Severity
High
Analysis Summary
Cybersecurity researchers have revealed a previously undocumented macOS variant of the LightSpy spyware which was earlier identified as targeting iOS users. The LightSpy attack on macOS begins by exploiting a Safari WebKit flaw via rogue HTML pages leading to the delivery of a Mach-O binary disguised as a PNG image.
This binary extracts and launches a shell script that fetches three additional payloads: a privilege escalation exploit, an encryption/decryption utility, and a ZIP archive. These payloads set up persistence and root privileges on the infected device, allowing the spyware's core component to connect to a command-and-control (C2) server to retrieve commands and download plugins. These plugins enable various espionage activities such as capturing audio taking photos, recording screen activity, harvesting files, and extracting data from web browsers and iCloud Keychain.
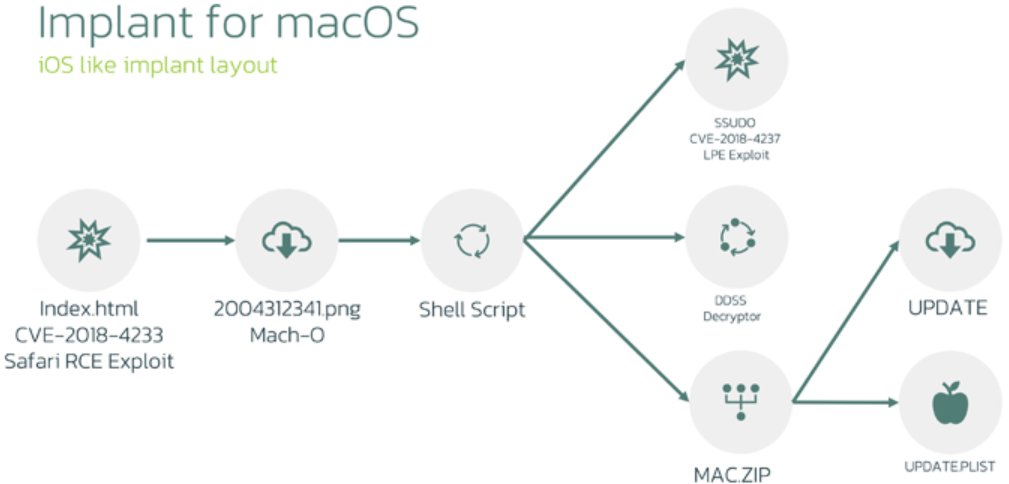
The analysis by researchers indicates that LightSpy is a cross-platform malware framework capable of infecting iOS, Android, Windows, macOS, Linux, and various routers. The macOS variant exploits two known vulnerabilities (CVE-2018-4233 and CVE-2018-4404) with parts of the latter likely derived from the Metasploit framework. This variant, active since at least January 2024, has been found on about 20 test devices, though its presence on VirusTotal from India does not necessarily indicate an active campaign in that region.
Additionally, the macOS version of LightSpy includes plugins for network discovery, capturing details about nearby Wi-Fi networks, and identifying other devices connected to the same network. Researchers uncovered a misconfiguration in the C2 panel, granting them access to the remote control platform which contains victim information and data. The threat actor group behind LightSpy appears focused on intercepting communications including messenger conversations and voice recordings and has designed specialized plugins for network discovery and proximity device identification.
The disclosure of the macOS variant comes amid broader concerns over spyware targeting various devices. Recent reports have highlighted Android devices being attacked with banking trojans like BankBot and SpyNote as well as Pegasus spyware targeting journalists and activists in Eastern Europe. Pegasus-maker NSO Group stated it only sells its tools to countries allied with Israel and the U.S. and promised to investigate and possibly terminate customer service if misuse is found.
Impact
- Data Theft
- Privilege Escalation
- Cyber Espionage
- File Encryption
Indicators of Compromise
IP
- 103.27.109.217
MD5
- 2ab41a8e6f4004a6237ad8dd19ea8efe
- d190774187353dbb332a0edc4754ad50
- b737dc726c253498a2e38288406a2ba1
- 4946041110628757ea259d0551c0775f
- b6938b27b999a7975969ae0881429b89
- 1cfa3984397d865fefad42a6d2ab2415
- 0cc533b1834c443df3f78411a618e4eb
- 8c76773e309cf62c2a67ddc6e3abe552
- d6fabf405d8657650278729e5e8b941e
- 770d80c6862ce2057c3d3fd387deb059
- 2178d673779605ffb9cf7f2fa3ec8e97
- 59ac7dd41dca19a25a78a242e93a7ded
SHA-256
- 8a4f8a755ca123e9c3aa77b525f59ce99f1f2e288afc2e29afb6d15573776a16
- 4cbc70b1c7d4ccc593fad895299e88a6734c8f4687f37f43850996f7fa076df9
- 4e7c9bd8c623d7de9dc225fbdc9305f32c961f473acb99256012ccf6d45ba494
- 2c2471150aacc8443aa92a6063a848e8bb9dbcc8e369fb378c003d98bceaa728
- 9b58e3a82b14e329dab6108a5f25d20edd50cac95072dac420c94718ed8c1764
- 1d499c401d8854b6331d3b531fc57418dd2b132861e0448ae198dcbea41484ab
- ff4332365b1628f88bc84bec102b534e5a6e9a32b2fc61dd43c951a338f976d8
- 85a2dd209cacb9628d160bf76b09a87d8f1bd39093cb365154e7d35810da7ca0
- 65dee715b928f07da356e8bce7a762b0ab4c140ebea63e4bd66c2eb85e0fa2dc
- 87cd75344a6826feac6d21b053f6816700b4b349ffd397addb4e244633edcc42
- 4b973335755bd8d48f34081b6d1bea9ed18ac1f68879d4b0a9211bbab8fa5ff4
- 0f66a4daba647486d2c9d838592cba298df2dbf38f2008b6571af8a562bc306c
SHA-1
- 8ab8c77a590a6d536286a5394453926c119c8b5f
- 25ca7f7c8d21f6e5f6806addff96dffb19f1b1a7
- b3ce5539662abe1ee7d667220662f7ffd372be06
- 8c744406d63d775057156a93681672101381358e
- fe7ae508de0b108bdcd06bcaa876e16cf921aa75
- 0f8f6fe87e57824dee9dd50c3ec98b2e06e47c62
- 95c7083eccdd62f841970f06748e9a5ee4729ef3
- 57e51edebe26dade3e004cd607cab70e2902843d
- 25fd671fbcc8483b876ec1f091e87aaa441c8181
- db0caed70d90646565cefdcdcdb8a226a7e327d5
- afd03337d1500d6af9bc447bd900df26786ea4a4
- fd49866245721acc6e7431ec61b066696b72a1e1
Remediation
- Block all threat indicators at your respective controls.
- Search for indicators of compromise (IOCs) in your environment utilizing your respective security controls.
- Only download apps from official app stores (Google Play Store and Apple App Store) and avoid third-party app sources.
- Review the permissions an app requests during installation. If an app asks for excessive permissions that are unrelated to its functionality, consider it a red flag.
- Never trust or open links and attachments received from unknown sources/senders.
- Encourage individuals to report any suspicious activities, emails, or messages to relevant authorities, organizations, or cybersecurity experts.
- Verify the authenticity of websites, social media profiles, and apps before providing personal information or engaging with them.
- Implement strong, multi-factor authentication (MFA) for email accounts, social media profiles, and other sensitive online services.
- Keep all software and operating systems up to date with the latest security patches to minimize vulnerabilities.
- Employ robust network security measures, including firewalls and intrusion detection systems, to detect and block malicious network traffic.
- Develop and maintain an incident response plan that outlines steps to take in case of a security breach. Ensure that individuals and organizations know how to respond effectively.
- Maintain cyber hygiene by updating your anti-virus software and implementing a patch management lifecycle.
- Refrain from downloading apps from unofficial sources or third-party app stores. These sources are less regulated and more prone to hosting malicious apps.
- Patch and upgrade any platforms and software timely and make it into a standard security policy. Prioritize patching known exploited vulnerabilities and zero-days.
- Enable antivirus and anti-malware software and update signature definitions promptly. Using a multi-layered protection is necessary to secure vulnerable assets.


