox ransomware decryptor by researchers indicates ongoing updates and improvements to the ransomware. This poses a continuous threat to organizations, as the ransomware can adapt and evolve, complicating defensive measures. The presence of a decryptor suggests that there may be a way to recover encrypted data, but it also underscores the need for robust preventive strategies to mitigate the risk of infection in the first place.
Organizations are urged to defend against this threat by implementing regular data backups, ensuring software is up-to-date, and maintaining heightened vigilance against suspicious links and attachments. These measures are crucial in preventing ransomware infections and mitigating the impact if an attack occurs. By adopting proactive cybersecurity practices, organizations can better protect their systems from the evolving threat of Mallox ransomware.
Impact
- Data Encryption
- Financial Loss
- Sensitive Data Theft
Indicators of Compromise
IP
- 185.73.125.6
- 91.215.85.142
- 91.215.85.135
MD5
- 3dde1507996cf8c3dd53a726501be33b
- 231478ff24055d5cdb5fbec36060c8ff
- 779aa15cd6a8d416e7f722331d87f47b
SHA-256
- e1d8095b39af0901618fa2b0d2f620d391f167045f6d2e61efca6797f5a322fd
- 9f4c40c0d52291334d90455a64106f920ede3bda5c3f7d00b0933032b0f208d8
- 23ba8078df63ebb313f2f2a2f24dab840e068ddd5cc54bb661db7d010954d2fc
SHA-1
- 07407eed403504e4c4890805ff2ea680061b0d97
- a1a8922702ffa8c74aba9782cca90c939dfb15bf
- 9050419cbecc88be7a06ea823e270db16f47c1ea
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Implement robust multi-layered security measures to detect and respond to ransomware and cyber espionage activities.
- Conduct regular security assessments and penetration testing to identify and mitigate vulnerabilities in critical infrastructure and government systems.
- Deploy advanced threat detection tools, such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (NTA), to monitor for suspicious activities and anomalies.
- Ensure timely patching and updating of all software and systems to close known security gaps.
- Use multi-factor authentication (MFA) and strong password policies to protect user accounts from unauthorized access.
- Segment networks to limit lateral movement within the organization in case of a breach.
- Develop and maintain an incident response plan that includes procedures for ransomware attacks and data breaches.
- Train employees on cybersecurity best practices and phishing awareness to reduce the risk of social engineering attacks.
- Regularly back up critical data and ensure backups are stored securely and are not accessible from the primary network.
- Collaborate with cybersecurity firms and government agencies for threat intelligence sharing and coordinated defense strategies.
- Implement encryption for sensitive data at rest and in transit to protect against data theft.
- Limit access to critical systems and data to only those individuals who require it for their role.
- Monitor for and immediately investigate the presence of known malware and indicators of compromise associated with state-sponsored groups.
- Engage in regular cybersecurity drills and exercises to ensure readiness for potential cyber incidents.
- Ensure legal and compliance measures are in place, particularly for industries subject to specific regulatory requirements.

